Quick Links
Key Takeaways
- Logging in as the Linux root user is risky as it grants all-powerful privileges. Logging in as root over SSH is even worse, as it allows remote attackers to potentially gain access to your system.
- Many Linux distributions recommend against logging in as root and instead suggest using the sudo command to temporarily elevate privileges when needed, reducing the risk of mistakes or malicious actions.
- If you need to allow root access over SSH, it is safer to use SSH keys instead of passwords. This eliminates the risk of brute-force attacks and unauthorized access.
Logging in as the Linux root user is bad practice. Logging in as root over an SSH connection is even worse. We tell you why, and show you how to prevent it.
This Cybersecurity Awareness Week article is brought to you in association with Incogni.
What is root on Linux?
You need someone with the authority to own and administer those parts of your operating system that are too important or too sensitive for regular users to deal with. That's where root comes in. root is the all-powerful superuser of Unix and Linux operating systems.
The root user account, like all accounts, is protected by a password. Without the root user's password, no one else can access that account. That means root's privileges and powers cannot be used by anyone else. The flip side is that the only defense between a malicious user and root's powers is that password. Passwords, of course, can be guessed, deduced, spotted written down somewhere, or brute-forced.
If a malicious attacker discovers root's password they can log in and do anything they like to the entire system. With root's elevated privileges there are no restrictions on what they can do. It would be just as if the root user had walked away from a terminal without logging out, allowing opportunistic access to their account.
Because of these risks, many modern Linux distributions don't allow root to login to the computer locally, never mind over SSH. The root user exists, but they don't have a password set for them. And yet, someone has to be able to administer the system. The solution to that conundrum is the sudo command.
sudo allows nominated users to temporarily use root-level privileges from within their own user account. You need to authenticate to use sudo, which you do by entering your own password. This gives you temporary access to root's capabilities.
Your root powers die when you close the terminal window they were used in. If you leave the terminal window open they'll timeout, automatically returning you to regular user status. This provides another type of protection. It protects you from yourself.
If you habitually log in as root instead of a regular account, any mistakes you make on the command line could be catastrophic. Having to use sudo to perform administration means you're more likely to be focused and careful about what you type.
Allowing root login over SSH increases the risks because attackers don't have to be local; they can try to brute-force your system remotely.
The root User and SSH Access
You're more likely to come across this problem when you administer systems for other people. Somebody may have decided to set a root password so that they can log in. Other settings need to be changed to allow root to log in over SSH.
This stuff won't happen by accident. But it can be done by people who don't understand the associated risks. If you take over the administration of a computer in that state, you'll need to advise the owners why it's a bad idea, and then revert the system to safe working. If it was something configured by the previous system administrator, the owners may not know about it.
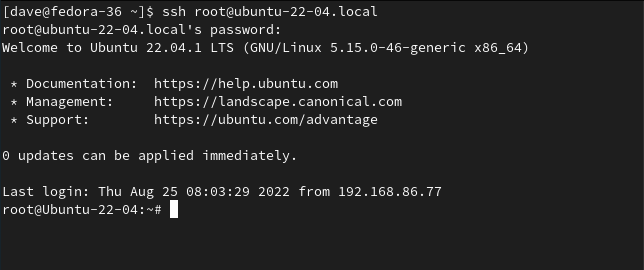
Here's a user on a computer running Fedora, making an SSH connection to an Ubuntu computer as the root user of the Ubuntu computer.
ssh root@ubuntu-22-04.local
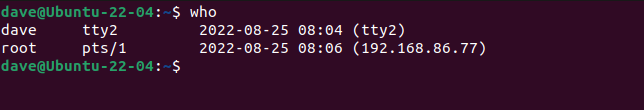
The Ubuntu computer allows the root user to log in over SSH. On the Ubuntu computer, we can see that a live connection is underway from the root user.
who
What we can't see is who is using that session. We don't know whether the person on the other end of the SSH connection is the root user or someone that has managed to obtain root's password.
