Quick Links
Last month, Linux Mint's website was hacked, and a modified ISO was put up for download that included a backdoor. While the problem was fixed quickly, it demonstrates the importance of checking Linux ISO files you download before running and installing them. Here's how.
Linux distributions publish checksums so you can confirm the files you download are what they claim to be, and these are often signed so you can verify the checksums themselves haven't been tampered with. This is particularly useful if you download an ISO from somewhere other than the main site--like a third-party mirror, or through BItTorrent, where it's much easier for people to tamper with files.
How This Process Works
The process of checking an ISO is a bit complex, so before we get into the exact steps, let's explain exactly what the process entails:
- You'll download the Linux ISO file from the Linux distribution's website--or somewhere else--as usual.
- You'll download a checksum and its digital signature from the Linux distribution's website. These may be two separate TXT files, or you may get a single TXT file containing both pieces of data.
- You'll get a public PGP key belonging to the Linux distribution. You may get this from the Linux distribution's website or a separate key server managed by the same people, depending on your Linux distribution.
- You'll use the PGP key to verify that the checksum's digital signature was created by the same person who made the key--in this case, the maintainers of that Linux distribution. This confirms the checksum itself hasn't been tampered with.
- You'll generate the checksum of your downloaded ISO file, and verify it matches the checksum TXT file you downloaded. This confirms the ISO file hasn't been tampered with or corrupted.
The process may differ a bit for different ISOs, but it usually follows that general pattern. For example, there are several different types of checksums. Traditionally, MD5 sums have been the most popular. However, SHA-256 sums are now more frequently used by modern Linux distributions, as SHA-256 is more resistant to theoretical attacks. We'll primarily discuss SHA-256 sums here, although a similar process will work for MD5 sums. Some Linux distros may also provide SHA-1 sums, although these are even less common.
Similarly, some distros don't sign their checksums with PGP. You'll only need to perform steps 1, 2, and 5, but the process is much more vulnerable. After all, if the attacker can replace the ISO file for download they can also replace the checksum.
Using PGP is much more secure, but not foolproof. The attacker could still replace that public key with their own, they could still trick you into thinking the ISO is legit. However, if the public key is hosted on a different server--as is the case with Linux Mint--this becomes far less likely (since they'd have to hack two servers instead of just one). But if the public key is stored on the same server as the ISO and checksum, as is the case with some distros, then it doesn't offer as much security.
Still, if you're attempting to verify the PGP signature on a checksum file and then validating your download with that checksum, that's all you can reasonably do as an end-user downloading a Linux ISO. You're still much more secure than the people who don't bother.
How to Verify a Checksum On Linux
We'll use Linux Mint as an example here, but you may need to search your Linux distribution's website to find the verification options it offers. For Linux Mint, two files are provided along with the ISO download on its download mirrors. Download the ISO, and then download the "sha256sum.txt" and "sha256sum.txt.gpg" files to your computer. Right-click the files and select "Save Link As" to download them.
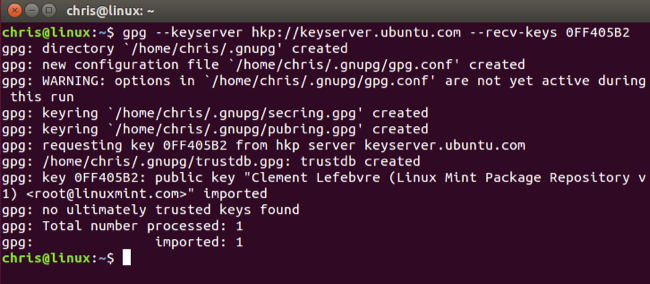
On your Linux desktop, open a terminal window and download the PGP key. In this case, Linux Mint's PGP key is hosted on Ubuntu's key server, and we must run the following command to get it.
gpg --keyserver hkp://keyserver.ubuntu.com --recv-keys 0FF405B2
Your Linux distro's website will point you towards the key you need.
