Quick Links
We've already covered installing Tomato on your router and how to connect to your home network with OpenVPN and Tomato. Now we are going to cover installing OpenVPN on your DD-WRT enabled router for easy access to your home network from anywhere in the world!
What is OpenVPN?
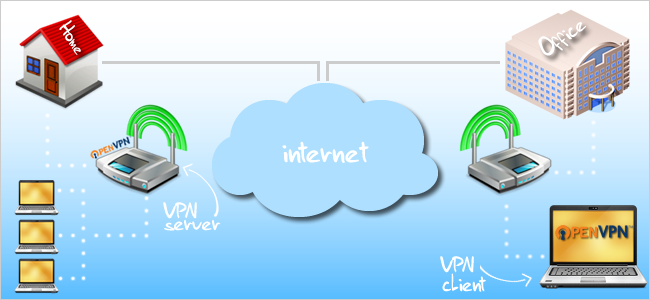
A virtual private network (VPN) is a trusted, secure connection between one local area network (LAN) and another. Think of your router as the middle man between the networks that you're connecting to. Both your computer and the OpenVPN server (your router in this case) "shake hands" using certificates that validate each other. Upon validation, both the client and server agree to trust each other and the client is then allowed access on the server's network.
Typically, VPN software and hardware cost a lot of money to implement. If you haven't guessed it already, OpenVPN is an open-source VPN solution that is (drum roll) free. DD-WRT, alongside OpenVPN, is a perfect solution for those who want a secured connection between two networks without having to open their wallet. Of course, OpenVPN won't work right out of the box. It takes a little bit of tweaking and configuring to get it just right. Not to worry though; we're here to make that process easier for you, so grab yourself a warm cup of coffee and let's get started.
For more information about OpenVPN, visit the official What Is OpenVPN? page.
Prerequisites
This guide assumes that you are currently running Windows 7 on your PC and that you're using an administrative account. If you're a Mac or Linux user, this guide will give you an idea of how things work, however, you may have to do a little more research on your own to get things perfect.
This guide also assumes that you own a Linksys WRT54GL and have a general understanding of VPN technology. It should serve as a basis for DD-WRT installation, but be sure to check out our official DD-WRT installation guide for an additional supplement.
Installing DD-WRT
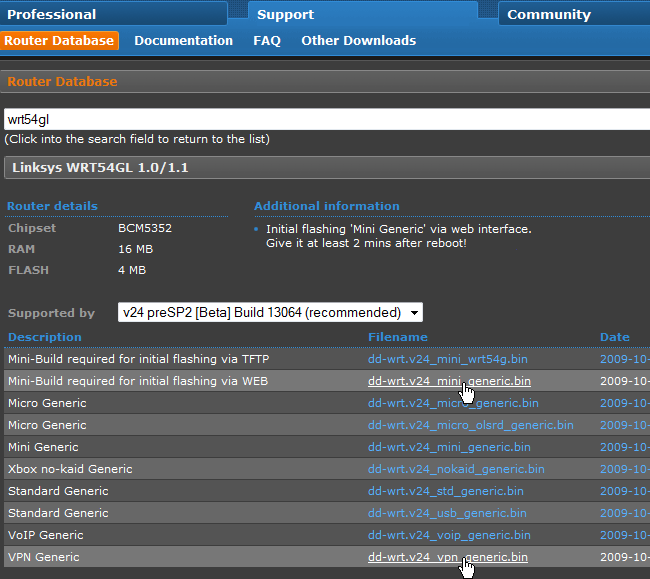
The team responsible for DD-WRT has done a great job making it easy for end users to discover router compatibility with their Router Database page. Start by typing in your router model (in our case WRT54GL) in the text field and watch search results appear instantly. Click your router once it's found.
You'll be brought to a new page that lists information about your model -- including hardware specs and different builds of DD-WRT. Download both the Mini-Generic build and VPN Generic build of DD-WRT (dd-wrt.v24_mini_generic.bin and dd-wrt.v24_vpn_generic.bin). Save these files to your computer.
It's a good idea to visit the DD-WRT Hardware-specific information page to look up detailed information about your router and DD-WRT. This page will explain exactly what you need to do before and after installing DD-WRT. For example, you must install the mini version of DD-WRT before installing DD-WRT VPN when upgrading from the stock Linksys firmware on a WRT54GL.
