DNS was designed over 30 years ago, back when security wasn't a primary focus of the internet. Without extra protection, it's possible for MITM attackers to spoof records and lead users to phishing sites. DNSSEC puts a stop to that, and it's easy to turn on.
DNS by Itself Is Not Secure
The DNS system includes no built-in methods to verify that the response to the request was not forged, or that any other part of the process wasn't interrupted by an attacker. This is an issue because whenever a user wants to connect to your website, they have to make a DNS lookup to translate your domain name into a usable IP address. If the user is connecting from an insecure place, like a coffee shop, it's possible for malicious attackers to sit in the middle and spoof DNS records. This attack could allow them to redirect users to a malicious page by modifying the IP address A record.
Luckily, there's a solution---DNSSEC, also known as DNS Security Extensions, fixes these issues. It secures DNS lookups by signing your DNS records using public keys. With DNSSEC enabled, if the user gets back a malicious response, their browser can detect that. The attackers do not have the private key used to sign the legitimate records, and can no longer pass off a forgery.
DNSSEC's signing of keys goes all the way up the chain. When you connect to
example.com
, your browser first connects to the DNS root zone, managed by IANA, then to the directory for the extension (
.com
, for example), then to the nameservers for your domain. When you connect to the DNS root zone, your browser will check the root zone signing key managed by IANA to verify that it is correct, then the
.com
directory signing key (signed by the root zone), then the signing key for your site, which is signed by the
.com
directory and cannot be forged.
It's worth noting that in the near future, this won't be as much of a problem. DNS is being moved over to HTTPS, which will secure it against all kinds of MITM attacks, make DNSSEC unnecessary, and also prevent ISPs from spying on your browsing history---which explains why Comcast is lobbying against it. As it stands though, it's an optional feature in Chrome and Firefox (with operating system support coming in Windows soon), so you'll still want to enable DNSSEC in the meantime.
How to Enable DNSSEC
If you're running a website, especially one that handles user data, you'll want to turn on DNSSEC to prevent any DNS attack vectors. There's no downside to it, unless your DNS provider only offers it as a "premium" feature, like GoDaddy does. In which case, we recommend moving to a proper DNS provider, like Google DNS, who won't nickel-and-dime you for basic security. You can read our guide to using it here, or read more about transferring your domain.
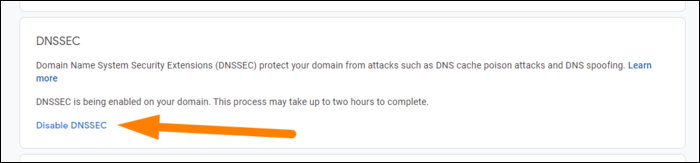
If you're using Google Domains, setup is literally just one button, found in the domain console under "DNS" in the sidebar. Check "Enable DNSSEC." This will take a few hours to complete and sign all the required keys. Google Domains also fully supports DNS over HTTPS, so users who have that enabled will be entirely secure.
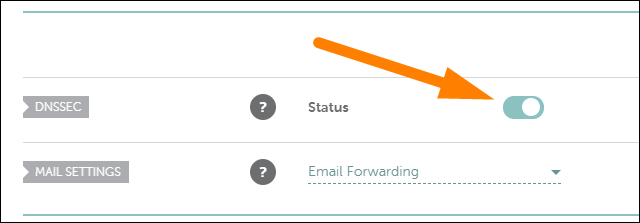
For Namecheap, this option is also just a toggle under "Advanced DNS" in the domain settings, and is entirely free:
If you're using AWS Route 53, it, unfortunately, does not support DNSSEC. This is a necessary downside to the elastic DNS features that make it great in the first place: features like Alias records, DNS level load balancing, health checks, and latency-based routing. Because Route 53 can't reasonably sign these records every single time they change, DNSSEC is not possible. However, if you're using your own nameservers or a different DNS provider, it's still possible to enable DNSSEC for domains registered using Route 53---just not domains using Route 53 as their DNS service.