Quick Links
Firewalls are crucial for any server's security. Only allowing the right traffic through to the right resource prevents malicious traffic and potential attacks from taking advantage of your unprotected server. DigitalOcean offers virtual machines, known as Droplets, which come with their own firewall system configuration, monitoring, and maintenance benefits over traditional OS-level firewalls.
The firewall system is called Cloud Firewalls. It is a networking-level firewall that drops the traffic that you do not want to make it to your Droplet, and therefore the potentially malicious traffic will never reach your server. Some of the features of Cloud Firewalls are:
- Inbound and Outbound Stateful Firewalls
- Named services, such as SSH, HTTP(S), MySQL, etc.
- Custom ports
- Port ranges
- Limit by sources, such as Droplets, Load Balancers, VPCs, Tags, or specific IPv4 or IPv6 CIDR addresses
Recently, DigitalOcean released Virtual Private Cloud (VPC) networks. By defining a collection of resources into a VPC, all traffic is kept internal to that network, even from other VPC networks. Cloud Firewalls work in conjunction with VPCs to further segment and protect traffic. For this article, we are going to use two virtual machines configured in the following manor:
- OS: Ubuntu 18.04.3 LTS x64
- Pricing: Basic VM at $5/mo
- Region: SFO2 Region
- Authentication: SSH Keys
-
Tags:
testubuntu
Create a Cloud Firewall
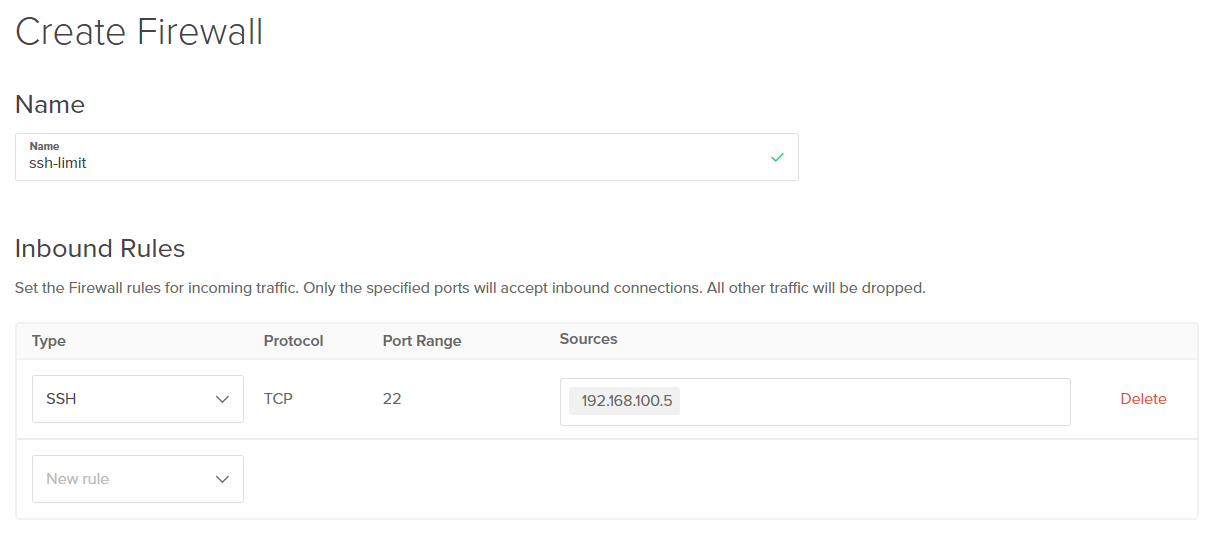
After creating a Linux VM, one of the first tasks is protecting the SSH service, as this is often a prime target of malicious actors. Let's create a simple and easy-to-use firewall that will limit SSH to our newly created VM by just the IP that we designate.