We now have everything we need: The ISO, the checksum file, the checksum's digital signature file, and the PGP key. So next, change to the folder they were downloaded to...
cd ~/Downloads
...and run the following command to check the signature of the checksum file:
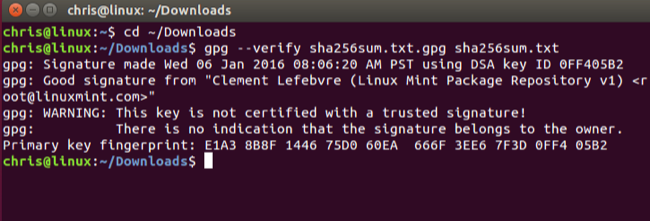
gpg --verify sha256sum.txt.gpg sha256sum.txt
If the GPG command lets you know that the downloaded sha256sum.txt file has a "good signature", you can continue. In the fourth line of the screenshot below, GPG informs us that this is a "good signature" that claims to be associated with Clement Lefebvre, Linux Mint's creator.
Don't worry that the key isn't certified with a "trusted signature." This is because of the way PGP encryption works--you haven't set up a web of trust by importing keys from trusted people. This error will be very common.
Lastly, now that we know the checksum was created by the Linux Mint maintainers, run the following command to generate a checksum from the downloaded .iso file and compare it to the checksum TXT file you downloaded:
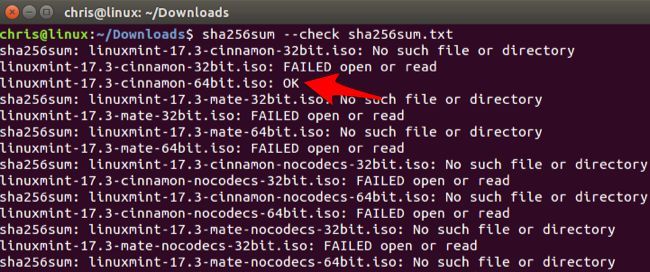
sha256sum --check sha256sum.txt
You'll see a lot of "no such file or directory" messages if you only downloaded a single ISO file, but you should see an "OK" message for the file you downloaded if it matches the checksum.
You can also run the checksum commands directly on an .iso file. It'll examine the .iso file and spit out its checksum. You can then just check it matches the valid checksum by looking at both with your eyes.
For example, to get the SHA-256 sum of an ISO file:
sha256sum /path/to/file.iso
Or, if you have an md5sum value and need to get the md5sum of a file:
md5sum /path/to/file.iso
Compare the result with the checksum TXT file to see if they match.
How to Verify a Checksum On Windows
If you're downloading a Linux ISO from a Windows machine, you can also verify the checksum there--though Windows doesn't have the necessary software built-in. So, you'll need to download and install the open-source Gpg4win tool.
Locate your Linux distro's signing key file and checksum files. We'll use Fedora as an example here. Fedora's website provides checksum downloads and tells us we can download the Fedora signing key from https://getfedora.org/static/fedora.gpg.
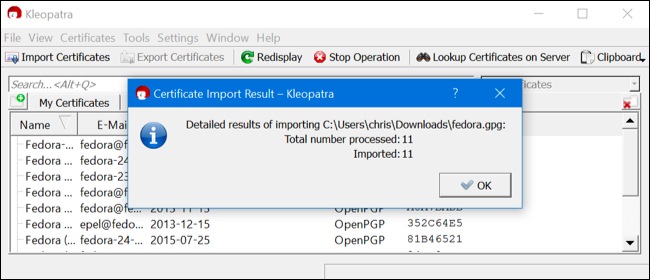
After you have downloaded these files, you'll need to install the signing key using the Kleopatra program included with Gpg4win. Launch Kleopatra, and click File > Import Certificates. Select the .gpg file you downloaded.
