
Chris Hoffman
Contributing since August, 2010
-
2888articles
Page 25
About Chris Hoffman
Chris Hoffman is the former Editor-in-Chief of How-To Geek. Chris has personally written over 2,000 articles that have been read more than one billion times---and that's just here at How-To Geek.
With over a decade of writing experience in the field of technology, Chris has written for a variety of publications including The New York Times, Reader's Digest, IDG's PCWorld, Digital Trends, and MakeUseOf. Beyond the web, his work has appeared in the print edition of The New York Times (September 9, 2019) and in PCWorld's print magazines, specifically in the August 2013 and July 2013 editions, where his story was on the cover. He also wrote the USA's most-saved article of 2021, according to Pocket.
Chris was a PCWorld columnist for two years. He founded PCWorld's "World Beyond Windows" column, which covered the latest developments in open-source operating systems like Linux and Chrome OS. Beyond the column, he wrote about everything from Windows to tech travel tips.
The news he's broken has been covered by outlets like the BBC, The Verge, Slate, Gizmodo, Engadget, TechCrunch, Digital Trends, ZDNet, The Next Web, and Techmeme. Instructional tutorials he's written have been linked to by organizations like The New York Times, Wirecutter, Lifehacker, the BBC, CNET, Ars Technica, and John Gruber's Daring Fireball. His roundups of new features in Windows 10 updates have been called "the most detailed, useful Windows version previews of anyone on the web" and covered by prominent Windows journalists like Paul Thurrott and Mary Jo Foley on TWiT's Windows Weekly. His work has even appeared on the front page of Reddit.
Articles he's written have been used as a source for everything from books like Team Human by Douglas Rushkoff, media theory professor at the City University of New York's Queens College and CNN contributor, to university textbooks and even late-night TV shows like Comedy Central's @midnight with Chris Hardwick.
Starting in 2015, Chris attended the Computer Electronics Show (CES) in Las Vegas for five years running. At CES 2018, he broke the news about Kodak's "KashMiner" Bitcoin mining scheme with a viral tweet. A wave of negative publicity ensued, with coverage on BuzzFeed News, CNBC, the BBC, and TechCrunch. The company's project was later reportedly shut down by the U.S. Securities and Exchange Commission.
In addition to his extensive writing experience, Chris has been interviewed as a technology expert on TV news and radio shows. He gave advice on dark web scans on Miami's NBC 6, discussed Windows XP's demise on WGN-TV's Midday News in Chicago, and shared his CES experiences on WJR-AM's Guy Gordon Show in Detroit.
Chris also ran MakeUseOf's email newsletter for two years. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Latest Articles

Windows 10 Will Soon Show Edge Browser Tabs in Alt+Tab
Windows 10 will soon show all your browser tabs when you Alt+Tab. Here's what to expect.

PSA: All Apps Can Read Your iPhone and Android Clipboard
TikTok isn't the only app silently reading your clipboard in the background. Any app on your phone can read your clipboard. Apple's iOS 14 update just drew attention to an existing privacy problem.
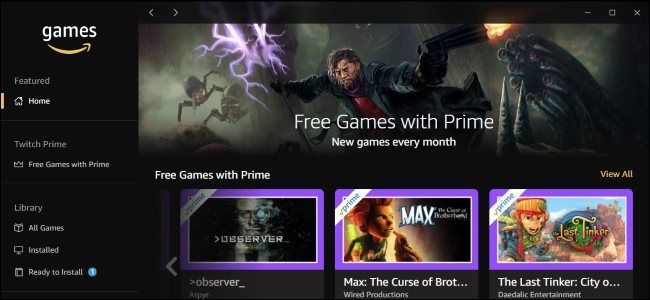
How to Download the Amazon Games App for Twitch Prime Games
Amazon offers free games to Amazon Prime subscribers every month. The Amazon Games App is the best way to download and play them. Here's how to get it.

How to Stop Slack Notifications on the Weekend
Slack finally lets you automatically stop notifications on your days off. Here's how.
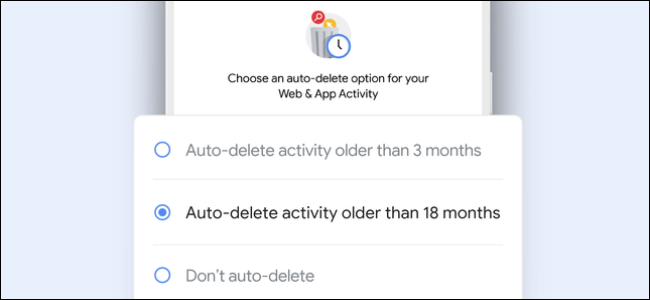
How to Make Google Auto-Delete Your Web and Location History
Google now automatically deletes your activity after 18 months to protect your privacy---but only for new users. Here's how to enable this privacy feature on your Google account today.

