Google Cloud Platform is a competitor to AWS that makes running virtualized servers easy and cheap. Unfortunately for beginners, they have a novel approach to setting up SSH that requires some explanation and setup.
Quick SSH Access: Use the Console
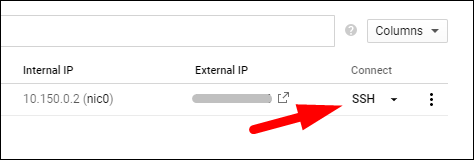
If you need quick access, the simplest method is to click "SSH" from the GCP Compute Engine console. This will bring up a new Chrome window that will transfer keys and connect you to the instance.
This is provided because setting up SSH for a third-party client is a bit more involved than you'd expect. For other cloud providers like AWS, you'd select a private key pair, download that key pair, and connect to the instance as normal using
ssh -i keyfile
.
However, GCP decides to manage SSH keys using IAM roles and permissions. Rather than downloading a private key for the instance, you instead provide your key to your user account, and provide your key to the instance by setting up OS Login.
Of course, you can always manually add your SSH key to the
authorized_keys
file, which will solve the issue, but Google has set up OS Login for a reason, and it's better to manage it this way rather than manually overriding the key management tools they've set in place.
Setting Up Your Own Keys With OS Login
The first step to setting up OS Login is to add your SSH keys to your user account. If you're managing access for other people, you can use the Directory API, but if you're linking your own account, you'll want to use the
gcloud
CLI.
Download the installer and run it. The installer will open a new window allowing you to sign in to the Google account you wish to add the keys to. Once it's done, run the following command in your terminal to add
~/.ssh/id_rsa.pub
to your account's keys:
gcloud compute os-login ssh-keys add
--key-file ~/.ssh/id_rsa.pub
--ttl 0
OS Login is disabled by default, so you'll need to enable it either project-wide or for specific instances. Under "Metadata" in the Compute Engine Console, add a new key pair with enable-oslogin as the key and TRUE as the value.
If your account is an IAM administrator, you should now be able to connect to any instances with OS Login turned on, using the private key you linked with your account.
However, if your account isn't the owner, you'll need a few IAM Permissions enabled to be able to access the instance:
-
roles/compute.osAdminLogin, which grants administrator permissions, or -
roles/compute.osLogin, which does not grant administrator permissions.
You can set either of these permissions at the instance level using IAM policy bindings.
Any new instances you create will automatically be accessible using the private key linked to your account, with no manual configuration required. If you're giving out access to other users and need to revoke it in the future, you can simply revoke their IAM permissions, which will solve the issue without requiring a key rotations.