Quick Links
You'll sometimes see MD5, SHA-1, or SHA-256 hashes displayed alongside downloads during your internet travels, but not really known what they are. These seemingly random strings of text allow you to verify files you download aren't corrupted or tampered with. You can do this with the commands built into Windows, macOS, and Linux.
How Hashes Work, and How They're Used for Data Verification
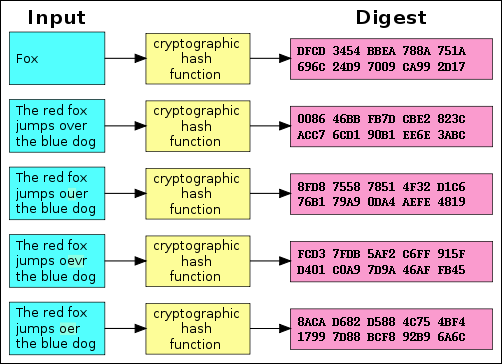
Hashes are the products of cryptographic algorithms designed to produce a string of characters. Often these strings have a fixed length, regardless of the size of the input data. Take a look at the above chart and you'll see that both "Fox" and "The red fox jumps over the blue dog" yield the same length output.
Now compare the second example in the chart to the third, fourth, and fifth. You'll see that, despite a very minor change in the input data, the resulting hashes are all very different from one another. Even if someone modifies a very small piece of the input data, the hash will change dramatically.
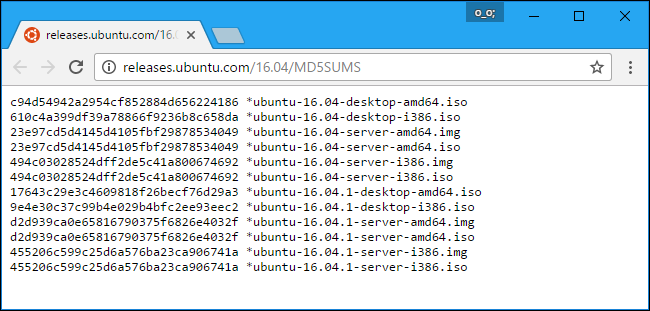
MD5, SHA-1, and SHA-256 are all different hash functions. Software creators often take a file download---like a Linux .iso file, or even a Windows .exe file---and run it through a hash function. They then offer an official list of the hashes on their websites.
That way, you can download the file and then run the hash function to confirm you have the real, original file and that it hasn't been corrupted during the download process. As we saw above, even a small change to the file will dramatically change the hash.
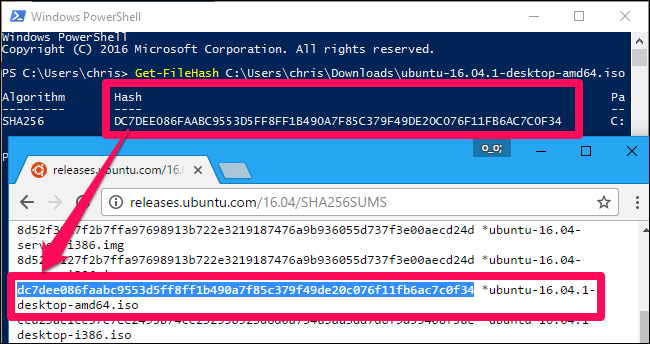
These can also be useful if you have a file you got from an unofficial source and you want to confirm that it's legitimate. Let's say you have a Linux .ISO file you got from somewhere and you want to confirm it hasn't been tampered with. You can look up the hash of that specific ISO file online on the Linux distribution's website. You can then run it through the hash function on your computer and confirm that it matches the hash value you'd expect it to have. This confirms the file you have is the exact same file being offered for download on the Linux distribution's website, without any modifications.
Note that "collisions" have been found with the MD5 and SHA-1 functions. These are multiple different files---for example, a safe file and a malicious file---that result in the same MD5 or SHA-1 hash. That's why you should prefer SHA-256 when possible.
How to Compare Hash Functions on Any Operating System
With that in mind, let's look at how to check the hash of a file you downloaded, and compare it against the one you're given. Here are methods for Windows, macOS, and Linux. The hashes will always be identical if you're using the same hashing function on the same file. It doesn't matter which operating system you use.
Windows
This process is possible without any third-party software on Windows thanks to PowerShell.
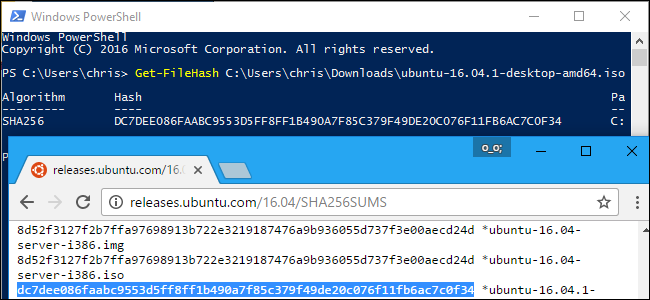
To get started, open a PowerShell window by launching the "Windows PowerShell" shortcut in your Start menu.