In this example, it will be the IP address
192.168.100.5
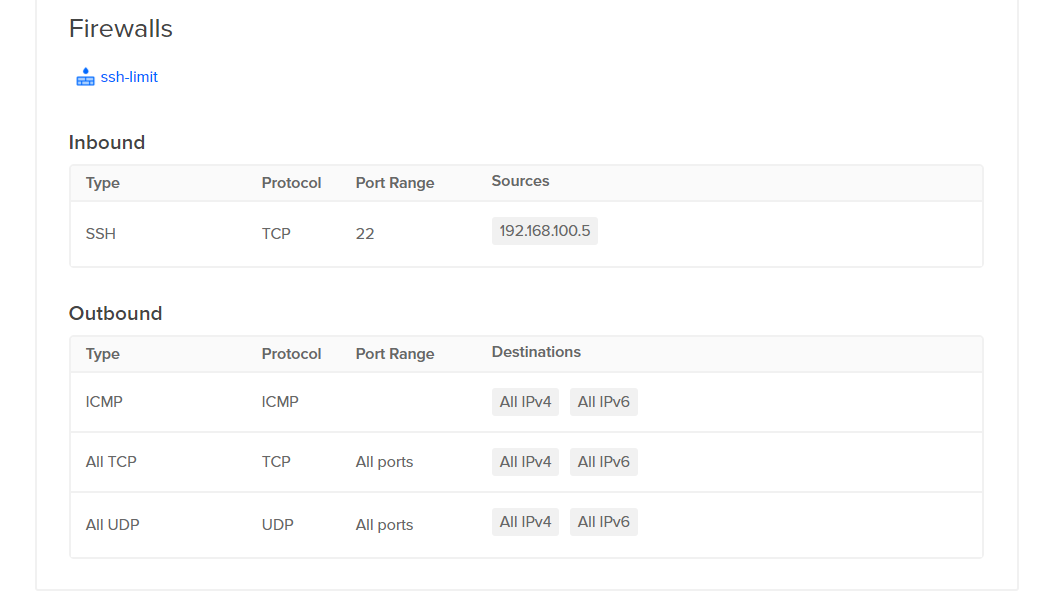
. After clicking on "Create Firewall," we are presented with a form asking for the Name, Inbound Rules, Outbound Rules, and the resource to apply the firewall to.
-
Name:
ssh-limit -
Inbound Rules
-
SSH →
192.168.100.5
-
SSH →
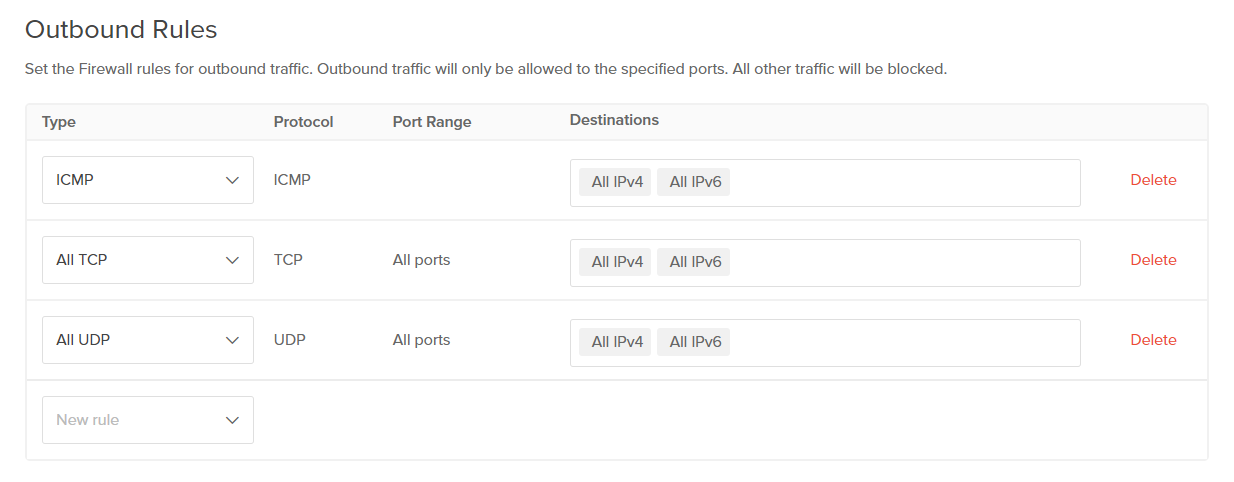
Next, let's take a look at the Outbound Rules. What you see below are the default rules. What this is saying is that all TCP/UDP outbound traffic is allowed to all locations, as is ICMP traffic. Generally, this is okay, depending on your needs. Most server administrators have a higher level of control on the outbound traffic rather than the inbound. That being said, you can certainly limit this traffic.
