Quick Links
Kubescape is a new open-source tool from ARMO which lets you automate Kubernetes cluster scans to identify security issues. Kubescape audits your cluster against the hardening recommendations published by the NSA and CISA.
Here's how to install Kubescape and get started scanning your cluster. Regular scans could help you resolve issues before they're utilized by attackers.
Downloading Kubescape
Kubescape is currently distributed as a pre-built binary for Windows, macOS and Ubuntu. You can download it directly from the project's GitHub releases page.
There's also an automated install script that you can paste into your terminal. This will fetch the correct binary for your system and add it to your path.
curl -s https://raw.githubusercontent.com/armosec/kubescape/master/install.sh | /bin/bash
Try running kubescape to check installation is complete. You'll see a synopsis of the available commands.
Scanning Your Cluster
Kubernetes connects to your cluster using standard Kubectl config files. Set the KUBECONFIG environment variable in your shell to reference the config file for the cluster you want to scan:
export KUBECONFIG=.kube/my-cluster.yaml
Kubescape will complain that it "failed to load Kubernetes config" if this variable's not set or the specified file is invalid. Update the KUBECONFIG variable each time you execute Kubescape if you want to scan multiple clusters.
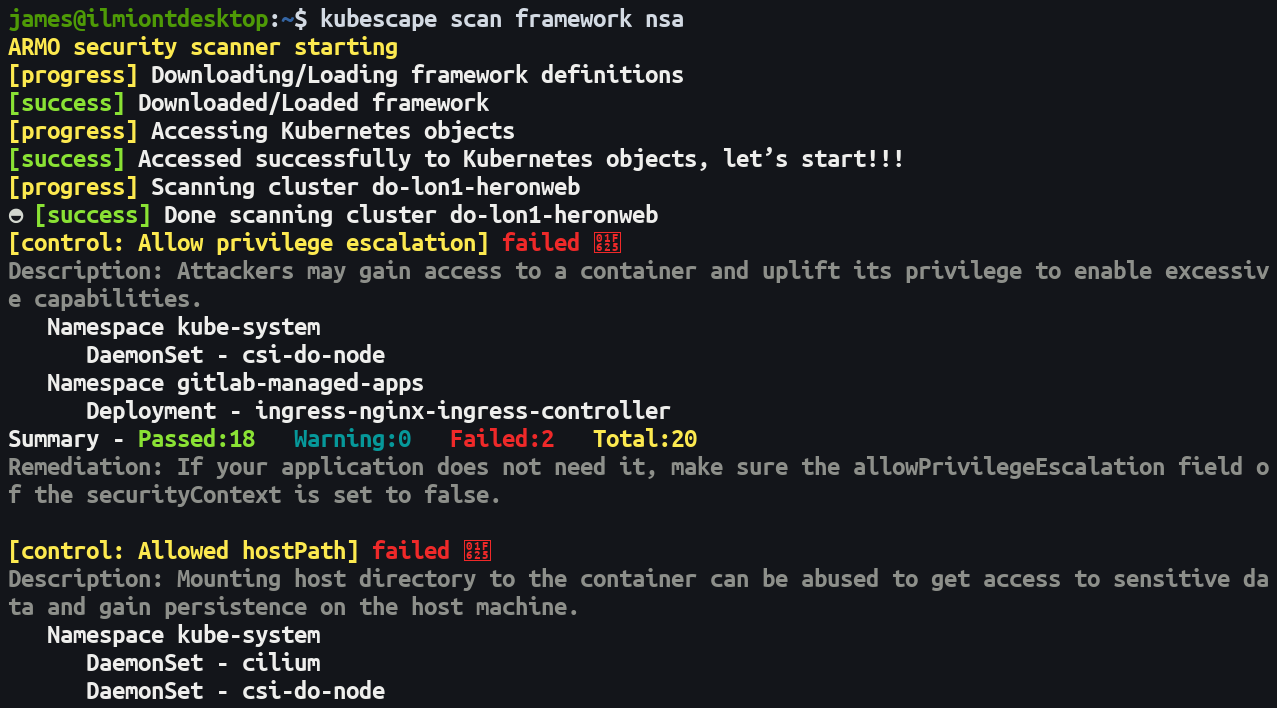
Scans are initiated with the scan command. You need to indicate the hardening framework you want to scan against. Currently nsa is the only supported option.
kubescape scan framework nsa --exclude-namespaces kube-system,kube-public
Kubescape will scan all the resources in your cluster, except for resources in namespaces omitted by the --exclude-namespaces flag. It's recommended you list the built-in Kubernetes namespaces here as you won't be able to address any issues which are found.
Your first Kubescape scan might take some time as the tool needs to download its framework definitions. These define the tests your cluster is scored against. Once the scan's complete, you'll see colorized output in your terminal that details any discovered issues.
