Insecure Wi-Fi is the easiest way for people to access your home network, leech your internet, and cause you serious headaches with more malicious behavior. Read on as we show you how to secure your home Wi-Fi network.
Why Secure Your Network?
In a perfect world you could leave your Wi-Fi networks wide open to share with any passing Wi-Fi starved travelers who desperately needed to check their email or lightly use your network. In reality leaving your Wi-Fi network open create unnecessary vulnerability wherein non-malicious users can sponge up lots of our bandwidth inadvertently and malicious users can pirate using our IP as cover, probe your network and potentially get access to your personal files, or even worse. What does even worse look like? In the case of Matt Kostolnik it looks like a year of hell as your crazy neighbor, via your hacked Wi-Fi network, uploads child pornography in your name using your IP address and sends death threats to the Vice President of the United States. Mr. Kolstolnik was using crappy and outdated encryption with no other defensive measures in place; we can only imagine that a better understanding of Wi-Fi security and a little network monitoring would have saved him a huge headache.
Securing Your Wi-Fi Network
Securing your Wi-Fi network is a multi-step affair. You need to weigh each step and decide if the increased security is worth the sometimes increased hassle accompanying the change. To help you weigh the benefits and drawbacks of each step we've divided them up into relative order of importance as well as highlighted the benefits, the drawbacks, and the tools or resources you can use to stress test your own security. Don't rely on our word that something is useful; grab the available tools and try to kick down your own virtual door. Note: It would be impossible for us to include step-by-step instructions for every brand/model combination of routers out there. Check the brand and model number on your router and download the manual from the manufacturer's website in order to most effectively follow our tips. If you have never accessed your router's control panel or have forgotten how, now is the time to download the manual and give yourself a refresher. Update Your Router and Upgrade to Third Party Firmware If Possible: At minimum you need to visit the web site for the manufacture of your router and make sure there are no updates. Router software tends to be pretty stable and releases are usually few and far between. If your manufacturer has released an update (or several) since you purchased your router it's definitely time to upgrade. Even better, if you're going to go through the hassle of updating, is to update to one of the awesome third-party router firmwares out there like DD-WRT or Tomato. You can check out our guides to installing DD-WRT here and Tomato here. The third party firmwares unlock all sorts of great options including an easier and finer grain control over security features. The hassle factor for this modification is moderate. Anytime you flash the ROM on your router you risk bricking it. The risk is really small with third-party firmware and even smaller when using official firmware from your manufacturer. Once you've flashed everything the hassle factor is zero and you get to enjoy a new better, faster, and more customizable router. Change Your Router's Password: Every router ships with a default login/password combination. The exact combination varies from model to model but it's easy enough to look up the default that leaving it unchanged is just asking for trouble. Open Wi-Fi combined with the default password is essentially leaving your entire network wide open. You can check out default password lists here, here, and here. The hassle factor for this modification is extremely low and it's foolish not to do it.
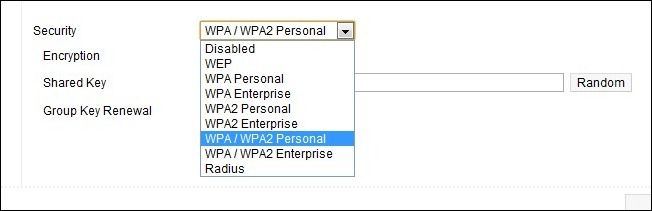
Turn On and/or Upgrade Your Network Encryption: In the above example we gave, Mr. Kolstolnik had turned on the encryption for his router. He made the mistake of selecting WEP encryption, however, which is the lowest encryption on the Wi-Fi encryption totem pole. WEP is easy to crack using freely available tools such as WEPCrack and BackTrack. If you happened to read the entire article about Mr. Kolstolnik's problems with his neighbors you'll note that it took his neighbor two weeks, according to the authorities, to break the WEP encryption. That's such a long span of time for such a simple task we have to assume that he also had to teach himself how to read and operate a computer too. Wi-Fi encryption comes in several flavors for home use such as WEP, WPA, and WPA2. In addition WPA/WPA2 can be further subdivided as WPA/WPA2 with TKIP (a 128-bit key is generated per packet) and AES (a different 128-bit encryption). If possible you want to use WP2 TKIP/AES as AES is not as widely adopted as TKIP. Allowing your router to use both will enable to use the superior encryption when available. The only situation where upgrading the encryption of your Wi-Fi network may pose a problem is with legacy devices. If you have devices manufactured before 2006 it's possible that, without firmware upgrades or perhaps not at all, they will be unable to access any network but an open or WEP encrypted network. We've phased out such electronics or hooked them up to the hard LAN via Ethernet (we're looking at you original Xbox). The hassle factor for this modification is low and--unless you have a legacy Wi-Fi device you can't live without--you won't even notice the change. Changing/Hiding Your SSID: Your router shipped with a default SSID; usually something simple like "Wireless" or the brand name like "Netgear". There's nothing wrong with leaving it set as the default. If you live in a densely populated area, however, it would make sense to change it to something different in order to distinguished it from the 8 "Linksys" SSIDs you see from your apartment. Don't change it to anything that identifies you. Quite a few of our neighbors have unwisely changed their SSIDs to things like APT3A or 700ElmSt . A new SSID should make it easier for you to identify your router from the list and not easier for everyone in the neighborhood to do so. Don't bother hiding your SSID. Not only does it provide no boost in security but it makes your devices work harder and burn more battery life. We debunked the hidden SSID myth here if you're interested in doing more detailed reading. The short version is this: even if you "hide" your SSID it is still being broadcast and anyone using apps like inSSIDer or Kismet can see it. The hassle factor for this modification is low. All you'll need to do is change your SSID once (if at all) to increase recognition in a router-dense environment.
