Quick Links
phpMyAdmin is a great tool for managing a MySQL database, but putting access to your database behind a web interface is an major security problem. Here are a few ways to mitigate the risks involved with runing phpMyAdmin.
Why Is phpMyAdmin a Security Problem?
Usually, you'd have a database that would run on your server and only accept connections from
localhost
or maybe from another trusted server. If you had an application also running on that server, it would communicate directly. There's no way for an attacker to gain access short of cracking into the whole server.
phpMyAdmin circumvents this to provide you a web interface for managing your database. It's a very useful tool, but it's a disaster for security. phpMyAdmin has full unrestricted access to your database, as it's intended to replace command line direct access. If an attacker gains access to the web panel, they'll have access to everything. And phpMyAdmin is usually only secured with a simple password.
Install phpMyAdmin and Secure MySQL
phpMyAdmin runs on the LAMP stack (Linux, Apache, MySQL, PHP). Before you even start installing phpMyAdmin, your instance of MySQL should be secure. MySQL provides a handy utility for performing some basic security tasks:
sudo mysql_secure_installation
This will walk you through changing the root password, disabling remote logins, and removing the test database.
After that, you can install phpMyAdmin as usual. During the install, you'll be prompted for a password of the database's admin user (which you should have set during mysql_secure_installation), and a new password to secure phpMyAdmin with. Make sure this password is long and secure, as it's the final point of defense before attackers could gain access.
Ideally though, no attacker should even get a chance to guess your password, so you'll want to put phpMyAdmin behind something else so you can secure it further.
Option 1: Lock Down Apache, and Use SSH Port Forwarding
This is the most secure option, but it is only really suitable for single-user access, particularly for single users that have full administrative access to the whole server, as it requires you to connect over SSH.
SSH port forwarding is a method of forwarding local ports to a remote system. For example, you would have Apache running on your server, listening on port 80. If you tunneled that port, you could access it by going to:
https://localhost:80/
...in any web browser. In a sense, it's almost like Apache is running on your system. But port 80 doesn't have to be open on your server; all traffic is routed through the standard port 22 used for SSH. You'll need to make sure SSH is secured with SSH keys, and ideally not running on the standard port, as this method is only as secure as your SSH connection is.
To do this, you'll need to bind Apache to localhost, and make sure it's not open to the internet. Open up /etc/apache2/ports.conf, and change the three listen statements to only listen on localhost (aka 127.0.0.1):
Listen 127.0.0.1:80
<IfModule ssl_module>
Listen 127.0.0.1:443
</IfModule>
<IfModule mod_gnutls>
Listen 127.0.0.1:443
</IfModule>
Restart Apache with:
sudo service apache2 restart
And phpMyAdmin should be inaccessible. This is expected. Once Apache is configured, you can tunnel port 80 using the following command:
ssh -L 80:localhost:80 user@server
Then, you can access phpMyAdmin from localhost:80 in any web browser. Meanwhile, your server can be configured with a strict firewall to disallow anything except SSH.
If ssh can't bind to port 80, try changing the first port to a different number and accessing it from there on localhost. It will still tunnel to port 80 on the remote machine. This connection is maintained until you exit ssh. If you want to run it in the background, use the -f flag.
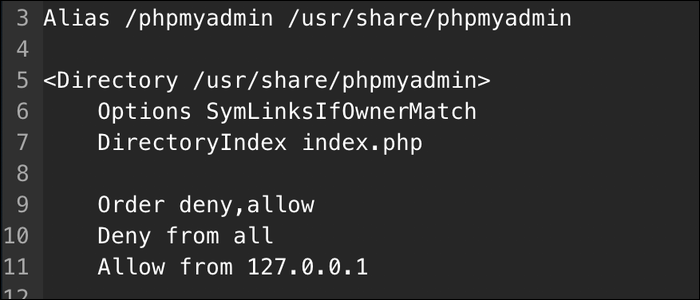
If you only want phpMyAdmin to listen on localhost, you can instead edit /etc/apache2/conf-enabled/phpmyadmin.conf and add the following lines to the Directory block:
Order deny,allow
Deny from all
Allow from 127.0.0.1
This will deny anything except localhost from accessing the phpMyAdmin install, although you will still need port 80 open in your firewall to allow regular traffic.
Option 2: Lock Down Apache, and Use a VPN
If you need to allow access to multiple people without giving SSH access, you can set up Apache to listen on your machine's private IP and only accept connections from the same cloud. This works particularly well with services like AWS VPC, where each server you launch is created in a virtual network.
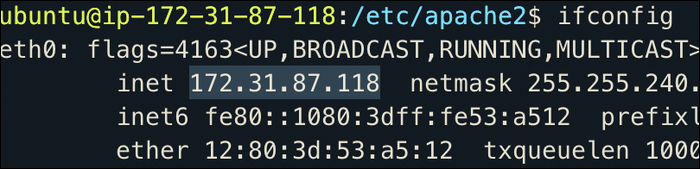
To find your private IP, you can run ifconfig and look for the inet address on your primary network adapter:
This address is also visible from the AWS EC2 Console. Once you have the address copied, open up /etc/apache2/ports.conf, and edit the three Listen directives to listen on the private IP:
Listen 172.31.87.118:8
<IfModule ssl_module>
Listen 172.31.87.118:443
</IfModule>
<IfModule mod_gnutls>
Listen 172.31.87.118:443
</IfModule>
Alternatively, if you just want to secure phpMyAdmin you can edit /etc/apache2/conf-enabled/phpmyadmin.conf and only allow from the private IP:
Order deny,allow
Deny from all
Allow from 172.31.87.118
And restart Apache.
Now, to access phpMyAdmin, you'll need to set up a VPN server like OpenVPN. This will allow you to tunnel your client computer to the virtual private cloud that your web servers are running in, and access the server running phpMyAdmin on the private IP as if you were another server. Of course, you'll need to configure your firewall settings to allow access from the OpenVPN server to the phpMyAdmin instance.
Option 3: Secure Apache with HTTPS and Basic Auth
If you really need to use public DNS and have your server accessible, you can use Basic authentication with Apache. This is simply another password in front of phpMyAdmin that prevents outsiders from making any requests to the phpMyAdmin application. You can use this alongside the other options on this list, as it's just an extra layer of defense.
Create a new password file with htpasswd, which should already be installed alongside Apache (if not, it's in apache2-utils):
sudo htpasswd /etc/apache2/.htpasswd phpadmin
This lets you set a new password for the user phpadmin and stores it in /etc/apache2/.htpasswd.
Open up /etc/apache2/conf-enabled/phpmyadmin.conf, and configure it to use Basic auth with the newly created password file:
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/apache2/.htpasswd
Require valid-user
Restart Apache with:
sudo service apache2 restart
And when you try to access phpMyAdmin in your browser, you'll be asked for a username and password. Enter phpadmin and the password you created, and you should be allowed access. Otherwise, all you'll see is a 401 Unauthorized response.