Scan Results
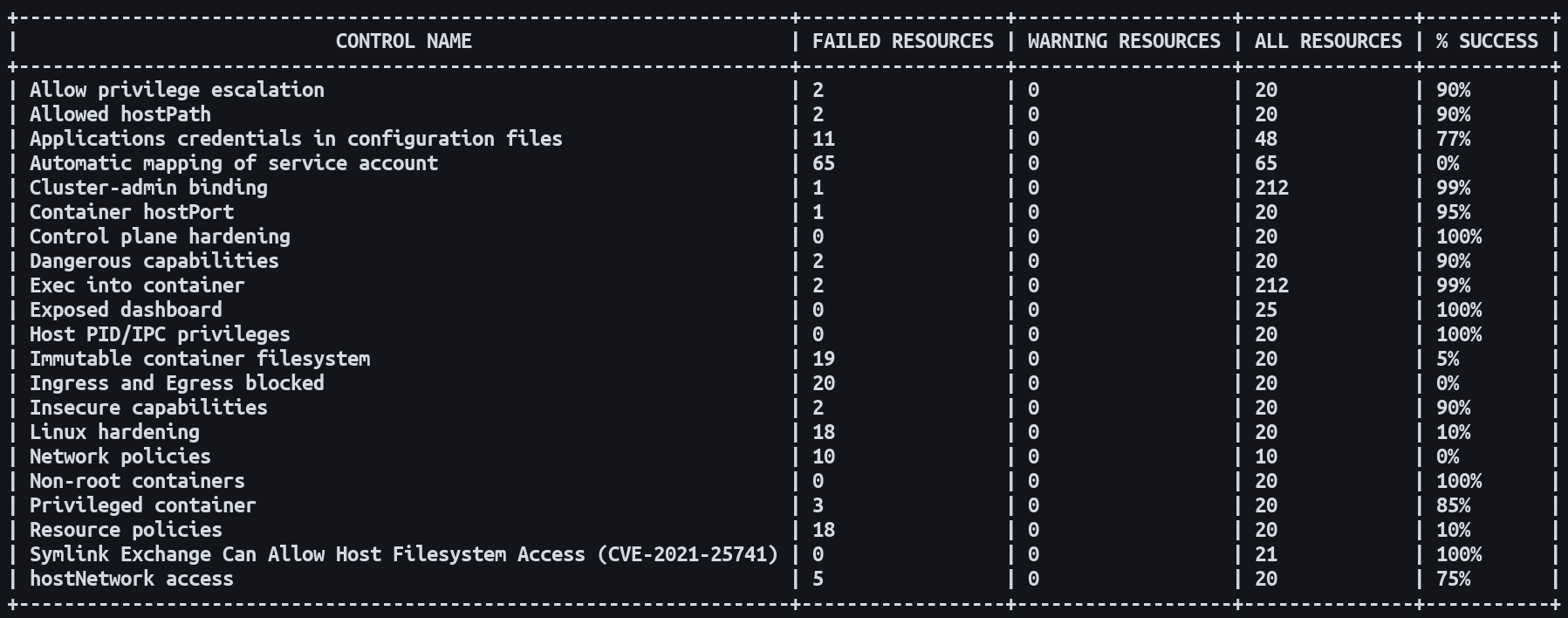
Each failed test produces its own section of output with a list of the suspect resources, a description of the problem, and a remediation hint. A table at the bottom of the report provides a summary of all the executed tests, the number of resources that failed them, and the overall success percentage.
Kubescape checks over 20 possible weaknesses based on the NSA-identified list. The NSA's report provides a description of the covered issues and the rationale for their inclusion. Some of the key problems which Kubescape checks for include:
- Privilege escalation opportunities
- Containers running in privileged mode
- Containers running with dangerous capabilities
- Exposed Kubernetes Dashboard
-
Containers running as
root - Credentials contained in configuration files
- Incorrectly secured control plane
Running Kubescape lets you check your cluster's health against the current best practice guidelines, giving you more confidence that you're not putting your data and workloads at risk.
Scanning Manifest Files
Kubescape can work without a cluster connection. You can scan resource manifests stored as local YAML files, letting you check their security before you apply them to your cluster. Add an extra argument after the framework name to specify the files you want to scan:
kubescape scan framework nsa k8s/*.yaml
You can use a URL as the file path to scan files stored remotely, such as in a Git repository.
It's best to use the default cluster scanning mode when you're conducting a comprehensive security audit. Manifest scans are ideally incorporated into CI pipelines. Used in this way, you can avoid unintentionally introducing new vulnerabilities as you update your resources and roll them out to your cluster.
Offline Scans
Kubescape is designed for online use as it needs to download the framework definitions before it can complete a scan. You can manually save the framework though to facilitate offline scans. You should try to update the file periodically so it doesn't become outdated.
Download the NSA framework file:
kubescape download framework nsa --output nsa.json
Now scan your cluster using the downloaded file:
kubescape scan framework nsa --use-from nsa.json
The --use-from flag instructs Kubescape to load framework definitions from the specified file. There's also --use-default which will try to use the locally cached file in the default location when it's available. Kubescape falls back to downloading the latest definitions from the server when no file is found.
Output Formats
Kubescape outputs to your terminal by default but can also produce reports in JSON or Junit format. Add the -f flag to specify your desired mode:
kubescape scan framework nsa -f json
kubescape scan framework nsa -f junit
The latter option emits an XML file which can be consumed by test report tools that work with the Junit format. This lets you feed Kubescape scans into your existing test reporting solutions for visualization and aggregation.
Output is emitted to your terminal's standard output stream irrespective of the report format you specify. Add the -o flag to supply a file path to save to:
kubescape scan framework nsa -f json -o report.json
Kubescape's usual progress messages can be disabled with the -s flag. This is helpful in CI scenarios where you don't want to pollute job logs with ASCII characters.
Conclusion
Kubescape lets you assess the safety of your Kubernetes clusters against the guidelines published by the NSA. The simple open-source tool provides a single command to benchmark your environment against over 20 key checks.
Kubescape doesn't check for vulnerabilities inside the containers you run in your cluster. You'll need another tool such as docker scan or Trivy to do that. Running a container scanning engine alongside Kubescape gives you the most complete picture of your environment's security posture.