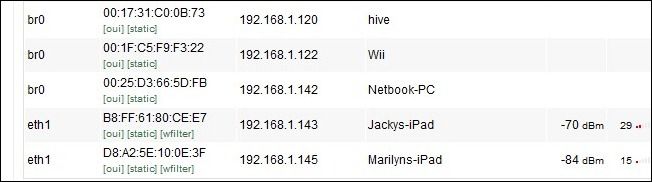
Filter Network Access by MAC Address: Media Access Control addresses, or MAC address for short, is a unique ID assigned to every network interface you'll encounter. Everything you can hook up to your network has one: your XBOX 360, laptop, smartphone, iPad, printers, even the Ethernet cards in your desktop computers. The MAC address for devices is printed on a label affixed to it and/or on the box and documentation that came with the device. For mobile devices you can usually find the MAC address within the menu system (on the iPad, for example, it's under the Settings --> General --> About menu and on Android phones you'll find it Settings --> About Phone --> Status menu). One of the easiest ways to check the MAC addresses of your devices, besides simply reading the label on them, is to check out the MAC list on your router after you've upgraded your encryption and logged all your devices back in. If you've just changed your password you can be nearly certain the iPad you see attached to the Wi-Fi node is yours. Once you have all the MAC addresses you can set up your router to filter based on them. Then it won't be enough for a computer to be in range of the Wi-Fi node and have the password/break the encryption, the device intruding on the network will also need to have the MAC address of a device on your router's whitelist. Although MAC filtering is a solid way to increase your security it is possible for somebody to sniff your Wi-Fi traffic and then spoof the MAC address of their device to match one on your network. Using tools like Wireshark, Ettercap, and Nmap as well as the aforementioned BackTrack. Changing the MAC address on a computer is simple. In Linux it's two commands at the command prompt, with a Mac it's just about as easy, and under Windows you can use a simple app to swap it like Etherchange or MAC Shift. The hassle factor for this modification is moderate-to-high. If you use the same devices on your network over and over with little change up then it's a small hassle to set up the initial filter. If you frequently have guests coming and going that want to hop on your network it's a huge hassle to always be logging into your router and adding their MAC addresses or temporarily turning off the MAC filtering. One last note before we leave MAC addresses: if you're particularly paranoid or you suspect someone is messing around with your network you can run applications like AirSnare and Kismet to set up alerts for MACs outside your white list. Adjust the Output Power of Your Router: This trick is usually only available if you've upgraded the firmware to a third party version. Custom firmware allows you to dial up or down the output of your router. If you're using your router in a one bedroom apartment you can easily dial the power way down and still get a signal everywhere in the apartment. Conversely if the nearest house is 1000 feet away, you can crank the power up to enjoy Wi-Fi out in your hammock. The hassle factor for this modification is low; it's a one time modification. If your router doesn't support this kind of adjustment, don't sweat it. Lowering the output power of your router is just a small step that makes it necessary for someone to be physically closer to your router to mess with it. With good encryption and the other tips we've shared, such a small tweak has a relatively small benefit.
Once you've upgraded your router password and upgraded your encryption (let alone done anything else on this list) you've done 90% more than nearly every Wi-Fi network owner out there.
Congratulations, you've hardened your network enough to make almost everyone else look like a better target! Have a tip, trick, or technique to share? Let's hear about your Wi-Fi security methods in the comments.