Quick Links
Code injection is common on Windows. Applications "inject" pieces of their own code into another running process to modify its behavior. This technique can be used for good or evil, but either way it can cause problems.
Code injection is also commonly called DLL injection because the injected code is often in the form of a DLL (dynamic link library) file. However, applications could also inject other types of code that aren't DLLs into a process.
What Code Injection is Used For
Code injection is used to accomplish all sorts of tricks and functionality on Windows. While legitimate programs use it, it's also used by malware. For example:
- Antivirus programs often inject code into web browsers. They can use it to monitor network traffic and block dangerous web content, for example.
- Malicious programs might add code to your web browser to better track your browsing, steal protected information like passwords and credit card numbers, and change your browser settings.
- Stardock's WindowBlinds, which themes your desktop, injects code to modify how windows are drawn.
- Stardock's Fences injects code to change the way the Windows desktop works.
- AutoHotkey, which lets you create scripts and assign system-wide hotkeys to them, injects code to accomplish this.
- Graphics driver's like NVIDIA's inject DLLs to accomplish a variety of graphics-related tasks.
- Some programs inject DLLs to add additional menu options to an application.
- PC game cheating tools often inject code into games to modify their behavior and gain an unfair advantage over other players.
Is Code Injection Bad?
This technique is used constantly by a wide variety of applications on Windows. It's the only real way to accomplish a variety of tasks. Compared to a modern mobile platform like Apple's iOS or Google's Android, the Windows desktop is so powerful because if offer this kind of flexibility to developers.
Of course, with all that power comes some danger. Code injection can cause problems and bugs in applications. Google says that Windows users who have code injected into their Chrome browser are 15% more likely to experience Chrome crashes, which is why Google is working on blocking this. Microsoft notes that code injection could be used by malicious applications to tamper with browser settings, which is one reason it's already blocked in Edge.
Microsoft even provides instructions for checking whether third-party DLLs are loaded in Microsoft Outlook, as they cause so many Outlook crashes.
As a Microsoft employee put it in a developer blog from 2004:
DLL injection is never safe. You're talking about squirting code into a process that was never designed, built, or tested by the process's author, and co-opting or creating a thread to run that code. You run the risk of creating timing, synchronization, or resource issues that weren't there before or exacerbating issues that were there.
In other words, code injection is kind of a dirty hack. In an ideal world, there would be a safer way to accomplish this that didn't cause potential instability. However, code injection is just a normal part of the Windows application platform today. It's constantly happening in the background on your Windows PC. You might call it a necessary evil.
How to Check for Injected DLLs
You can check for code injection on your system with Microsoft's powerful Process Explorer application. It's basically an advanced version of the Task Manager packed with additional features.
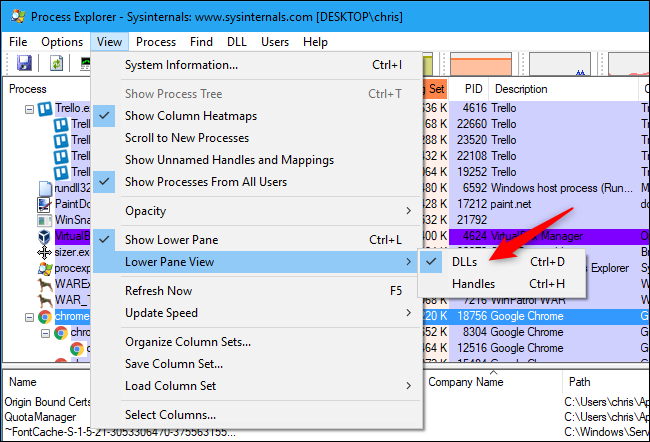
Download and run Process Explorer if you'd like to do this. Click View > Lower Pane View > DLLs or press Ctrl+D.
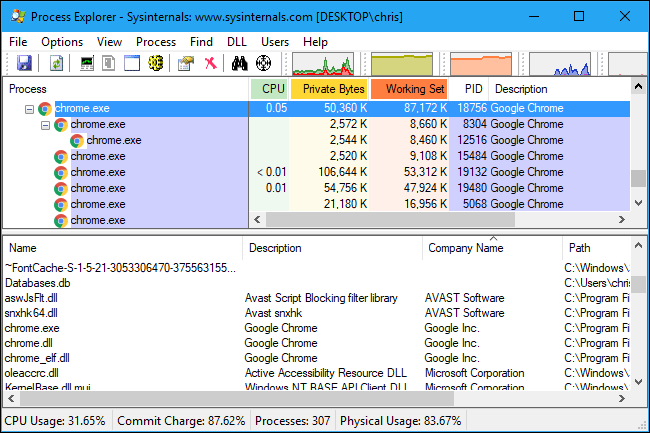
Select a process in the top pane and look in the lower pane to see the DLLs that are loaded. The "Company Name" column provides a useful way to filter this list.
For example, it's normal to see a variety of DLLs made by "Microsoft Corporation" here, as they're part of Windows. It's also normal to see DLLs made by the same company as the process in question---"Google Inc." in the case of Chrome in the screenshot below.
We can also spot a few DLLs made by "AVAST Software" here. This indicates that the Avast antimalware software on our system is injecting code like the "Avast Script Blocking filter library" into Chrome.
There's not much you can do if you find code injection on your system---aside from uninstalling the program injecting code to prevent it from causing problems. For example, if Chrome crashes regularly, you may want to see if there are any programs injecting code into Chrome and uninstall them to prevent them from tampering with Chrome's processes.
How Does Code Injection Work?
Code injection doesn't modify the underlying application on your disk. Instead, it waits for that application to run and it injects additional code into that running process to change how it functions.
Windows includes a variety of application programming interfaces (APIs) that can be used for code injection. A process can attach itself to a target process, allocate memory, write a DLL or other code to that memory, and then instruct the target process to execute the code. Windows doesn't prevent processes on your computer from interfering with each other like this.
For more technical information, check out this blog post explaining how developers can inject DLLs and this look at other types of code injection on Windows.
In some cases, someone might change the underlying code on disk---for example, by replacing a DLL file that comes with a PC game with a modified one to enable cheating or piracy. This technically isn't "code injection." The code isn't being injected into a running process, but the program is instead being tricked into loading a different DLL with the same name.
Image Credit: Lukatme/Shutterstock.com.