AWS logically isolates your resources from everyone else, launching everything you use into your own virtual private cloud. It may run on the same hardware underneath, but AWS has built the systems to virtualize entire networks on their infrastructure.
Your Instances Are Private
When you first create an EC2 instance, a new VPC is created for you. Every instance you launch is created in this VPC, and is given a random private IP address.
This IP address is virtual, just like the whole VPC itself. AWS works their magic behind the scenes to make this networking work, but your VPC is yours and yours alone. You might share the same private IP with many other people, exactly like how everyone's home router is usually
192.168.1.1
.
Nobody can connect to your instance on your private IP, meaning if you have an instance that doesn't have any connections to the outside world, it is virtually air-gapped from everything else. This makes AWS way more secure than other providers who may simply assign you a unique private IP for each server and be done with it.
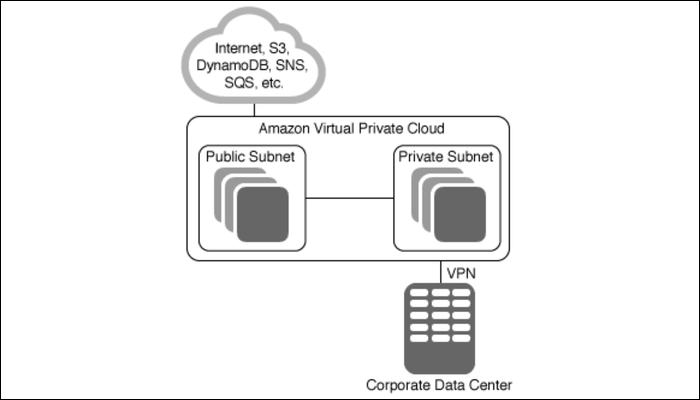
Your default VPC is likely good enough to be used for everything, and simply acts as your own personal cloud, separating your assets from other people running on the same servers. If you're a large business with specific needs, AWS provides many templates for common scenarios with custom VPCs, including public and private subnets with a VPN connection for on-site access.
Having a private subnet allows you to run things like database servers, which shouldn't be connected to the actual internet but need to talk to your other instances (such as web servers fetching information). You can do this pretty easily with VPCs.
VPC Subnets and Networking
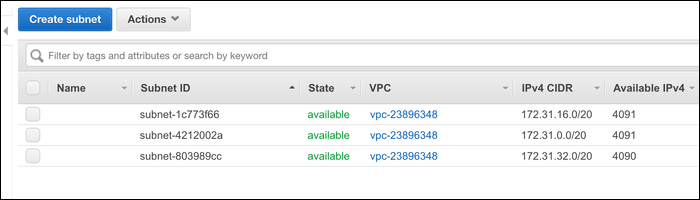
You can define these however you want, but the default configuration will probably work fine for most people. By default, your VPC will use the
172.31.0.0/16
block, with the following subnets:
-
172.31.0.0/20 -
172.31.16.0/20 -
172.31.32.0/20
You can create any number of subnets, though you cannot overlap them within the same VPC. When you launch an instance, you'll launch them into a specific subnet; if you didn't specify a custom subnet, it will have launched into the default subnet for your availability zone.
Your VPC connects to the internet with an Internet Gateway, which is like a virtual router that everything hides behind. You can have multiple gateways per VPC, but there isn't much purpose to that.
Your Elastic IP Addresses are tied to your VPC; the public IP part is given to you randomly out of Amazon's pool (usually from their gigantic
3.0.0.0/8
block of over 16 million addresses), but the private IP address it is mapped to is specific to your VPC.
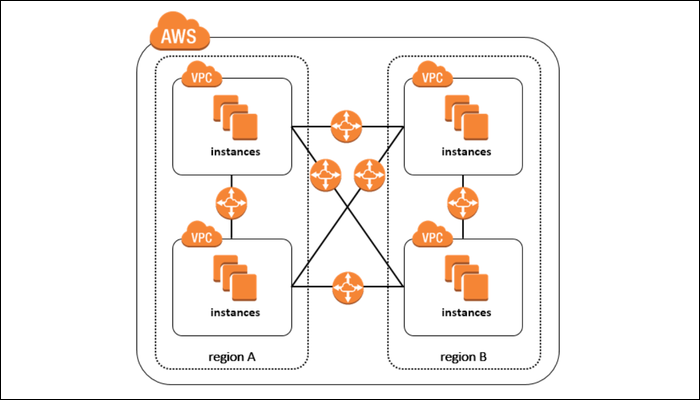
VPCs are specific to AWS regions, so you'll have different VPCs for us-east and us-west. However, AWS provides many tools for setting up communication between them, so your VPCs can act as one cloud. Note that your subnets must be set up to have no overlap between VPCs for this to work properly.
You are also charged for data transfer between regions, because it has to go over the actual Internet wires. However, all traffic is encrypted over the "AWS Backbone," so it's still private.