
Chris Hoffman
Contributing since August, 2010
-
2888articles
Page 22
About Chris Hoffman
Chris Hoffman is the former Editor-in-Chief of How-To Geek. Chris has personally written over 2,000 articles that have been read more than one billion times---and that's just here at How-To Geek.
With over a decade of writing experience in the field of technology, Chris has written for a variety of publications including The New York Times, Reader's Digest, IDG's PCWorld, Digital Trends, and MakeUseOf. Beyond the web, his work has appeared in the print edition of The New York Times (September 9, 2019) and in PCWorld's print magazines, specifically in the August 2013 and July 2013 editions, where his story was on the cover. He also wrote the USA's most-saved article of 2021, according to Pocket.
Chris was a PCWorld columnist for two years. He founded PCWorld's "World Beyond Windows" column, which covered the latest developments in open-source operating systems like Linux and Chrome OS. Beyond the column, he wrote about everything from Windows to tech travel tips.
The news he's broken has been covered by outlets like the BBC, The Verge, Slate, Gizmodo, Engadget, TechCrunch, Digital Trends, ZDNet, The Next Web, and Techmeme. Instructional tutorials he's written have been linked to by organizations like The New York Times, Wirecutter, Lifehacker, the BBC, CNET, Ars Technica, and John Gruber's Daring Fireball. His roundups of new features in Windows 10 updates have been called "the most detailed, useful Windows version previews of anyone on the web" and covered by prominent Windows journalists like Paul Thurrott and Mary Jo Foley on TWiT's Windows Weekly. His work has even appeared on the front page of Reddit.
Articles he's written have been used as a source for everything from books like Team Human by Douglas Rushkoff, media theory professor at the City University of New York's Queens College and CNN contributor, to university textbooks and even late-night TV shows like Comedy Central's @midnight with Chris Hardwick.
Starting in 2015, Chris attended the Computer Electronics Show (CES) in Las Vegas for five years running. At CES 2018, he broke the news about Kodak's "KashMiner" Bitcoin mining scheme with a viral tweet. A wave of negative publicity ensued, with coverage on BuzzFeed News, CNBC, the BBC, and TechCrunch. The company's project was later reportedly shut down by the U.S. Securities and Exchange Commission.
In addition to his extensive writing experience, Chris has been interviewed as a technology expert on TV news and radio shows. He gave advice on dark web scans on Miami's NBC 6, discussed Windows XP's demise on WGN-TV's Midday News in Chicago, and shared his CES experiences on WJR-AM's Guy Gordon Show in Detroit.
Chris also ran MakeUseOf's email newsletter for two years. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Latest Articles

How to Turn Off Your Webcam and Microphone on Zoom
PSA: Here's how to turn off your webcam and mute yourself on Zoom.

What's New in Windows 10's October 2020 Update (20H2), Available Now
Here's what to expect from Windows 10's 20H2 update in the fall. Spoiler; There are some big changes---like the removal of the System Control Panel---but it's largely full of bug fixes and polish.
How to Install Windows 10's October 2020 Update (20H2)
Windows 10's October 2020 Update is here. Want to get it without waiting? Here's how to install it.

Looking for a Netflix Free Trial? Try These Services Instead
Netflix no longer offers free trials, but there are still lots of ways to stream for free. Here are your options.