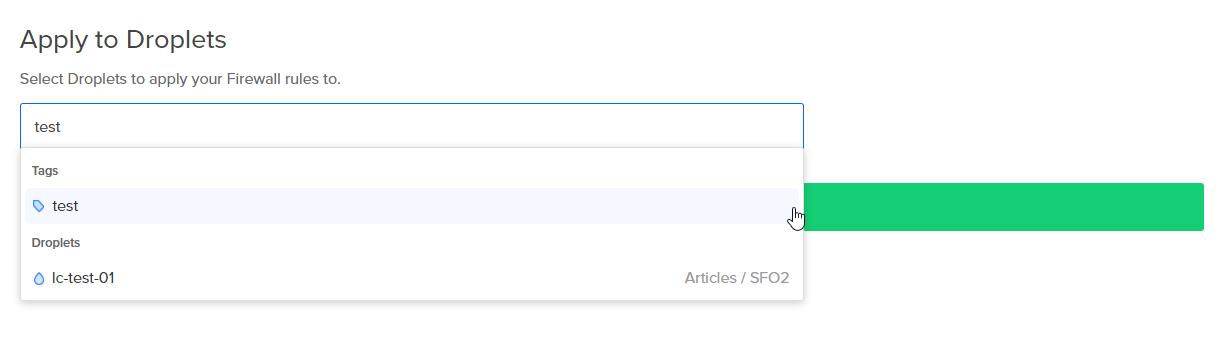
Finally, let's apply this new firewall to a newly created VM that we have tagged
test
. Why apply the firewall to a tag rather than the Droplet itself? By applying to a tag, this firewall will automatically apply to every new resource that is tagged appropriately. It automates the configuration and means that important firewall configurations will not be missed.
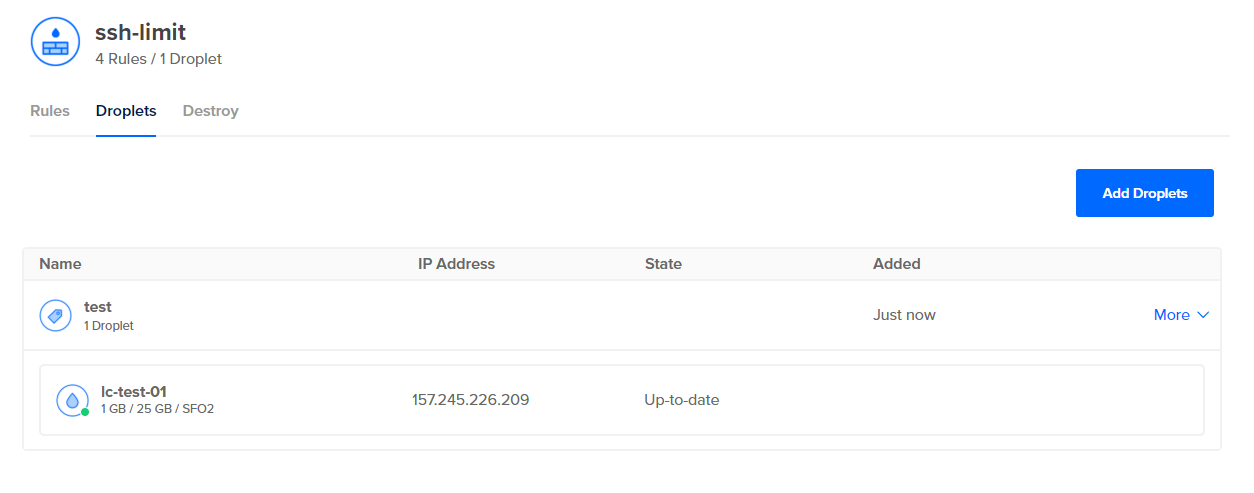
After creation, you can see that the firewall is properly applied to the Droplet, and will now drop all traffic that doesn't fit that pattern, before the traffic makes it to the Droplet.
