Quick Links
Losing your hardware is bad enough, but what happens to your personal data? Could a thief with your phone, tablet, or laptop access your apps and files? It depends on the device you lost---unfortunately, most Windows PCs aren't encrypted.
Thieves can always erase your device and keep using it---unless you enable something like Activation Lock on an iPhone or iPad---but they can't get at your personal data if your device's storage is encrypted.
iPhones and iPads
Apple's iPhones and iPads are securely encrypted by default. A thief won't be able to unlock your phone without your passcode. Even if you normally sign in with Touch ID or Face ID, your phone is also secured with a passcode.
Of course, if you set your iPhone or iPad to not require a passcode or you use one that's very easy to guess---like 1234 or 0000---the thief may easily unlock it.
However, some types of personal information remain visible, even if you've protected your device with a passcode. For example, the thief can see any notifications that arrive on your phone without unlocking it. With the default settings, this means the thief will see incoming text messages---including messages that contain SMS verification codes for accessing your accounts. You can hide sensitive notifications from your lock screen, but they're all on your lock screen by default. The thief could also answer incoming phone calls on your phone.
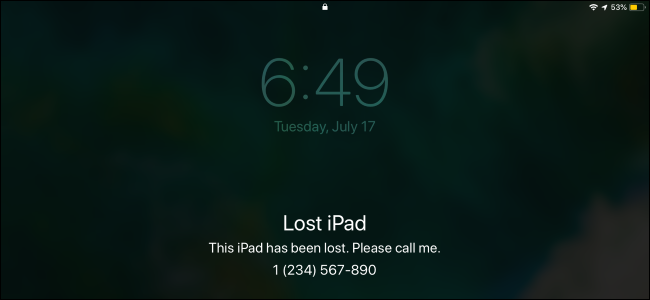
You can head to Apple's Find My iPhone website to remotely locate your lost iPhone or iPad. To prevent a thief from using your device, put it into "Lost Mode." This will disable all notifications and alarms on it. Lost Mode also lets you write a message that will appear on the phone or tablet---for example, you could ask whoever finds it to return it and provide a phone number where you can be reached.
If you've given up on getting your iPhone or iPad back, you can---and should---remotely erase it. Even if it's offline, it will be erased the next time it comes online.
GrayKey could allow police departments and other government agencies to bypass your passcode, but Apple is fixing this with USB Restricted Mode.
Android Phones
Modern Android phones are encrypted by default, too. Specifically, encryption is required by default starting with Android 7.0 Nougat, which was officially released in August, 2016. As long as the phone you're using originally came with Android Nougat or a newer version of Android, it's definitely encrypted.
If your phone originally came with an older version of Android and you never enabled encryption, your phone's storage may not be encrypted and it may be possible for thieves to get your data off of it. Even if your phone is currently running Android 7.0 or newer, it may not be encrypted if it originally ran an older version of Android.
Of course, this encryption only helps if you're using a secure PIN or passphrase to protect your device. If you're not using a PIN or you're using something easy to guess---like 1234---a thief can easily get access to your device.
Just like on an iPhone, your Android phone will continue displaying notifications on your lock screen. This could expose sensitive text messages, for example, unless you hide sensitive notifications from your lock screen.
You can use Google's Find My Device to remotely locate your lost Android phone. This tool also lets you lock your device to stop the thief from seeing your notifications, and remotely wipe it to ensure your personal data is removed from the phone.
Windows PCs
Most Windows PCs are in trouble if they're ever stolen. Windows 10 is still the only modern operating system that doesn't provide encryption to all users, and Windows 7 and 8 were even worse. There's a very good chance your Windows PC's storage is not encrypted, which means that anyone who steals your Windows device can gain access to your private files simply by booting another operating system on it or pulling out the internal drive and putting it in another computer.
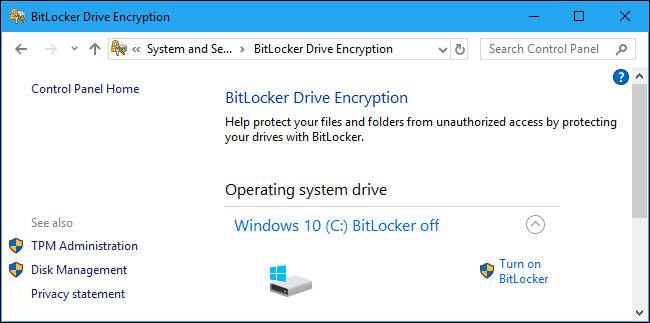
If you're using a Professional, Enterprise, or Education edition of Windows 7, 8, or 10, you can enable optional BitLocker encryption to protect your device. If you are using these more expensive editions of Windows and have set up BitLocker, then your data will be secure---assuming you used a strong password.
You can check if BitLocker is in use on a PC by heading to Control Panel > System and Security > BitLocker Drive Encryption. (If you don't see the option, you're using a Home edition of Windows.)