Also, be sure to do a hard reset (AKA a 30/30/30) before installing DD-WRT. Press the reset button on the back of your router for 30 seconds. Then, while still holding the reset button, unplug the power cable and leave it unplugged for 30 seconds. Finally, plug the power cable back in while still holding down the reset button for another 30 seconds. You should have held the power button for 90 seconds straight.
Now open up your browser and enter in your router's IP address (default is 192.168.1.1). You'll be prompted for a username and password. The defaults for a Linksys WRT54GL are "admin" and "admin".
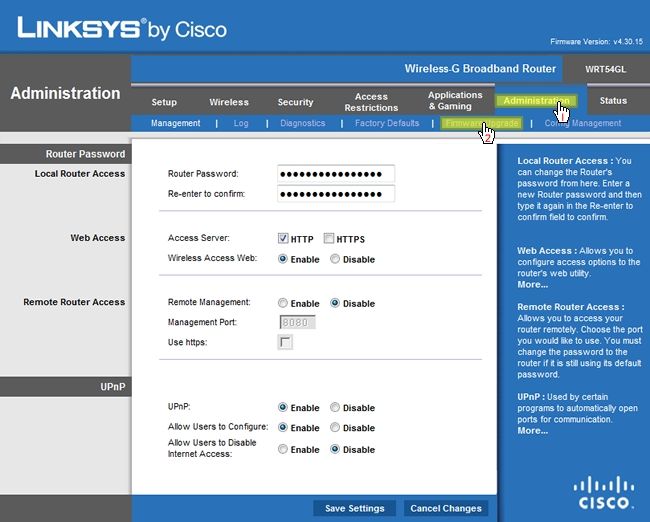
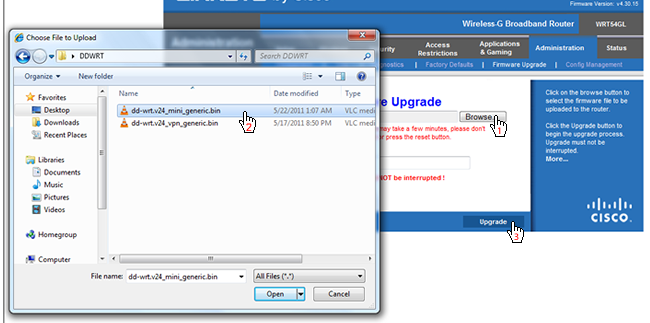
Click the Administration tab at the top. Next, click Firmware Upgrade as seen below.
Click the Browse button and navigate to the DD-WRT Mini Generic .bin file we downloaded earlier. Do not upload the DD-WRT VPN .bin file yet. Click the Upgrade button in the web interface. Your router will start installing DD-WRT Mini Generic, and should take less than a minute to complete.
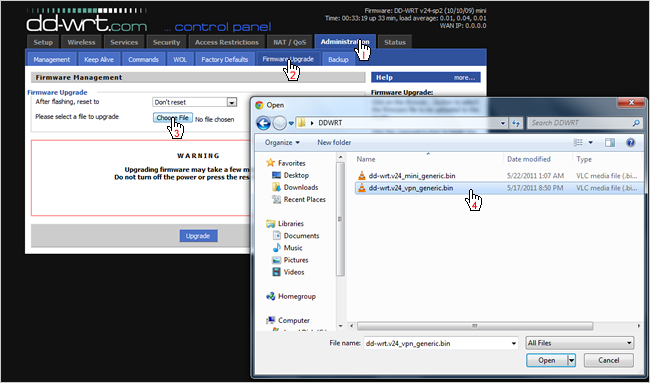
Alas! Your first sighting of DD-WRT. Once again, do another 30/30/30 reset as we did above. Then click the Administration tab at the top. You will be prompted with a username and password. The default username and password is "root" and "admin" respectively. After you've logged in, click the Firmware Upgrade sub-tab and click Choose File. Browse for the DD-WRT VPN file we downloaded earlier and click Open. The VPN version of DD-WRT will now begin to upload; be patient as it could take 2-3 minutes.
