
Chris Hoffman
Contributing since August, 2010
-
2888articles
Page 37
About Chris Hoffman
Chris Hoffman is the former Editor-in-Chief of How-To Geek. Chris has personally written over 2,000 articles that have been read more than one billion times---and that's just here at How-To Geek.
With over a decade of writing experience in the field of technology, Chris has written for a variety of publications including The New York Times, Reader's Digest, IDG's PCWorld, Digital Trends, and MakeUseOf. Beyond the web, his work has appeared in the print edition of The New York Times (September 9, 2019) and in PCWorld's print magazines, specifically in the August 2013 and July 2013 editions, where his story was on the cover. He also wrote the USA's most-saved article of 2021, according to Pocket.
Chris was a PCWorld columnist for two years. He founded PCWorld's "World Beyond Windows" column, which covered the latest developments in open-source operating systems like Linux and Chrome OS. Beyond the column, he wrote about everything from Windows to tech travel tips.
The news he's broken has been covered by outlets like the BBC, The Verge, Slate, Gizmodo, Engadget, TechCrunch, Digital Trends, ZDNet, The Next Web, and Techmeme. Instructional tutorials he's written have been linked to by organizations like The New York Times, Wirecutter, Lifehacker, the BBC, CNET, Ars Technica, and John Gruber's Daring Fireball. His roundups of new features in Windows 10 updates have been called "the most detailed, useful Windows version previews of anyone on the web" and covered by prominent Windows journalists like Paul Thurrott and Mary Jo Foley on TWiT's Windows Weekly. His work has even appeared on the front page of Reddit.
Articles he's written have been used as a source for everything from books like Team Human by Douglas Rushkoff, media theory professor at the City University of New York's Queens College and CNN contributor, to university textbooks and even late-night TV shows like Comedy Central's @midnight with Chris Hardwick.
Starting in 2015, Chris attended the Computer Electronics Show (CES) in Las Vegas for five years running. At CES 2018, he broke the news about Kodak's "KashMiner" Bitcoin mining scheme with a viral tweet. A wave of negative publicity ensued, with coverage on BuzzFeed News, CNBC, the BBC, and TechCrunch. The company's project was later reportedly shut down by the U.S. Securities and Exchange Commission.
In addition to his extensive writing experience, Chris has been interviewed as a technology expert on TV news and radio shows. He gave advice on dark web scans on Miami's NBC 6, discussed Windows XP's demise on WGN-TV's Midday News in Chicago, and shared his CES experiences on WJR-AM's Guy Gordon Show in Detroit.
Chris also ran MakeUseOf's email newsletter for two years. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Latest Articles

Windows 10 Is Getting a Built-in Linux Kernel
Microsoft is adding a Linux kernel to Windows 10. Yes, you read that right. It will be updated via Windows Update.
Windows 10 Is Finally Getting a Real Command Line
The new Windows Terminal app is a break from the past. It features tabs, themes, and GPU-based text rendering.
How to Restore a Missing Battery Icon on Windows 10's Taskbar
Did the battery icon vanish from your Windows 10 laptop's taskbar? Here's how to get it back.

How to Schedule Sending an Email in Gmail
Gmail now lets you schedule sending emails for the future. You can even schedule an email for the year 2068! That's awfully confident of Google.

How to Watch Videos at Faster Speeds
Here's how to speed up videos---Netflix, YouTube, local video files with VLC, and anything you can stream in a browser.
Windows 10's "Check for Updates" Button Just Got Safer
Windows 10's "Check for Updates" button is now less dangerous.

Windows 10's Your Phone App Gets Android Notification Mirroring
Windows 10's Your Phone app now has Android phone notification mirroring. Microsoft recently added display mirroring for additional Android phones, too
Windows 10 Now Requires 12-16 GB More Storage
Windows 10's minimum storage requirement is going up from 16 GB or 20 GB to 32 GB.
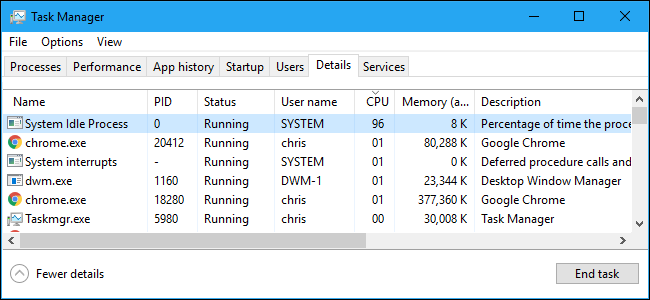
What Is "System Idle Process," and Why Is It Using So Much CPU?
Why is the System Idle Process on Windows always using all your CPU?

