
Chris Hoffman
Contributing since August, 2010
-
2888articles
Page 35
About Chris Hoffman
Chris Hoffman is the former Editor-in-Chief of How-To Geek. Chris has personally written over 2,000 articles that have been read more than one billion times---and that's just here at How-To Geek.
With over a decade of writing experience in the field of technology, Chris has written for a variety of publications including The New York Times, Reader's Digest, IDG's PCWorld, Digital Trends, and MakeUseOf. Beyond the web, his work has appeared in the print edition of The New York Times (September 9, 2019) and in PCWorld's print magazines, specifically in the August 2013 and July 2013 editions, where his story was on the cover. He also wrote the USA's most-saved article of 2021, according to Pocket.
Chris was a PCWorld columnist for two years. He founded PCWorld's "World Beyond Windows" column, which covered the latest developments in open-source operating systems like Linux and Chrome OS. Beyond the column, he wrote about everything from Windows to tech travel tips.
The news he's broken has been covered by outlets like the BBC, The Verge, Slate, Gizmodo, Engadget, TechCrunch, Digital Trends, ZDNet, The Next Web, and Techmeme. Instructional tutorials he's written have been linked to by organizations like The New York Times, Wirecutter, Lifehacker, the BBC, CNET, Ars Technica, and John Gruber's Daring Fireball. His roundups of new features in Windows 10 updates have been called "the most detailed, useful Windows version previews of anyone on the web" and covered by prominent Windows journalists like Paul Thurrott and Mary Jo Foley on TWiT's Windows Weekly. His work has even appeared on the front page of Reddit.
Articles he's written have been used as a source for everything from books like Team Human by Douglas Rushkoff, media theory professor at the City University of New York's Queens College and CNN contributor, to university textbooks and even late-night TV shows like Comedy Central's @midnight with Chris Hardwick.
Starting in 2015, Chris attended the Computer Electronics Show (CES) in Las Vegas for five years running. At CES 2018, he broke the news about Kodak's "KashMiner" Bitcoin mining scheme with a viral tweet. A wave of negative publicity ensued, with coverage on BuzzFeed News, CNBC, the BBC, and TechCrunch. The company's project was later reportedly shut down by the U.S. Securities and Exchange Commission.
In addition to his extensive writing experience, Chris has been interviewed as a technology expert on TV news and radio shows. He gave advice on dark web scans on Miami's NBC 6, discussed Windows XP's demise on WGN-TV's Midday News in Chicago, and shared his CES experiences on WJR-AM's Guy Gordon Show in Detroit.
Chris also ran MakeUseOf's email newsletter for two years. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Latest Articles

How to Stop Superhuman (and Other Apps) From Tracking Your Email Opens
Superhuman isn't the only app that can track your email opens. Here's how to stop everyone from seeing when you opened their emails.

Windows 10 Can Now Sync Android Notifications to Your PC
Hey Android users, Windows 10 now lets you sync your notifications to your PC. This feature was previously being tested with Insiders, but is now available to everyone.

Windows 10 20H1 Will Let You Drag and Drop With Your Eyes
Windows 10's latest 20H1 insider build lets you drag and drop with your eyes, tap your PC's touch screen to control your smartphone, and more.

Why Did Your iPhone Beep or Vibrate? Here's How to Find Out
Has your iPhone ever vibrated or beeped---but there were no notifications when you looked at the screen? Here's why that can happen.

How to Check If Apple Has Recalled Your MacBook (For Free Repairs)
Apple keeps recalling MacBooks. Here's how to check if your MacBook has been recalled---and is eligible for some free repairs.

How to Export and Import Your Linux Systems on Windows 10
Windows 10 now lets you export an installed Linux environment to a TAR file and import it on other computers. Here's how.

Valve Now Says Steam Will "Likely" Support Ubuntu 19.10
Valve says that Steam will "likely" support Ubuntu 19.10 after all. However, Steam may start officially recommending other Linux distributions (not just Ubuntu) in the future.

How to Stop Chrome (or Edge) From Taking Over Your Media Keys
Google Chrome now uses your media keys to control websites like YouTube. That gets in the way if you're using them for something else, like Spotify---so here's how to disable that.
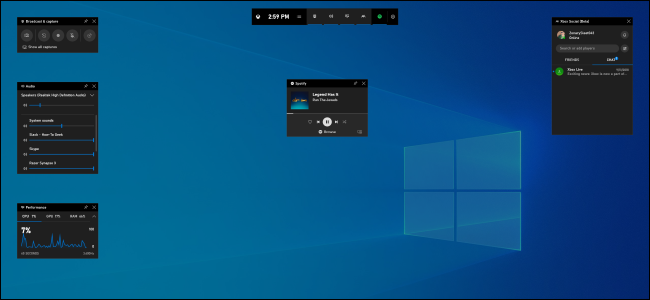
6 Great Features in Windows 10's New Game Bar
Windows 10's new game bar is a full-featured PC gaming overlay with application volume controls, performance monitoring, and even Spotify integration.