Disabling SSH Access for root
To disable SSH access for the root user we need to make changes to the SSH configuration file. This is located at "/etc/ssh/sshd_config." We'll need to use sudo to write changes to it.
sudo gedit /etc/ssh/sshd_config
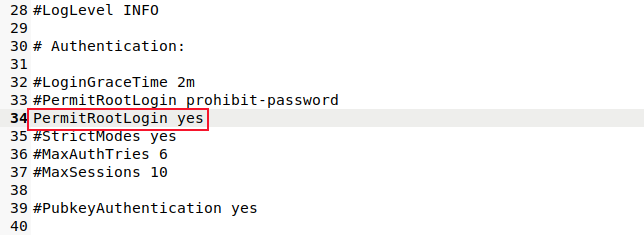
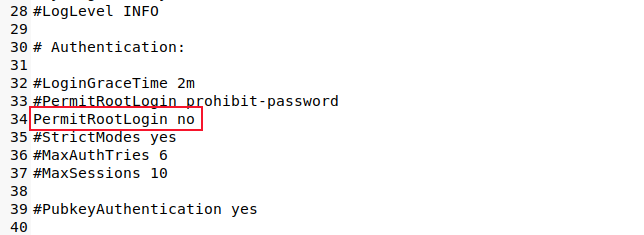
Scroll through the file or search for the string "PermitRootLogin."
Either set this to "no" or comment the line out by placing a hash "#" as the first character on the line. Save your changes.
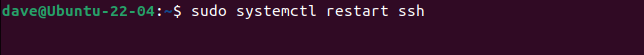
We need to restart the SSH daemon so that our changes come into effect.
sudo systemctl restart ssh
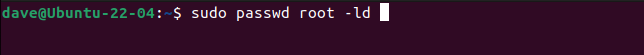
If you also want to prevent local logins, disable root's password. We're taking a belt and braces approach and using both the -l (lock) and -d (delete password) options.
sudo passwd root -ld
This locks the account and removes the account password into the bargain. Even if the root user is physically sitting at your computer they won't be able to log in.
A Safer Way to Allow root SSH Access
Sometimes you'll encounter managerial resistance to removing root access over SSH. If they really won't listen, you might find yourself in a position where you have to reinstate it. If this is the case, you ought to be able to compromise in a way that reduces risk and still permits remote logins from the root user.
Using SSH keys to make a connection over SSH is far more secure than using passwords. Because no passwords are involved, they cannot be brute-forced, guessed, or otherwise discovered.
Before you lock the local root account, set up SSH keys on the remote computer so that the root user can connect to your local computer. Then go ahead and delete their password and lock their local account.
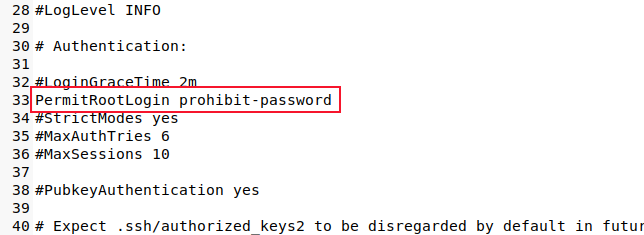
We'll also need to edit the "sshd_config" file once more.
sudo gedit /etc/ssh/sshd_config
Change the "PermitRootLogin" line so that it uses the "prohibit-password" option.
Save your changes and restart the SSH daemon.
sudo systemctl restart ssh
Now, even if someone reinstates the root user's password, they will not be able to log in over SSH using a password.
When the remote root user makes an SSH connection to your local computer the keys are exchanged and examined. If they pass authentication, the root user is connected to your local computer without the need for a password.
ssh root@ubuntu-22-04.local
No Entry
Refusing remote connections from the root user is the best option. Allowing root to connect using SSH keys is second best, but still a lot better than using passwords.