Installing OpenVPN
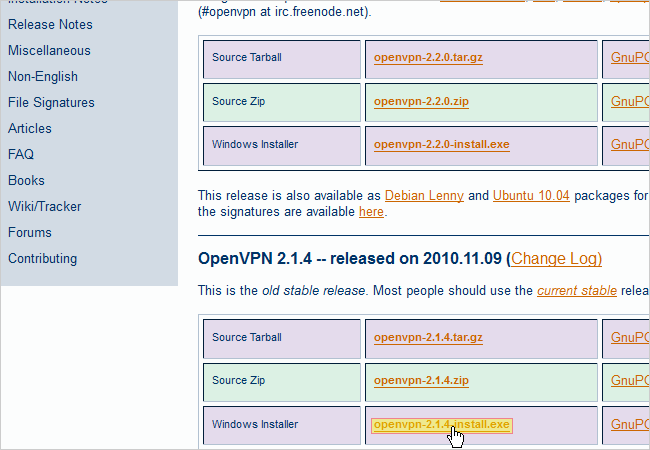
Now let's head over to OpenVPN's Downloads page and download the OpenVPN Windows Installer. In this guide, we'll be using the second latest version of OpenVPN called 2.1.4. The latest version (2.2.0) has a bug in it that would make this process even more complicated. The file we're downloading will install the OpenVPN program that allows you to connect to your VPN network, so be sure to install this program on any other computers that you want to act as clients (as we'll be seeing how to do that later). Save the openvpn-2.1.4-install .exe file to your computer.
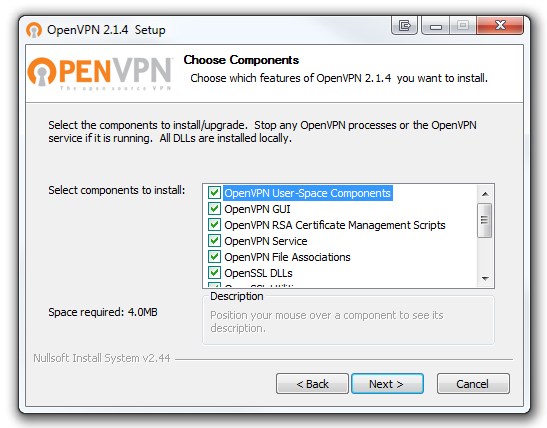
Navigate to the OpenVPN file we just downloaded and double click it. This will begin the installation of OpenVPN on your computer. Run through the installer with all the defaults checked. During the installation, a dialog box will pop up asking to install a new virtual network adapter called TAP-Win32. Click the Install button.
Creating the Certificates and Keys
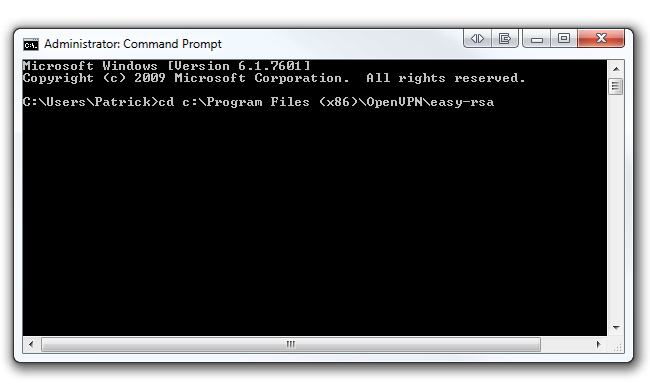
Now that you have OpenVPN installed on your computer, we have to start creating the certificates and keys to authenticate devices. Click the Windows Start button and navigate under Accessories. You'll see the Command Prompt program. Right click on it and click Run as administrator.
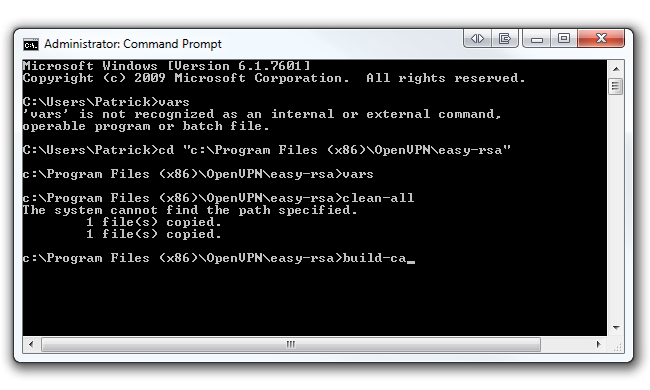
In the command prompt, type cd c:\Program Files (x86)\OpenVPN\easy-rsa if you're running 64-bit Windows 7 as seen below. Type cd c:\Program Files\OpenVPN\easy-rsa if you're running 32-bit Windows 7. Then hit Enter.