What 5G Means for Apple's iPhone 12
Apple's iPhone 12 supports 5G. So will you see blazing-fast speeds? And what does that mean for battery life? It's complicated.
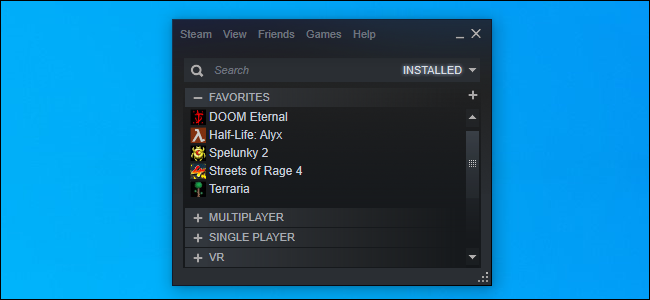
How to Reduce Steam's RAM Usage From 400 MB to 60 MB
Steam uses a lot of RAM. Here's how to cut it down to size.
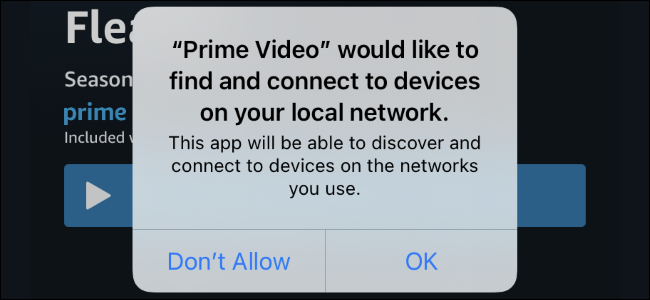
Why iPhone Apps Ask for "Devices on Your Local Network"
Here's why so many iPhone and iPad apps are asking to "find and connect to devices on your local network."

How to Stop Spotify's Automatic Startup on Windows 10
Spotify normally launches itself each time you sign into your Windows PC. Here's how to stop Spotify from automatically starting.
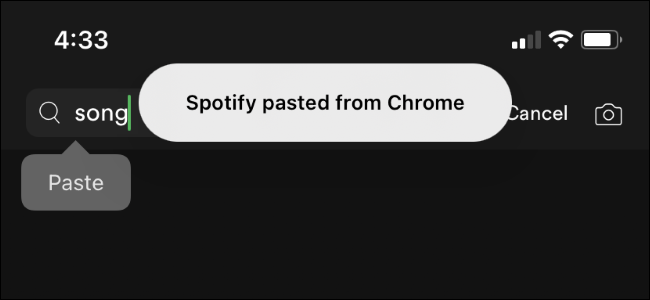
Why Are iPhone Apps "Pasting From" Other Apps?
Here's why your iPhone keeps saying apps are pasting from other apps---and why it's so important for privacy.

How to Install Linux
Want to install Linux on your PC? We'll walk you through everything you need to know.
How to Disable Steam's Chat Filter (or Customize It)
Steam has a built-in profanity filter, but you can disable it. You can even customize it, uploading a list of words you want Steam to filter. Here's how.

How to See What Packages and Mail You Have Coming Before It Arrives
The United States Postal Service, UPS, and FedEx all offer online dashboards where you can see exactly what packages (and letters, in the case of the US Postal Service) are scheduled to arrive at your address.

What Is an "Evil Maid" Attack, and What Does It Teach Us?
If an attacker has physical access to your devices, all bets are off. That's the lesson of the "evil maid" attack in cybersecurity.
How to Input Kaomoji on Windows 10 (╯°□°)╯︵ ┻━┻
Windows 10's latest update lets you easily insert kaomoji in any app. ( •_•)>⌐■-■ (⌐■_■)

How to Disable Private Wi-Fi MAC Addresses on iPhone and iPad
iOS 14 and iPadOS 14 use "Private Addresses" when connecting to WI-Fi networks. Here's how that works---and how to disable private addresses, if you need to do so.

How to Switch AirPods Automatically on iPhone, iPad, and Mac
Your AirPods will now automatically switch between your iPhone, iPad, and Mac. Here's how it works---and how to control it.

Custom App Icons Slow Down Your iPhone
Custom app icons look beautiful on an iPhone. There's just one problem: They'll slow your iPhone down. Here's what you should know before you spend time customizing your icons.
How to Control Smart Home Devices in the Control Center on iPhone or iPad
Apple's iOS 14 update adds new smart home controls to your iPhone's Control Center. Here's how to use them---and choose which shortcuts appear.
What Are the Orange and Green Dots on an iPhone or iPad?
Your iPhone (or iPad) will now tell show you whenever an app is accessing your microphone or camera. Here's how the new indicator dots work.

How to Turn On Spatial Audio for AirPods on iPhone or iPad
If you have AirPods Pro, you can take advantage of the new Spatial Audio feature. Here's how.