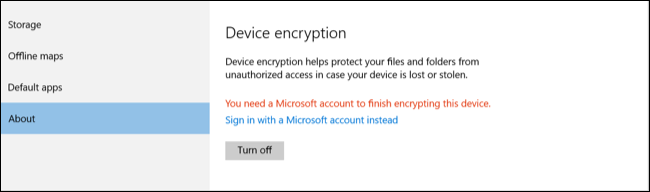
If you're using a Home edition of Windows 7, 8, or 10, there is no way to use standard BitLocker encryption. Some newer PCs that shipped with Windows 8.1 or 10 do have a special, limited version of BitLocker that was originally called "Device Encryption." This will automatically encrypt their storage---but only if you sign in with a Microsoft account and not a local user account. This encryption feature is not available on all Windows 8.1 and 10 PCs, but only on PCs with specific hardware.
You can check if Device Encryption is available on a PC by heading to Settings > System > About. Look for a message about "Device Encryption." If you don't see this section, your PC doesn't support it.
If you're using a Home edition of Windows, you can also try third-party encryption tools like VeraCrypt or pay $100 to upgrade from Home to Professional to get BitLocker.
The bad news is that, unless you've gone out of your way to enable encryption with BitLocker or you have this encryption feature built into your Windows 10 PC, your PC's internal storage is probably unencrypted and its files will be accessible to thieves.
If your device ran Windows 10, you can use Microsoft's Find My Device tool to track it---assuming Find My Device was enabled on the PC before you lost it.
We think Microsoft should enable encryption by default for everyone. Unfortunately, it hasn't done so and, among modern devices, Windows PCs are uniquely vulnerable to data theft unless BitLocker is enabled.
MacBooks
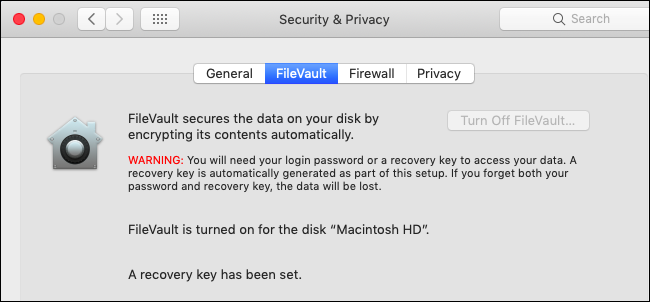
Apple has been encrypting Mac storage by default with FileVault since OS X 10.10 Yosemite, which was released in 2014. Your Mac's internal disk is almost certainly encrypted with FileVault, which prevents anyone from accessing your files without knowing your Mac password.
You can double-check whether your Mac is encrypted by heading to Apple menu > System Preferences > System & Privacy > FileVault.
Of course, this assumes your MacBook is secured with a password. If you use a very weak, easily guessable password or set up automatic login, the thief can easily gain access.
If you enabled Find My Mac, you can use Apple's Find My iPhone tool (yes, Macs appear in it, too) to remotely lock and erase your Mac. The passcode you set when you lock your Mac will even prevent the thief from resetting your Mac and using it as their own.
Chromebooks
Chromebooks always have encrypted storage, so a thief won't be able to sign in and access your data without your Google account password or the PIN you use to unlock your Chromebook.
The thief can sign in with another Google account, log into the guest account, or erase your Chromebook and set it up from scratch---but they won't be able to access your personal data.
This assumes that your Google account has a good password and not something like "password" or "letmein," of course.
Linux Laptops
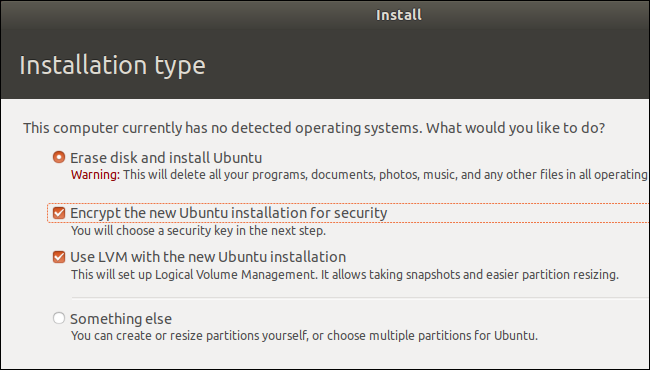
If you were running Linux on your laptop, whether it was encrypted depends on the options you chose while installing your Linux distribution of choice. Most modern Linux distributions, including Ubuntu, let you enable disk encryption during the installation process, and this encryption is either secured with your normal Linux user account password or with a special encryption passphrase you type when your computer boots.
However, this encryption option often isn't enabled by default---it isn't on Ubuntu. If you didn't choose to enable it, your Linux system will not be using encrypted storage.
Assuming you did enable encryption while installing your Linux distribution, your data should be protected---as long as you used a secure password that's hard to guess.
Laptops Are More Vulnerable While Asleep
There's one more consideration for laptops: If your laptop was powered on but asleep, its encryption key is stored in its memory. Theoretically, an attacker could perform a "cold boot attack," quickly resetting your device and booting another operating system from a USB drive to grab the encryption key from memory before it's erased.
Most thieves aren't even going to think about an attack like this, as it's quite sophisticated. However, if you are seriously worried about corporate espionage or government agencies, it's safer to shut down your laptop when you aren't using it instead of leaving it in sleep mode. You may just want to shut it down when you're taking it to a public place or somewhere else you're worried it may be stolen, too. This will ensure the encryption key isn't present in memory.
Image Credit: waewkid/Shutterstock.com.