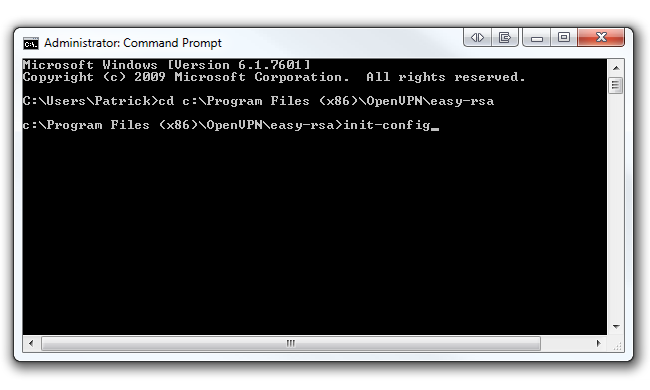
Now type init-config and hit Enter to copy two files called vars.bat and openssl.cnf into the easy-rsa folder. Keep your command prompt up as we'll be coming back to it shortly.
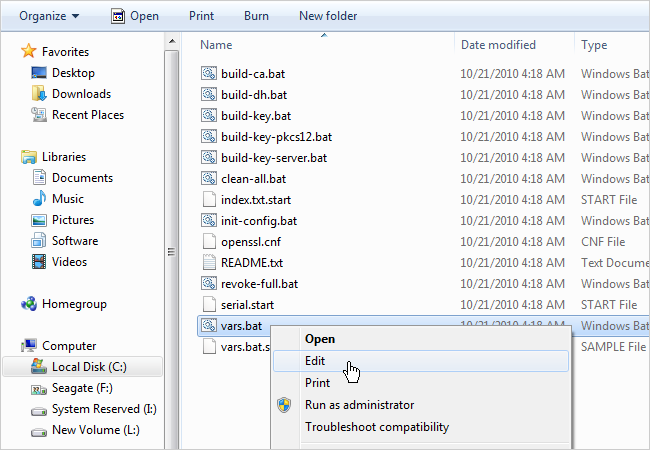
Navigate to C:\Program Files (x86)\OpenVPN\easy-rsa (or C:\Program Files\OpenVPN\easy-rsa on 32-bit Windows 7) and right click on the file called vars.bat. Click Edit to open it up in Notepad. Alternatively, we recommend opening this file with Notepad++ as it formats the text in the file much better. You can download Notepad++ from their homepage.
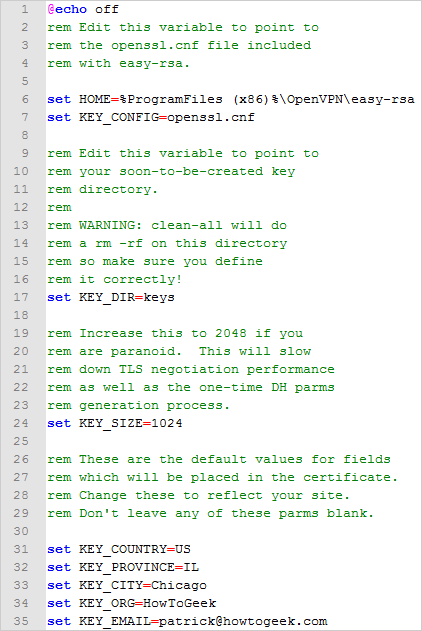
The bottom portion of the file is what we are concerned with. Starting at line 31, change the KEY_COUNTRY value, KEY_PROVINCE value, etc. to your country, province, etc. For example, we changed our province to "IL", city to "Chicago", org to "HowToGeek", and email to our own email address. Also, if you're running Windows 7 64-bit, change the HOME value in line 6 to %ProgramFiles (x86)%\OpenVPN\easy-rsa. Do not change this value if you're running 32-bit Windows 7. Your file should look similar to ours below (with your respective values, of course). Save the file by overwriting it once you're done editing.
Go back to your command prompt and type vars and hit Enter. Then type clean-all and hit Enter. Finally, type build-ca and hit Enter.
