Quick Links
Apple's iMessage service uses secure end-to-end encryption. This ensures only you and the person you're talking to can see your messages. But there's a big privacy hole in iMessage, and it's named iCloud. Here's what you need to know.
iMessage Uses End-to-End Encryption to Send and Receive Messages
Apple's iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents.
Photos, videos, and other file attachments are also encrypted. What's more, Apple's FaceTime service also uses end-to-end encryption for voice and video calls, too.
This means that Apple and its employees cannot see the contents of the iMessages you're sending and receiving---even if they wanted to.
So far, so good. But there's a big "gotcha" here.
iCloud Backups Are Enabled by Default and Aren't E2E Encrypted
If you have iCloud Backups enabled on your iPhone or iPad---and most people do---then there's a big hole in the normally secure, end-to-end encryption.
With iCloud Backup enabled, your iCloud messages are encrypted, then backed up to iCloud and stored on Apple's servers. However, Apple receives a copy of the key that is used to encrypt that backup.
In other words: Apple and its employees could technically access the contents of your iMessage backups on Apple's servers. The backups aren't end-to-end encrypted. If Apple's servers were compromised or someone else gained access to your iCloud account, they could see the contents of your messages. This also means that Apple could turn over the contents of your iMessage history if compelled to by a government.
Apple makes all this clear in its iMessage and FaceTime Privacy policy. (As that policy says, Apple never stores the contents of FaceTime audio or video calls. Only messages and attachments in iMessage are stored.)
Of course, even iMessage is much better than traditional text messages. SMS messages aren't even private or secure when you're sending and receiving them! Your cellular carrier can see their contents.
Why Aren't iCloud Backups End-to-End Encrypted?
There are several reasons why Apple doesn't use end-to-end encryption for backups.
First, this provides more protection for average people who lose their passwords. If you lose your Apple ID password and go through Apple's password recovery process, you can regain access to all your data, including your iMessage backups. With end-to-end encryption, Apple could give you access to your account---but if you lost your password, you would never be able to access those backups again.
In this way, end-to-end encrypted backups are less user-friendly. Imagine explaining to a bunch of Apple customers that, actually, they can never access their data again because they forgot their passwords. To implement an account recovery process that doesn't lose data, Apple must have the key that unlocks those backups.
It's fair to ask, however, why Apple doesn't at least offer end-to-end encryption as an option for backups. Perhaps there could be an advanced option that encrypts them behind a big warning message.
According to a report in Reuters from January 2020, Apple was planning to offer end-to-end encryption for iCloud backups. However, the company dropped plans to let its users fully encrypt backups after the FBI complained that this would make it more difficult for law enforcement to get iPhone users' data.
Messages in iCloud vs. iCloud Backup of Messages
There are several moving parts here. Apple has two services that host your messages: Messages in iCloud syncs your messages between devices, and it is end-to-end encrypted. However, if you use iCloud Backup to back up anything on your device, it seems that iCloud gets a copy of the key that can decrypt the messages---even if you're not backing up messages using iCloud.
Apple makes this very confusing, but it's spelled out most clearly on Apple's iCloud Security Overview page:
Messages in iCloud also uses end-to-end encryption. If you have iCloud Backup turned on, your backup includes a copy of the key protecting your Messages. This ensures you can recover your Messages if you lose access to iCloud Keychain and your trusted devices. When you turn off iCloud Backup, a new key is generated on your device to protect future messages and isn't stored by Apple.
In other words, having Messages in iCloud enabled is fine for security... but only if you disable iCloud Backup. This prevents the key from being uploaded to Apple.
If you want to use iCloud Backups to back up your device, you will need to disable Messages in iCloud.
How to Ensure That Apple Can't See Your iMessage
Disabling Messages in iCloud Isn't Good Enough
You might think that you can solve this problem by disabling Messages in iCloud. However, the only solution is disabling iCloud backup itself.