Run the following command, replacing "C:\path\to\file.iso" with the path to any file you want to view the hash of:
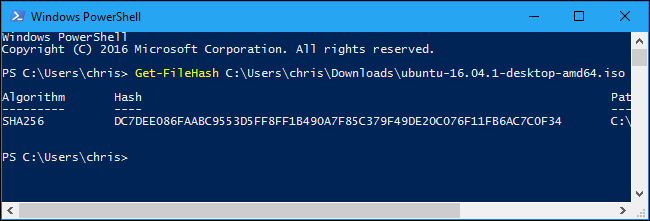
Get-FileHash C:\path\to\file.iso
It will take some time to generate the hash of the file, depending on the size of the file, the algorithm you're using, and the speed of the drive the file is on.
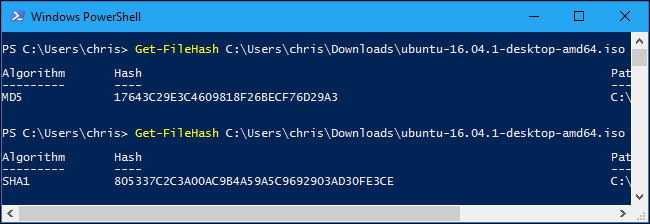
By default, the command will show the SHA-256 hash for a file. However, you can specify the hashing algorithm you want to use if you need an MD5, SHA-1, or other type of hash.
Run one of the following commands to specify a different hashing algorithm:
Get-FileHash C:\path\to\file.iso -Algorithm MD5
Get-FileHash C:\path\to\file.iso -Algorithm SHA1
Get-FileHash C:\path\to\file.iso -Algorithm SHA256
Get-FileHash C:\path\to\file.iso -Algorithm SHA384
Get-FileHash C:\path\to\file.iso -Algorithm SHA512
Get-FileHash C:\path\to\file.iso -Algorithm MACTripleDES
Get-FileHash C:\path\to\file.iso -Algorithm RIPEMD160
Compare the result of the hash function to the result you expected to see. If it's the same value, the file hasn't been corrupted, tampered with, or otherwise altered from the original.
macOS
macOS includes commands for viewing different types of hashes. To access them, launch a Terminal window. You'll find it at Finder > Applications > Utilities > Terminal.
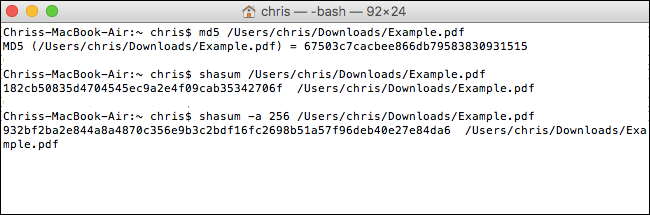
The md5 command shows the MD5 hash of a file:
md5 /path/to/file
The shasum command shows the SHA-1 hash of a file by default. That means the following commands are identical:
shasum /path/to/file
shasum -a 1 /path/to/file
To show the SHA-256 hash of a file, run the following command:
shasum -a 256 /path/to/file
Linux
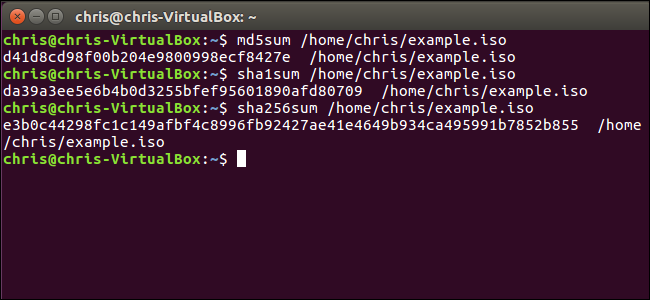
On Linux, access a Terminal and run one of the following commands to view the hash for a file, depending on which type of hash you want to view:
md5sum /path/to/file
sha1sum /path/to/file
sha256sum /path/to/file
Some Hashes are Cryptographically Signed for Even More Security
While hashes can help you confirm a file wasn't tampered with, there's still one avenue of attack here. An attacker could gain control of a Linux distribution's website and modify the hashes that appear on it, or an attacker could perform a man-in-the-middle attack and modify the web page in transit if you were accessing the website via HTTP instead of encrypted HTTPS.
That's why modern Linux distributions often provide more than hashes listed on web pages. They cryptographically sign these hashes to help protect against attackers that might attempt to modify the hashes. You'll want to verify the cryptographic signature to ensure the hash file was actually signed by the Linux distribution if you want to be absolutely sure the hash and file weren't tampered with.
Verifying the cryptographic signature is a more involved process. Read our guide to verifying Linux ISOs haven't been tampered with for full instructions.
Image Credit: Jorge Stolfi/Wikimedia