Quick Links
AWS provides an extensive CLI that provides access to every service they offer. You can use this on remote machines to give them access to certain features of your account, or on your personal computer to help administrate your infrastructure.
Install Python and pip
The AWS CLI runs on Python, so you'll need it installed along with its associated package manager, pip. There is a version for Python 2.6.5 and higher, and a separate version for Python 3.3 and higher. You'll probably want to install Python 3:
python3 --version
If you don't have it, you can download the latest release for Windows, or install it from your package manager on Linux:
sudo apt install python3.7
On macOS, Python 3 is available from brew.
pip is probably installed alongside Python, but if it isn't, you can download the install script:
curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
python3 get-pip.py
Install the AWS CLI From pip
Once Python is installed, you can download and install the AWS CLI from pip3:
pip3 install awscli --upgrade --user
Verify the install was successful with:
aws --version
If the command doesn't work, you may need to add the folder where Python is to your PATH:
ls -al $(which python3)
Configure the AWS CLI With an IAM User
IAM Users are the best way to manage account access in AWS. Rather than using your root account access key (which is dangerous, especially on remote servers), you instead create a new "user account" with the permissions to do the job it needs. For example, if you have a server that needs to upload content to S3, there's no reason to give it permission to spin up new EC2 instances, so you'd create a separate IAM user for that.
If you're just installing the AWS CLI on your personal computer, it's fine to give the IAM user full administrative access, as you'd have that anyway. AWS actually recommends this over using your root account for everything. Keep in mind though that if you've enabled two factor authentication for your AWS account, anyone with your administrator IAM access key can bypass your keyfob. But, these keys will be locked on your personal computer, so it's not a huge issue as long as you keep them secure.
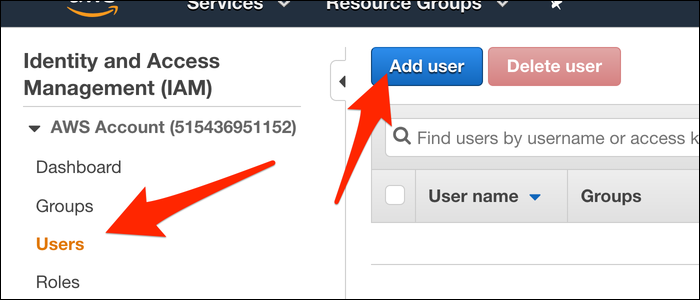
Head over to the IAM Management Console, and click on the "Users" tab. From here, add a new user for the CLI to use:
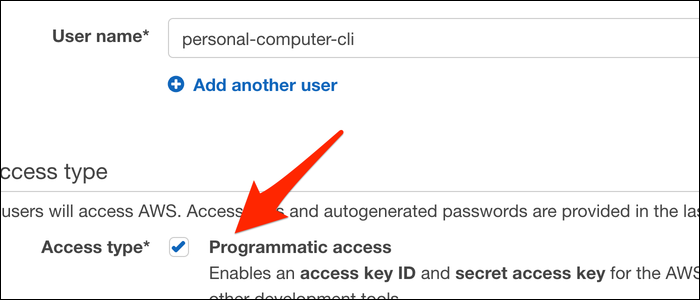
Give it a name, and make sure to set the access type to "Programmatic Access," which gives you the access key ID and secret access key the CLI needs to function.
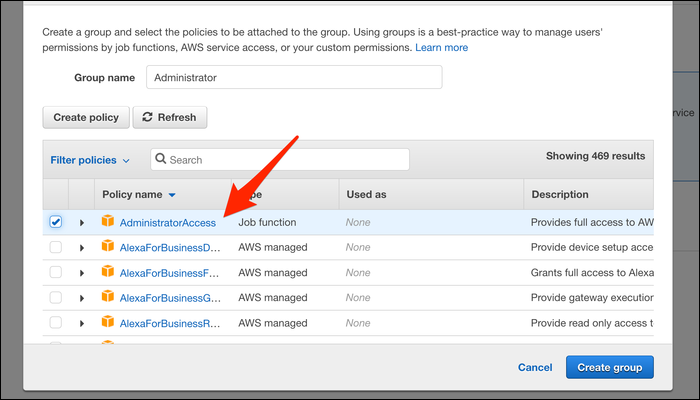
Click next, and you'll be asked to define the permissions for your IAM user. It's best to manage permissions with groups, so make a new group called "Administrator" and add the "AdministratorAccess" policy as a permission:
If you're setting up the AWS CLI on a remote machine, you'll instead want to manually enable the permissions necessary for that program to perform its task. AWS provides an extensive list of permissions controlling access to each service, and you can create your own permissions that can be much more specific.
Next, you'll be asked for tags. These are used to organize IAM users in larger organizations; you can skip this step or just write "admin" in one of them.
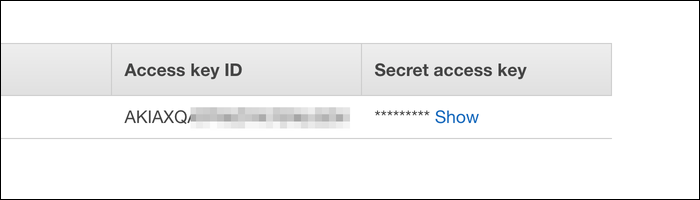
Click through to create your user, and you'll be brought to this screen showing your access key ID and secret access key:
You can download these as a .csv file for safekeeping, but keep the tab open so you can configure the CLI with this key.
Link the CLI to Your Account
Once your access key is ready to go, run the following command:
aws configure
You'll be asked for your access key ID and secret access key; paste these in.
You'll also be asked here for your default region name---you'll definitely want to set that here to prevent headaches from every command asking for a --region flag. Keep in mind that your region only includes the location and one number (e.g., "us-east-2") and not a trailing letter included in the availability zone ID (e.g., "us-east-2c"). Commands will fail if this is not set correctly, but you can always re-run aws configure to set it again in the future.
Once your account is linked, you're all set, and ready to use the AWS CLI. Verify that it's linked properly by listing your EC2 instances:
aws ec2 describe-instances
This should output a JSON array listing every EC2 instance you have running. The AWS CLI outputs a lot of JSON, so now would be a good time to install and learn jq for working with JSON on the command line.