
Chris Hoffman
Contributing since August, 2010
-
2888articles
Page 20
About Chris Hoffman
Chris Hoffman is the former Editor-in-Chief of How-To Geek. Chris has personally written over 2,000 articles that have been read more than one billion times---and that's just here at How-To Geek.
With over a decade of writing experience in the field of technology, Chris has written for a variety of publications including The New York Times, Reader's Digest, IDG's PCWorld, Digital Trends, and MakeUseOf. Beyond the web, his work has appeared in the print edition of The New York Times (September 9, 2019) and in PCWorld's print magazines, specifically in the August 2013 and July 2013 editions, where his story was on the cover. He also wrote the USA's most-saved article of 2021, according to Pocket.
Chris was a PCWorld columnist for two years. He founded PCWorld's "World Beyond Windows" column, which covered the latest developments in open-source operating systems like Linux and Chrome OS. Beyond the column, he wrote about everything from Windows to tech travel tips.
The news he's broken has been covered by outlets like the BBC, The Verge, Slate, Gizmodo, Engadget, TechCrunch, Digital Trends, ZDNet, The Next Web, and Techmeme. Instructional tutorials he's written have been linked to by organizations like The New York Times, Wirecutter, Lifehacker, the BBC, CNET, Ars Technica, and John Gruber's Daring Fireball. His roundups of new features in Windows 10 updates have been called "the most detailed, useful Windows version previews of anyone on the web" and covered by prominent Windows journalists like Paul Thurrott and Mary Jo Foley on TWiT's Windows Weekly. His work has even appeared on the front page of Reddit.
Articles he's written have been used as a source for everything from books like Team Human by Douglas Rushkoff, media theory professor at the City University of New York's Queens College and CNN contributor, to university textbooks and even late-night TV shows like Comedy Central's @midnight with Chris Hardwick.
Starting in 2015, Chris attended the Computer Electronics Show (CES) in Las Vegas for five years running. At CES 2018, he broke the news about Kodak's "KashMiner" Bitcoin mining scheme with a viral tweet. A wave of negative publicity ensued, with coverage on BuzzFeed News, CNBC, the BBC, and TechCrunch. The company's project was later reportedly shut down by the U.S. Securities and Exchange Commission.
In addition to his extensive writing experience, Chris has been interviewed as a technology expert on TV news and radio shows. He gave advice on dark web scans on Miami's NBC 6, discussed Windows XP's demise on WGN-TV's Midday News in Chicago, and shared his CES experiences on WJR-AM's Guy Gordon Show in Detroit.
Chris also ran MakeUseOf's email newsletter for two years. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Latest Articles

PSA: Gmail Has Your Old Chat Logs From Google Talk (and Hangouts)
Remember Google Talk? Google is storing your old chat logs from as long ago as 2005 in your Gmail account. Here's how to find it---and clear it.
Apple's iMessage Is Secure ... Unless You Have iCloud Enabled
Apple's iMessage isn't as private as you might think. There's a big hole in Apple's end-to-end encryption scheme, and it's called iCloud.

How to Back up Your Gmail to a Local Mailbox the Easy Way
Want a full local copy of your Gmail account that you can search and browse---all offline? Here's how to set it up.

Why SMS Text Messages Aren't Private or Secure
You may not want Facebook seeing every message you send, but standard SMS text messages aren't any better. In fact, they're even worse.

How Devices Use Wi-Fi to Determine Your Physical Location
Modern devices can find your precise physical location even without GPS---all by using Wi-Fi. Here's how that works.

How to Display Steam's Built-in FPS Counter in PC Games
Did you know Steam has a built-in FPS counter? Here's how to enable it. It works in Steam for Windows, Mac, and Linux.

How to Open an MBOX File (Using Mozilla Thunderbird)
Google Takeout offers your Gmail emails in the form of an MBOX file. Here's how to view the contents of an MBOX file on your computer.

How to Check If Signal Is Down
Is Signal down? Here's how to check. (Yes, it was down when we published this!)

Can You Use Signal Without Giving It Your Contacts?
Signal is all about privacy---but the encrypted chat app wants access to all your contacts. Here's why.

How to Stop Signal From Telling You When Your Contacts Join
If you're using Signal, you're probably getting a lot of notifications saying your contacts are joining. Here's how to hide these alerts.
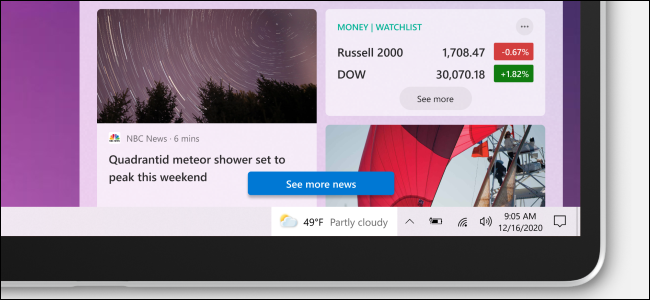
Your Windows 10 Taskbar Is About to Get News and Weather
Microsoft is about to put News and Weather right on your Windows 10 taskbar. Here's how it will work.
What Was the Windows Briefcase Used For, Anyway?
The Windows Briefcase was introduced in Windows 95 and was the Dropbox of its day.

HTTPS Is Almost Everywhere. So Why Isn't the Internet Secure Now?
Most web traffic online is now sent over an HTTPS connection, making it "secure.

How to Buy a Laptop for Linux
If you're buying a new laptop for Linux, you shouldn't just buy the Windows laptop you like and hope for the best---you should plan your purchase to ensure it will work well with Linux.
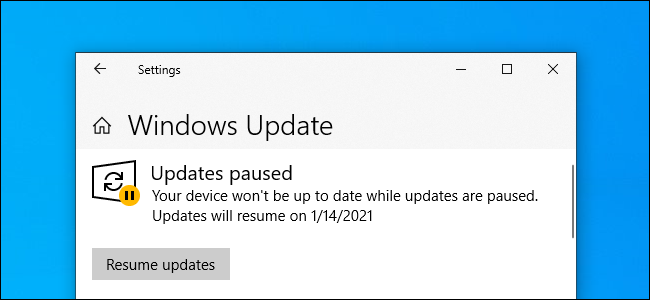
How to Pause Updates on Windows 10
Windows 10 lets you pause updates for up to 35 days, even if you're using Windows 10 Home. Here's how.

10 Hidden Gestures for Google Chrome on iPhone
Chrome for iPhone is packed with useful hidden features. Do you know all these gestures?
How to Check If Your PC Has the Latest Version of Windows 10
Most PCs don't have the latest version of Windows 10 installed. Does your PC have the latest software? Here's how to check.
What Is an "Optional Quality Update" on Windows 10?
Windows Update says an "optional quality update" is available right now. But should you install it? Here's what's going on.

How to See If an App Runs on an M1 Mac With Apple Silicon
Do all your Mac apps run properly on those new M1 Macs? Here's how to check before you buy one.

Can Websites See Your Physical Location?
Can websites see your physical location? Yes and no. Here's how it works, and how you can control it.