Provisioning a New Droplet
What happens then when we provision a new Droplet and tag that VM with the
test
tag? After provisioning a new VM and navigating to the networking section of the droplet, you can see that the
ssh-limit
firewall that we previously created is automatically applied.
Limiting Internal VPC Traffic
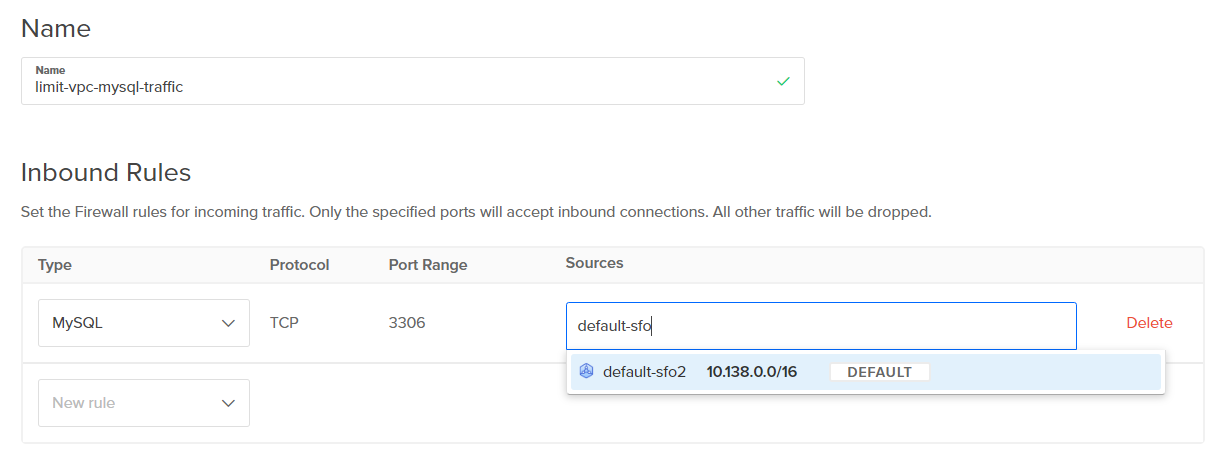
What if we have MySQL databases on our two Droplets that have been provisioned, and we would like to ensure that the traffic doesn't leak beyond these resources? To make sure that port 3306 (MySQL) traffic is only allowed from other resources within the VPC, a cloud firewall rule can actually be applied to the VPC traffic range.
If you use the Managed Databases product from DigitalOcean, such as a MySQL, PostGres, or Redis databases, this ability makes it easy to protect those resources as well. The ideal setup would be to contain all relevant resources in a VPC, then use Cloud Firewalls to properly protect the traffic between the different resources.
Cloud Firewall Caveats
You shoudl be aware of a couple of items when using Cloud Firewalls. Some of these are quantity limits on Cloud Firewalls, and others are product limitations that may affect how you use Cloud Firewalls.
- There is a maximum of 10 individually added droplets to any given firewall.
- There is a maximum of 5 tags that can be added to a given firewall, but by using tags you can get around the 10 individual droplet rule (i.e., a tag with 50 droplets will still work with the firewall).
- A firewall can have a total of 50 combined incoming and outgoing rules.
- Firewalls only support ICMP, TCP, and UDP traffic at this time.
- Traffic logs won't be available for the dropped traffic because this happens at the network level.
Conclusion
Although this is just an overview of the functionality and rules that can be defined for DigitalOcean Droplets, the combination of a network-level firewall and VPC networks can easily protect your Droplets from malicious traffic. With the low cost of low-powered droplets and the ease of configuration, one can quickly see how to use Cloud Firewalls to protect their server resources.