What Are Algorithms, and Why Do They Make People Uncomfortable?
We use the word "algorithm" a lot. But do we really know what we're talking about when we call something an "algorithm?"
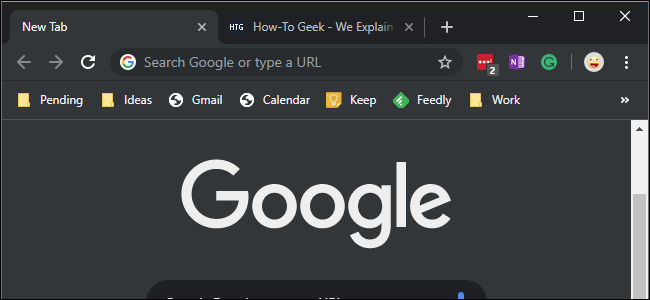
How to Enable Google Chrome's Dark Mode on Windows 10
Chrome now has a built-in dark mode on Windows 10 (and macOS, too). Here's how to enable it.
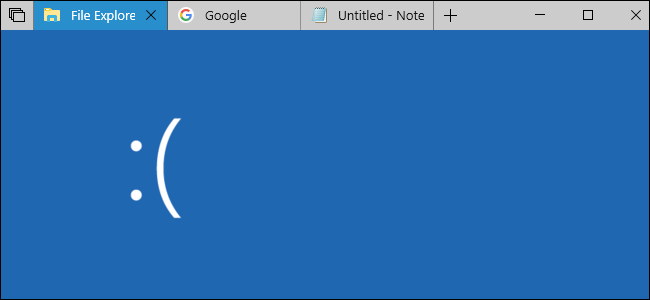
Nobody Wanted Microsoft’s Doomed Sets Feature (We Just Wanted Tabs)
Windows 10's Sets feature was doomed from day one. No one asked for Microsoft to make it so complicated. Sets was all about Edge, Bing, and things users didn't want.
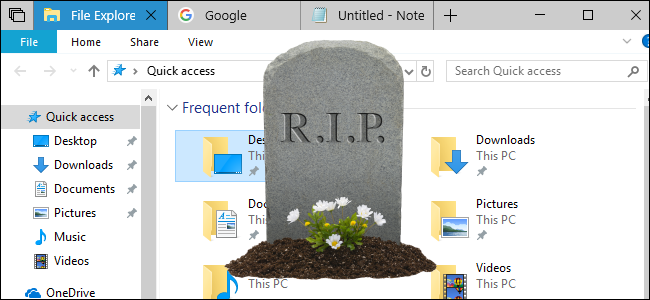
Windows 10's "Sets" App Tabs Are "No More"
Waiting for Windows 10's "Sets" tabs? Stop holding your breath---they appear cancelled. Can we please, please have File Explorer tabs already, Microsoft?

Windows Updates Are Breaking PCs With These Antivirus Programs
A recent Windows Update broke PCs with a variety of antivirus programs installed. This time it's Windows 7 PCs getting bit---not Windows 10 users.

How the UK's New Internet "Porn Block" Will Work
The UK will enact its "porn block" in three months. Websites will be blocked, Britons will be uploading copies of their passports---and minors will still have access to porn. Here are the details.

How to Stop Google's Sensorvault From Sharing Your Location With Law Enforcement
Google stores your location history in a database named SensorVault. Law enforcement can query it (with a warrant) to see a list of people near the location of a crime. Here's how to remove yourself from that database.

Alexa, Why Are Employees Looking at My Data?
Shocked Amazon has people listening to your Alexa recordings? They're not the only company looking at your data. And it could be much worse---employees at companies like Google and Facebook have used their access to stalk people.

How to Bypass Amazon's $25 Add-on Item Minimum (Without Alexa)
Finally! You can once again order add-on items from Amazon without a $25 minimum.

Here's How to Watch Game of Thrones’ Final Season Online
Game of Thrones season 8 begins this Sunday, April 14. Here's how to watch it without a cable TV subscription.

End of an Era: Adobe Shockwave Dies Today
RIP Adobe Shockwave, part of the web from 1995-2019 (No, not Adobe Shockwave Flash, that's something different!)