How the Mac Will Switch From Intel to Apple's Own ARM Chips
Apple is ditching Intel CPUs for its own ARM chips, which it calls "Apple Silicon." Here's everything you need to know. (New Macs will be able to install and run iPhone and iPad apps!)

How to Open Microsoft Word Documents Without Word
Need to open a Word document, but don't have Word installed? Here are your options.

How to Use Windows 10's "Fresh Start" on the May 2020 Update
Microsoft moved Windows 10's "Fresh Start" feature in the May 2020 Update. Here's where to find it.

How to Always Show Full URLs in Google Chrome
Want to see full URLs in Google Chrome? Here's now to enable the new "Always show full URLs" option in Chrome 83.

How to Directly Link to Text on a Web Page in Chrome
This awesome bookmarklet lets you create links directly to text on a web page in Chrome. It takes advantage of Chrome's awesome new "scroll to text fragment" feature for easy sharing.
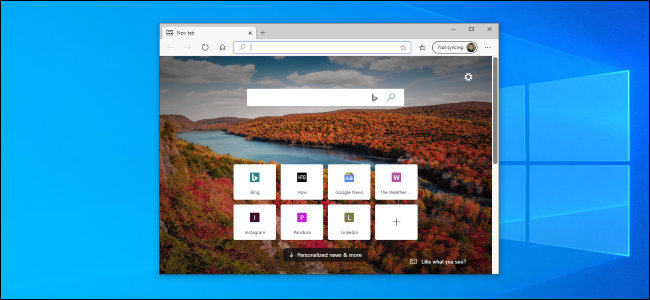
What You Need to Know About the New Microsoft Edge Browser
Windows Update will soon install a new web browser on your Windows 10 PC. Here's what you need to know about the new Microsoft Edge.
How to Uninstall Windows 10's May 2020 Update
Are you experiencing problems with Windows 10's May 2020 Update? Here's how to uninstall it---or any other big Windows 10 update.
How to Install Windows 10's May 2020 Update
Windows 10's May 2020 Update is here now, but Windows Update may not offer it for a few more weeks Here's how to install it right now.
What's New in Windows 10's May 2020 Update, Available Now
Windows 10's next update is nearly done. Here's what to expect from Windows 10's 2004 update.

How to Automatically Translate a Web Page in Microsoft Edge
The new Microsoft Edge has built-in automatic translation of web pages, just like Google Chrome does. Here's how to use it.
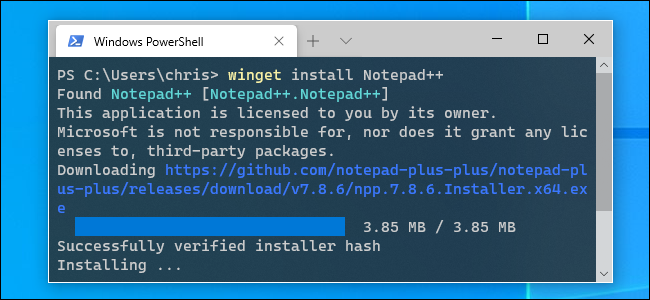
How to Use Windows 10's Package Manager, "winget"
Windows 10 now has a Linux-style package manager named "winget." Here's how you can use it today.
Microsoft Will Merge UWP and Win32 Apps With Project Reunion
Microsoft has a big new plan to merge UWP and Win32 apps on Windows 10. Meet Project Reunion.

Windows 10 Is Getting Graphical Linux Apps With GPU Support
Graphical Linux desktop apps with GPU support are coming to Windows 10. Yes, you read that right.

Windows 10's PowerToys Get a Launcher and Keyboard Remapper
Windows 10's PowerToys just got even better with an application launcher and keyboard shortcut manager.

Microsoft Edge Is Getting a Web Search Sidebar
Microsoft Edge will soon take better advantage of wide-screen monitors, presenting contextual search results in a sidebar instead of a new tab.
