
Matthew Hughes
Contributing since October, 2019
-
26articles
About Matthew Hughes
Matthew Hughes is a tech journalist with bylines in The Register, The Next Web, The Daily Beast, Gizmodo UK, The Daily Dot, and more.
Latest Articles

How to Protect Yourself From SIM-Swapping Attacks
Even the best-laid security plans can go awry if you fall victim to a SIM-swapping attack. Here's how to protect yourself.

Do Hackers Really Battle in Real Time?
Remember that episode of "NCIS," in which multiple hackers frantically type on the same keyboard, while battling another hacker? Yeah, that's not how it works.

Why People Restore Vintage Computers, and How You Can Too
Interested in restoring a retro computer? Here are some tips to get you started with this increasingly popular hobby.

An Open Alternative to Intel and ARM: What is RISC-V?
How RISC-V intends to change the computing landscape.

What Is Edge Computing, and Why Does It Matter?
How do you make cloud computing even more convenient? Give it an edge!
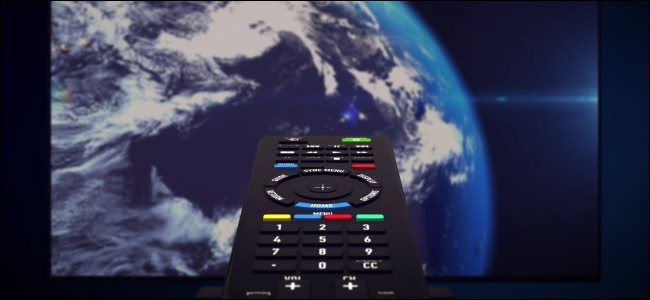
Why an IR Blaster Is Still Useful on Phones in 2020
Remember IR blasters? Some modern smartphones still include them---and they still have their uses.

Why I Still Use an Old PowerPC Mac in 2020
A classic PowerPC Mac from the early 2000s might just boost your productivity.

Why People Still Buy Feature Phones in 2020
Before the smartphone, feature phones were the hottest devices on the market. But why are people still buying them in 2020?

Meet Celia, Huawei’s Google Assistant Replacement
Bixby has a new friend! Samsung isn't the only Android manufacturer to create its own voice assistant.

Does Private or Incognito Mode Make Web Browsing Anonymous?
How well do private browsing modes, like Chrome's "Incognito," protect your online activities?

Can Law Enforcement Really Track Someone Down with an IP Address?
In movies and TV shows, cops often catch criminals with just an IP address. Is this accurate, or just creative embellishment?

Can You Really "Zoom and Enhance" Security Footage?
We've all seen detectives "zoom and enhance" footage in TV shows and movies. How does that actually work?

Can Law Enforcement Really Recover Files You've Deleted?
Is it really possible for law enforcement to recover deleted files? Yes, actually. Here's how it works.

What Is Harmony OS? Huawei's New Operating System Explained
Harmony OS is Chinese tech giant Huawei's new operating system, and it might one day be the company's replacement for Android.
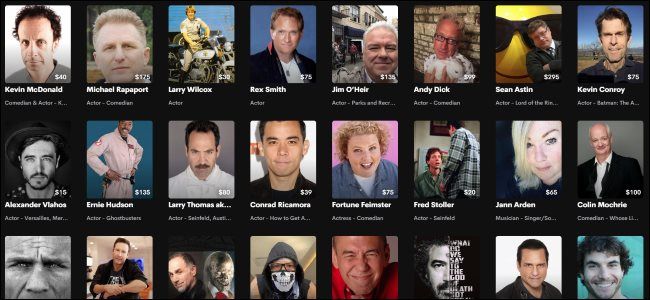
Celebrities on Demand: What Is Cameo?
Want a short video message from your favorite celebrity? That's what Cameo is for. Now you can pay to book a one-on-one Zoom call with a celebrity, too.

Does It Really Take 60 Seconds to Trace a Phone Call?
You've seen it on your favorite cop show: To trace a call, the detective has to keep the perp on the phone for a full minute. Is this accurate in the real world?

Can Hackers Really "Bounce" Their Signal All Over the World?
You've seen that movie where the hacker has to "bounce" a signal all over the world to evade detection, right? But is that even possible?

What Is a Man-in-the-Middle Attack?
Have you heard of Man-in-the-middle (MITM) attacks? If you use public Wi-Fi, you could fall prey to one. Fortunately, you can protect yourself!

What Is Dropshipping, and Is It a Scam?
Tempted to buy an item that popped up in your social media feed for dirt cheap? There are tons of online stores selling you products they haven't even seen, let alone tested, themselves. Here's what you need to know about this latest online scam.

Are Online Transcription Services Safe and Private?
Thinking of using an online service to transcribe voice mails, interviews, or meetings? Would you still want to if someone else would be listening to them?