How to Disable "Reserved Storage" on Windows 10
Windows 10's May 2019 Update will now "reserve" 7 GB of storage on new PCs (and fresh installs.) Here's how it works---and how to disable it.

Steam Won't Support Ubuntu 19.10 and Future Releases
Steam won't officially support Ubuntu 19.10 and future versions of the popular Linux distro. Instead, Valve will be recommending a different Linux distribution. Here's what you need to know.
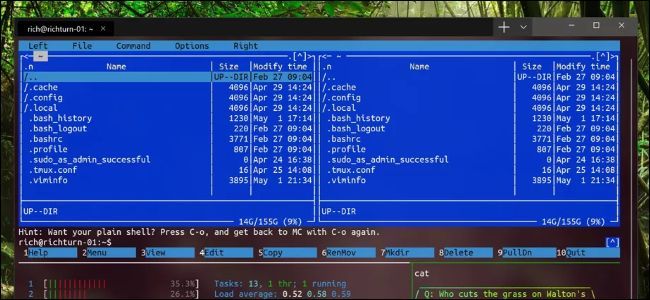
Microsoft's New Windows Terminal Is Now Available
Windows 10's new Terminal application is finally here! Here's how you can download it right now.
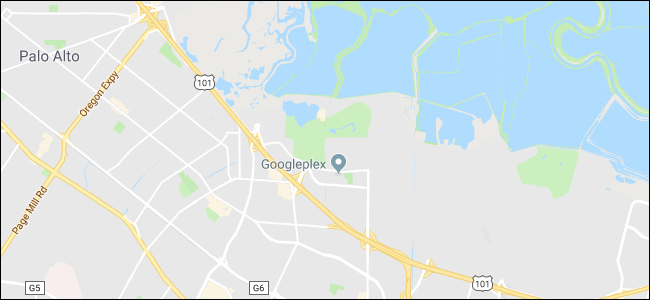
How to Report a Fake Business Listing on Google Maps
Noticed a fake business listing on Google Maps? Report it and get it removed. You'll be doing everyone a big favor. Here's how.

How to Report Phishing and Malicious Websites in Google Chrome
Google's new Chrome extension lets you report phishing and other "suspicious websites" in Chrome. Here's how.
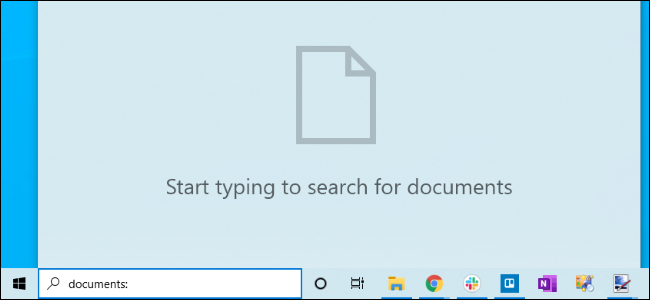
How to Search All Your PC's Files in Windows 10's Start Menu
Windows 10's May 2019 Update finally lets you search for files anywhere on your PC via the Start menu. It's off by default, though---here's how to power up your Start menu's file search.

Do You Really Need Antivirus For Your Smart TV?
Samsung recommends manually scanning your smart TV for malware "every few weeks." Do you really antivirus for your TV? (No---and if Samsung thinks you do, that's a good argument against buying a Samsung TV.)

How to Fix a Black Screen After Updating Windows 10
Some Windows 10 PCs are rebooting to a black screen after a recent Windows update. Here's how to fix it.

How to See Which Apps Are Using Your Webcam on Windows 10
Windows 10's May 2019 update lets you see exactly which applications are accessing your webcam---and which applications have in the past.

What's Going to Happen to Your Huawei or Honor Phone?
Here's what's going to happen to your existing Huawei or Honor phone.

Hardware Security Keys Keep Getting Recalled; Are They Safe?
Yubico just recalled some of its hardware security keys. Google had its own Titan security recall recently. So what's going on? Are hardware security keys safe?
