Jacob Zinicola
Contributing since May, 2014
-
6articles
About Jacob Zinicola
Jacob Zinicola has been a technology geek since the day he could spell "VIC 20". He spends about as much time trying to break things as he does fixing them. When not preoccupied with either of those, he's typically diving into the heat of a computer-generated battle or lost in some good sci-fi - or both at once, if he's lucky.
Latest Articles
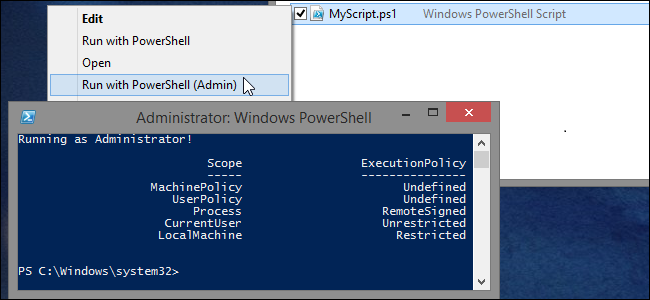
How to Configure Windows to Work with PowerShell Scripts More Easily
Windows and PowerShell have built-in security features and default configurations intended to prevent end-users from accidentally launching scripts in the course of their daily activities.
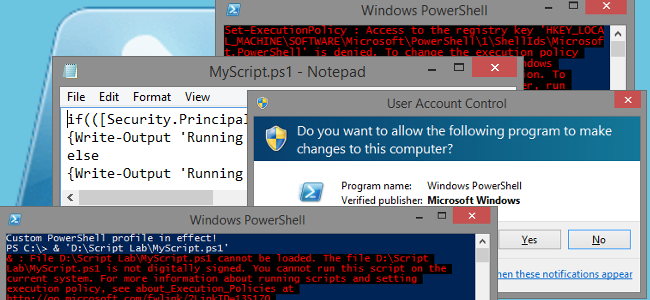
How to Use a Batch File to Make PowerShell Scripts Easier to Run
For several reasons, mostly security-related, PowerShell scripts aren't as easily portable and usable as batch scripts can be.
How Scopes Affect PowerShell Scripts
In batch scripts, changes to environment variables have a global impact to the current session by default.
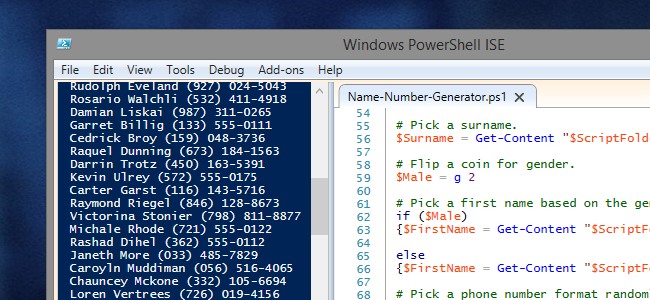
How to Generate Random Names & Phone Numbers with PowerShell
When you need a data set for testing or demonstration, and that set needs to represent Personally Identifiable Information (PII), you generally don't want to use real data that represents actual people.
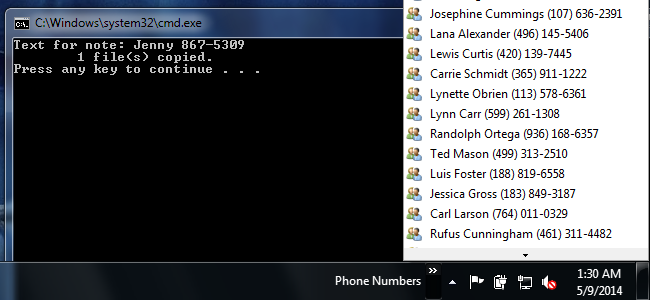
How to Put Short Notes in the Windows Taskbar
There are plenty of third-party programs and other widgets that may help you keep information close at hand.

Protect Your Data in the Cloud with TrueCrypt
With news of the NSA, GCHQ, big corporations, and anyone else with an Internet connection snooping through your online data these days, you can’t be too careful when it comes to protecting the stuff you put in the cloud.