Here's a quick summary of what the various combinations of settings do:
- iCloud Backup Enabled, Messages in iCloud Enabled: Apple will store your iCloud messages on its servers in an end-to-end encrypted manner. However, the encryption key will be uploaded as part of the iCloud backup, giving Apple access to your messages.
- iCloud Backup Enabled, Messages in iCloud Disabled: With Messages in iCloud disabled, Apple will upload a copy of your messages as part of your iCloud backup instead.
- iCloud Backup Disabled, Messages in iCloud Enabled: Apple will store your iCloud messages on its servers in a secure, end-to-end encrypted manner. The key to them will not be uploaded to Apple's servers.
Unfortunately, there is no way to prevent iCloud backup from uploading just your messages or just your encryption key. You must disable iCloud backup entirely if you want to remove Apple's access to your messages.
The Only Solution: Disable iCloud Backups
You can keep using Messages in iCloud to sync your messages, if you like, but you must disable iCloud Backups entirely on the devices you're syncing messages to. This will prevent Apple from storing a copy of the decryption key that can access these messages. (If you just disable Messages in iCloud and leave iCloud backups enabled, Apple says it will upload a copy of your messages as part of your backups.)
Unfortunately, you cannot just tell iCloud to stop backing up your Messages---you have to disable iCloud backups entirely.
It's a good idea to regularly back up your iPhone using iTunes on your PC or Mac if you disable automatic iCloud backups.
Of course, people you talk to on iMessage likely have iCloud Backups enabled for iMessage on their own account, even if you don't. This means that your messages may be stored on Apple's servers---in the other person's iCloud backup, of course. To prevent this from happening, consider switching to a secure messaging app that doesn't back up to iCloud---like Signal.
For improved privacy when communicating in Messages, have the person you're communicating with disable iCloud backup, too. Of course, you should also be sure to communicate via iMessage and not SMS, as SMS messages aren't encrypted.
Doesn't Your iPhone Back up Signal Data to iCloud, Too?
Of course, iMessages aren't the only thing that your iPhone backs up to iCloud. It backs up the local data many other apps are storing, too---if you have iCloud Backup enabled.
Some other secure, end-to-end encrypted messaging apps get around this concern by just not backing up your messages to iCloud.
For example, the secure messaging app Signal does not back up your message history to iCloud, as Signal's support site explains. It is always stored locally on your device. You can transfer messages from one iPhone to a new iPhone, but it's a process that moves messages to a new iPhone and deletes them from your old one.
If you've wiped or lost, or just don't have your old iPhone, you can't move your messages to a new device. That's the idea---Signal is designed with privacy and security in mind. It may be less convenient to keep your message history forever, but that protects your privacy.
How to Make Encrypted iPhone Backups
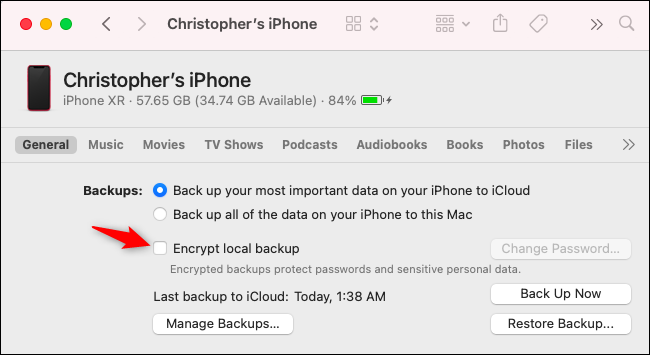
By the way, you can make encrypted backups of your iPhone. You just can't do it with iCloud. If you have a Windows PC or Mac, you can connect your iPhone (or iPad) to your computer with a USB cable and back up to a local file via iTunes (on Windows) or Finder (on Mac).
Check the "Encrypt Local Backups" option to secure your local backup with a password.
If you lose your iPhone or have to erase it, you can restore this encrypted backup on a new iPhone. This will move your iMessage history to your new device without it being stored on Apple's servers.