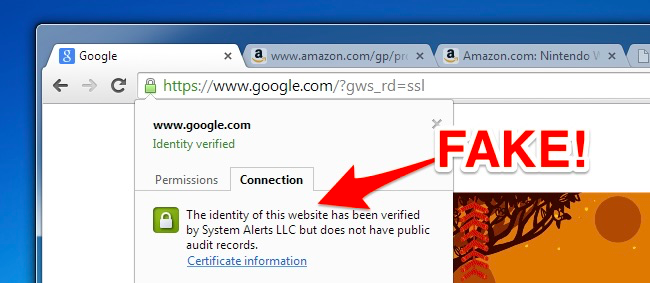
Dangerous root certificates are a serious problem. From Lenovo's Superfish to Dell's eDellRoot and a number of other certificates installed by adware programs, your computer's manufacturer or a program you installed may have added a certificate that opens you to attack. Here's how to check if your certificates are clean.
In the past, this hasn't been an easy process. However, a new Microsoft tool can quickly scan your system and inform you if any certificates are installed that aren't normally trusted by Microsoft. It's an especially good idea to run this on new computers to check if they're open to attack out of the box.
Update: The sigcheck tool didn't work on Windows 7 at the time of publishing, but Microsoft has updated the tool and it should now work properly on all versions of Windows. So if you couldn't get it to work before, try it again now!
How to Check
We'll be using the Sigcheck tool provided by Microsoft for this. It's part of the SysInternals suite of tools, which was updated with this feature at the beginning of 2016.
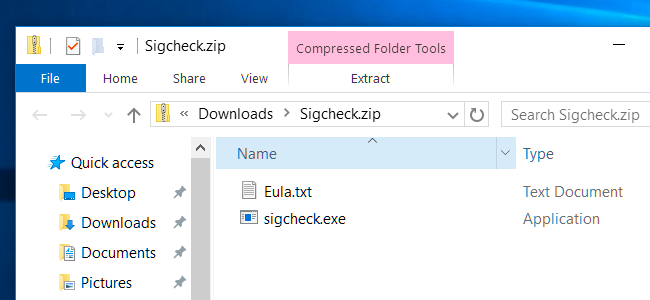
To get started, download Sigcheck from Microsoft. Open the downloaded .zip file and extract the sigcheck.exe file. For example, you could just drag and drop the file to your desktop.
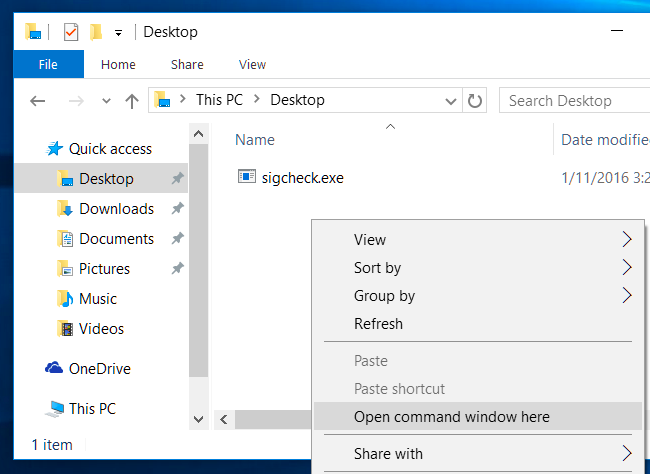
Navigate to the folder containing the sigcheck.exe file you just extracted. For example, if you put it on your desktop, open the Desktop folder in File Explorer (or Windows Explorer, if you're on Windows 7). Press and hold the Shift key on your keyboard, right-click in the File Explorer window, and select "Open command window here".
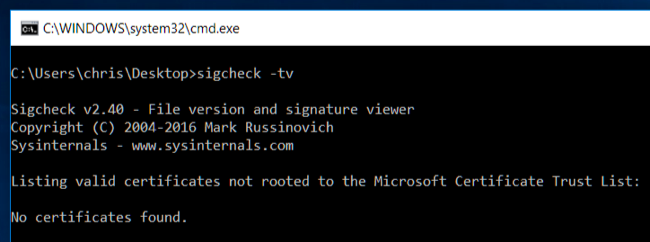
Type the following command at the command prompt and press Enter:
sigcheck -tv
Sigcheck will download a list of trusted certificates from Microsoft and compare it to the certificates installed on your computer. If there are any certificates on your computer that aren't on the "Microsoft Certificate Trust List", you'll see them listed here. If everything is good and you don't have any rogue certificates, you'll see the "No certificates found" message.
Help, I Found a Bad Certificate!
If the sigcheck application lists one or more certificates after you run the command and you're not sure what they are, you can try performing a web search for their names to find out what they are and how they got there.
Removing them manually isn't necessarily the best idea. If the certificate was installed by a program running on your computer, that program could just reinstall the certificate after you remove it. You really want to identify which program is causing the problem and get rid of that program entirely. How you do this depends on the program. Ideally, you could just uninstall it from the "Uninstall a program" control panel. Adware programs may dig their hooks in and need special cleaning tools. Even manufacturer-installed "legitimate" software like Dell's eDellRoot and Superfish needed special uninstallation tools you had to download to remove them. Do a search online for the best way to remove the precise certificate you see installed because the ideal method will be different for each one.
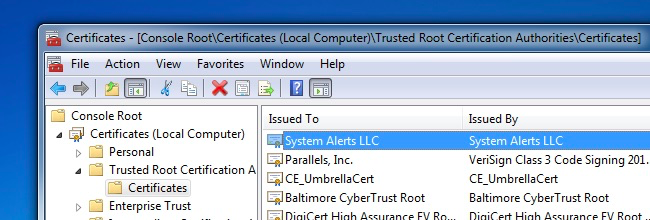
However, if you really want to -- or if you can't find specific instructions -- you can remove the certificate by hand with Windows' certificate management console. To open it, perform a search for "certificates" in your Start menu or Start screen and click the "Manage computer certificates" link. You could also press Windows Key + R to launch the Run dialog, type "certmgr.msc" into the Run dialog, and press Enter.
Root certificates are located under Trusted Root Certification Authorities\Certificates in this window. If there's a certificate you need to remove, you can locate it in this list, right-click it, and select the "Delete" option.
Be careful, though: don't remove any legitimate certificates! The vast majority of the certificates here are legitimate and part of Windows itself. Be careful when removing certificates and be sure you're removing the correct one.
Prior to the modification to the sigcheck tool above, there was no easy way to check for bad certificates that shouldn't be there. It would be nice if there were a friendlier method than a Command Prompt command, but this is the best we can do for now.
Microsoft has announced it will be cracking down on software that behaves in this way. Applications that install insecure root certificates to perform man-in-the-middle attacks -- often for advertising -- will be flagged by Windows Defender and other tools and be automatically removed. That should help a bit when the next manufacturer-installed certificate is discovered.
Image Credit: Sarah Joy on Flickr