Over the past few months, a bug in the popular Cloudflare service may have exposed sensitive user data---including usernames, passwords, and private messages---to the world in plain text. But how big is this problem, and what should you do?
What Is Cloudflare?
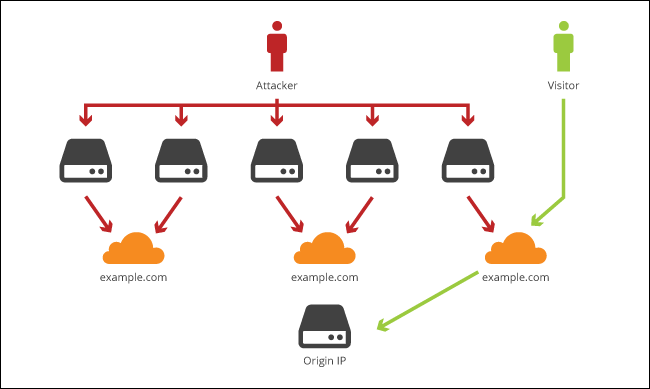
Cloudflare is a service that offers security and performance features (among other things) to a wide network of websites. It acts as a reverse proxy, a middleman between you---the user---and a given website. When you go to visit that site, you'll be directed to one of Cloudflare's servers instead of the actual site's servers.
This allows Cloudflare to ensure you're a legitimate user (thus protecting against denial of service attacks), load the site faster (since they've cached certain parts of the site), and protect against downtime (since they have multiple servers worldwide and can fall back on any server if one has a problem).
In short: Cloudflare aims to make sites faster and more secure, and it's a service a lot of websites use.
What Happened? (And What Is "Cloudbleed?")
Unfortunately, nothing is 100% secure, even if a site uses a service like Cloudflare, and bugs happen. In this case, Cloudflare actually caused a security problem: a bug in the reverse proxy code that parses HTML caused Cloudflare's servers to leak the contents of its memory in certain circumstances. (Some people are referring to this as "Cloudbleed", a play off the Heartbleed bug that also affected a large portion of the internet.)
This data could have included all kinds of sensitive data, including usernames, passwords, private messages, OAuth tokens, and a lot more. Even worse, some of that data was indexed and cached by some search engines (about 700 pages, according to Cloudflare), so if you knew what to search on Google, you could find sensitive data from users logging in at the time of a specific leak.
This bug went undiscovered for about five months, and was patched after being discovered this week. Cloudflare says "the greatest period of impact was from February 13 and February 18 with around 1 in every 3,300,000 HTTP requests through Cloudflare potentially resulting in memory leakage (that's about 0.00003% of requests)."
But with a service as popular as Cloudflare, 0.00003% is still a lot. Some folks have been compiling a list of sites that use Cloudflare, and it includes over 4 million domains---including Yelp, OkCupid, Uber, Authy, Medium, and many many more. (Some mobile apps are affected as well.)
You can read more about the technical details of this bug at Cloudflare's blog, though it will probably only interest you if you're a programmer---if you're a regular internet user, the only thing you need to know is...
What Should I Do?
First: don't panic too much. Not every site on that list of 4 million necessarily leaked sensitive information---if a site was just using Cloudflare to cache image data, for example, there would be no sensitive information to leak. And it's not like each leak was a master list of passwords anyway---it was random pieces of information, which could have included a few random usernames and passwords at any given time.
However, Cloudflare also noted that one of their own private keys was leaked, which would have provided an attacker access to a lot of internal Cloudflare data---including, potentially, usernames and passwords. Cloudflare was extremely vague about this particular point, despite it being a major security risk with the potential to leak a lot more sensitive information
All that said, there's no real way to tell if any of your data was leaked and where, so the only safe course of action right now is to change all of your passwords. (Sure, you could look through the list of 4 million sites and only change those used by Cloudflare, but honestly, it'd probably be easier and faster to just change them all.)
The usual rules with passwords apply here: don't use the same password on multiple sites, use a password manager like LastPass, and turn on two-factor authentication for every site that allows it. If you aren't doing these things, the Cloudflare bug is probably the least of your worries---after all, sites get hacked all the time, and if you're using the same password everywhere, all your data is regularly at risk.
If you're already using a password manager, this process should be easy (if a bit long and boring). But you should be used to this dance by now.