Wi-Fi network names can be longer than you might think. But what about passwords? Here's the maximum length for Wi-Fi passwords based on your network's security protocol.
People tend to groan at very long passwords---who enjoys pecking them out using a TV remote or the tiny touchpad on a network printer, after all? But passwords are important: the longer and more complex, the better.
Here's a look at the history of Wi-Fi password length from the beginning of the Wi-Fi standard, and how the maximum length has changed as the security protocols have evolved.
If you're not interested in the history of early Wi-Fi security protocols and passwords, feel free to jump to the last section for a discussion of modern Wi-Fi password requirements.
WEP: The First Wi-Fi Security Protocol
Wi-Fi passwords have been around since the first commercial implementation of Wi-Fi in the late 1990s. The first Wi-Fi security protocol was called Wired Equivalent Privacy (WEP). The earliest commercial access points used WEP until better protocols around the mid-2000s superseded it.
We're talking about WEP here as a historical curiosity and to thoroughly answer the question at hand. It's a very old protocol that has been compromised for years, and you should use modern Wi-Fi security protocols instead.
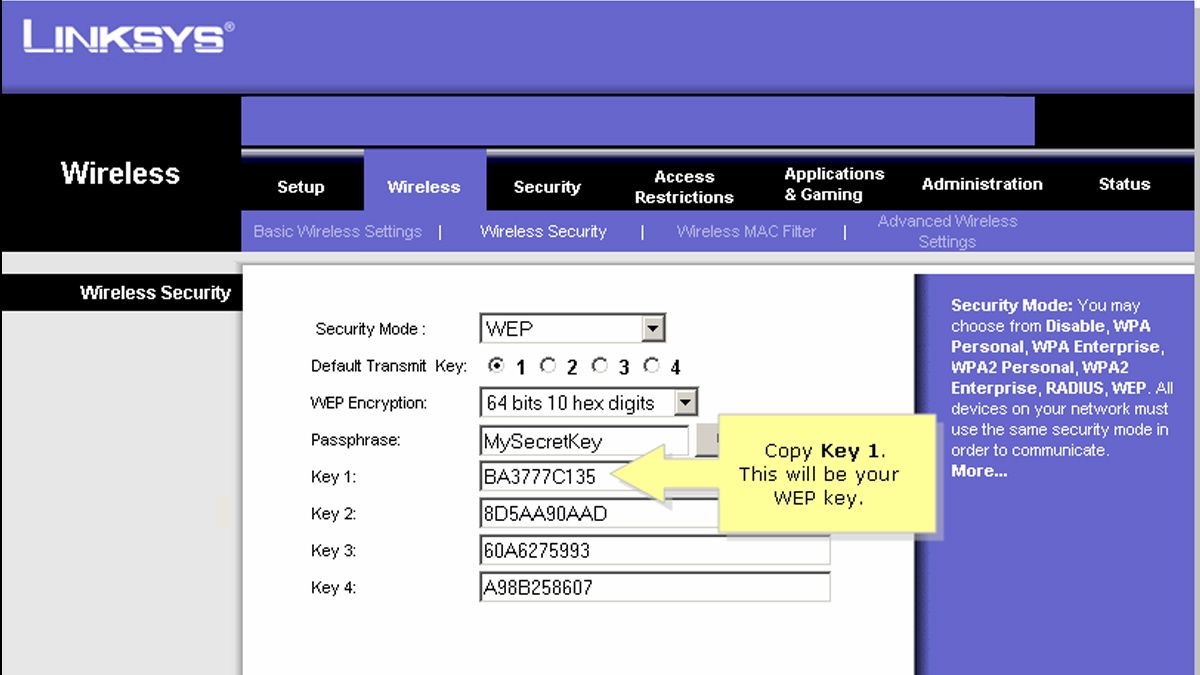
Compared to the way we use Wi-Fi passwords today, the way WEP functioned seems pretty archaic and overly fussy. WEP used a hexadecimal key system---most consumer routers included a key generator in the firmware for user convenience.
Your password or passphrase was used to generate the key was dependent on the level of encryption the version of WEP used. WEP encryption strength ranged from 64-bit in the earliest implementations to 256-bit in the later versions---although 128-bit was the most common.
The shortest password was 5 ASCII characters for 64-bit WEP and would yield a 10-character hexadecimal string. An input like
John9
would generate a key like
ZH2J3M5N6P
.
The longest possible password was 29 characters when using 256-bit WEP. An input like
WEPsATerribleSecurityProtocol
would yield a much longer key like
XFYH2J3K5N6P7R9SATCVDWEYGZH2J4M5N6Q8R9SBUCVDXFYGZJ3K4M6P7Q
.
Not only was WEP insecure, but using it was inconvenient. Let's move on to the present day.
WPA and Beyond: Double the Password Length
Wi-Fi Protected Access (WPA) was introduced in 2003 to fix the serious security issues with the WEP security protocol. WPA was, in turn, just an intermediary while WPA2 was rolled out in 2004.
Much further down the road, in 2018, the Wi-Fi Alliance announced an even better version of WPA, WPA3---we strongly recommend you switch to WPA3 if your router and the devices in your home support it.
If your router doesn't support WPA3, there's no time like the present to upgrade. Not only will you get better security, but you'll also get better speeds and an overall improved experience.
We're lumping the entire WPA family of security protocols together in this section---despite the significant security improvements between them over the years---because the password parameters have stayed the same throughout all the iterations.
The enforced minimum length of a WPA password is eight characters, and the maximum length is 63 characters.
Regardless of what you fill your 8-63 character spread with, the characters must be ASCII printable characters which includes
A-Z
,
a-z
,
0-9
, as well as the standard symbols found on a QWERTY-style keyboard like
$
,
!
, and so on---no emoji allowed.
Even though you can stick to a short password, you shouldn't. Between a weak 8-character password like
NoWEP4Me
and a very strong maximum length 63-character password like
WEPsATerribleSecurityProtocolSoUseWPA3WithRandomSymbols&^2*!5$%
, we recommend you err on the lengthier side.
Putting aside potential security vulnerabilities and looking at it only from a raw computing standpoint, the former example would take under an hour to brute force crack, and the latter would take trillions of years. No need to use a 63-character password, but do aim for at least 12-16 characters with plenty of variation and symbols or consider a passphrase.
Believe it or not, from a computational processing standpoint, a plain English passphrase you can easily remember like
I Love Deep Dish Pizza!
is harder to brute force than something much more difficult to remember like
Pizza2!44@$%!3%2
.
While you're thinking about passwords, now is a great time to brush up on what makes for a strong password. And, while you're at it, consider using a password manager. If you don't have to remember the password, whether or not it's memorable is irrelevant!