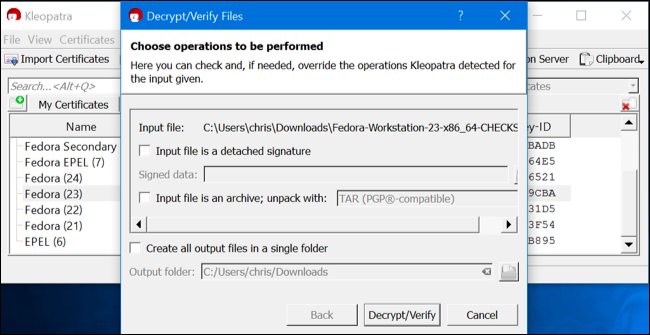
You can now check if the downloaded checksum file was signed with one of the key files you imported. To do so, click File > Decrypt/Verify Files. Select the downloaded checksum file. Uncheck the "Input file is a detached signature" option and click "Decrypt/Verify."
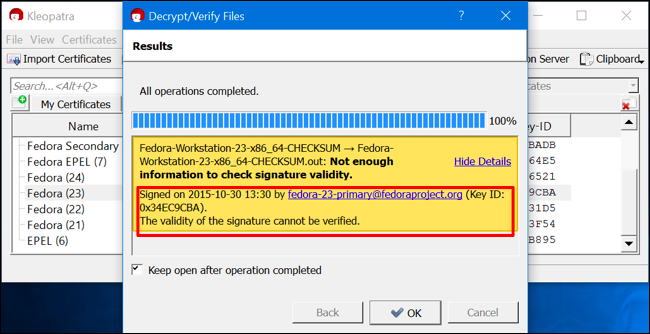
You're sure to see an error message if you do it in this way, as you haven't gone through the trouble of confirming those Fedora certificates are actually legitimate. That's a more difficult task. This is the way PGP is designed to work--you meet and exchange keys in person, for example, and piece together a web of trust. Most people don't use it in this way.
However, you can view more details and confirm that the checksum file was signed with one of the keys you imported. This is much better than just trusting a downloaded ISO file without checking, anyway.
You should now be able to select File > Verify Checksum Files and confirm the information in the checksum file matches the downloaded .iso file. However, this didn't work for us--maybe it's just the way Fedora's checksum file is laid out. When we tried this with Linux Mint's sha256sum.txt file, it did work.
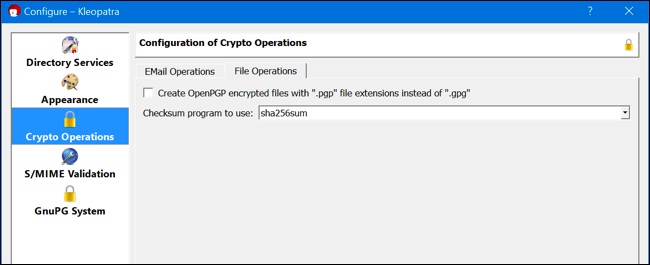
If this doesn't work for your Linux distribution of choice, here's a workaround. First, click Settings > Configure Kleopatra. Select "Crypto Operations," select "File Operations," and set Kleopatra to use the "sha256sum" checksum program, as that's what this particular checksum was generated with. If you have an MD5 checksum, select "md5sum" in the list here.
Now, click File > Create Checksum Files and select your downloaded ISO file. Kleopatra will generate a checksum from the downloaded .iso file and save it to a new file.
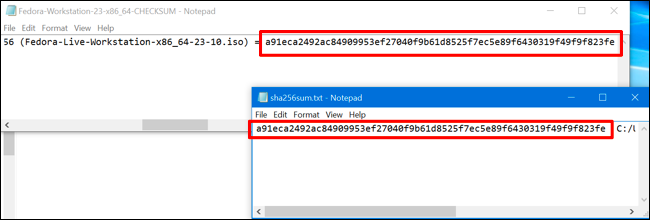
You can open both of these files--the downloaded checksum file and the one you just generated--in a text editor like Notepad. Confirm the checksum is identical in both with your own eyes. If it's identical, you've confirmed your downloaded ISO file hasn't been tampered with.
These verification methods weren't originally intended for protecting against malware. They were designed to confirm that your ISO file downloaded correctly and wasn't corrupted during the download, so you could burn and use it without worrying. They're not a completely foolproof solution, as you do have to trust the PGP key you download. However, this still provides much more assurance than just using an ISO file without checking it at all.
Image Credit: Eduardo Quagliato on Flickr