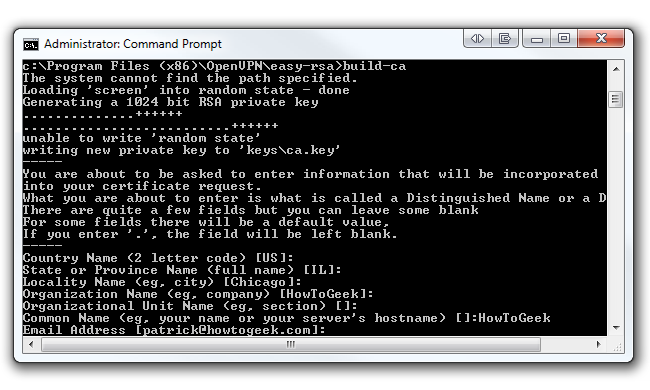
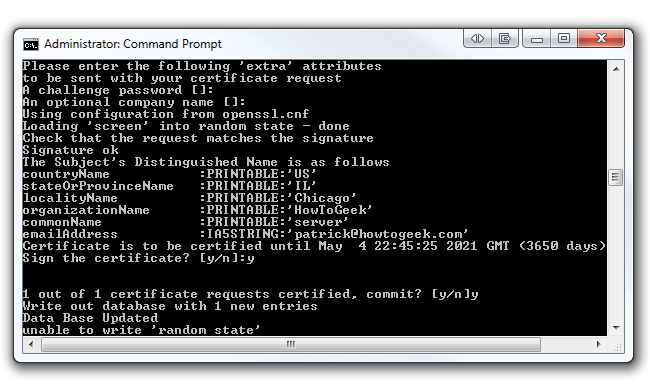
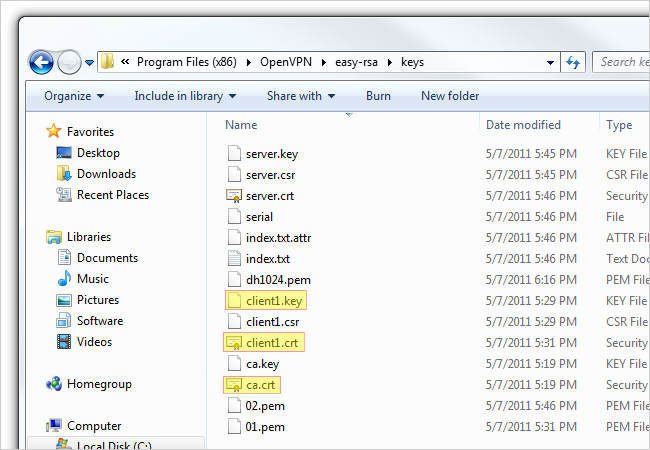
After executing the build-ca command, you will be prompted to enter in your Country Name, State, Locality, etc. Since we already set up these parameters in our vars.bat file, we can skip past these options by hitting Enter, but! Before you start slamming away at the Enter key, watch out for the Common Name parameter. You can enter anything in this parameter (i.e. your name). Just make sure you enter something. This command will output two files (a Root CA certificate and a Root CA key) in the easy-rsa/keys folder.
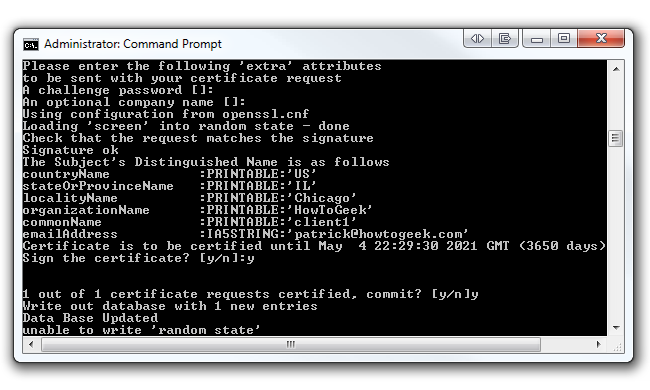
Now we're going to build a key for a client. In the same command prompt type build-key client1. You can change "client1" to anything you'd like (i.e. Acer-Laptop). Just be sure to enter the same name as the Common Name when prompted. Run through all the defaults like the last step we did (except for Common Name, of course). However, at the end you will be asked to sign the certificate and to commit. Type "y" for both and click Enter.
Also, don't worry if you received the "unable to write 'random state'" error. We've noticed that your certificates still get made without a problem. This command will output two files (a Client1 Key and a Client1 Certificate) in the easy-rsa/keys folder. If you want to create another key for another client, repeat the previous step, but be sure to change the Common Name.
The last certificate we'll be generating is the server key. In the same command prompt, type build-key-server server. You can replace "server" at the end of the command with anything you'd like (i.e. HowToGeek-Server). As always, be sure to enter the same name as the Common Name when prompted. Hit Enter and run through all the defaults except Common Name. At the end, type "y" to sign the certificate and commit. This command will output two files (a Server Key and a Server Certificate) in the easy-rsa/keys folder.
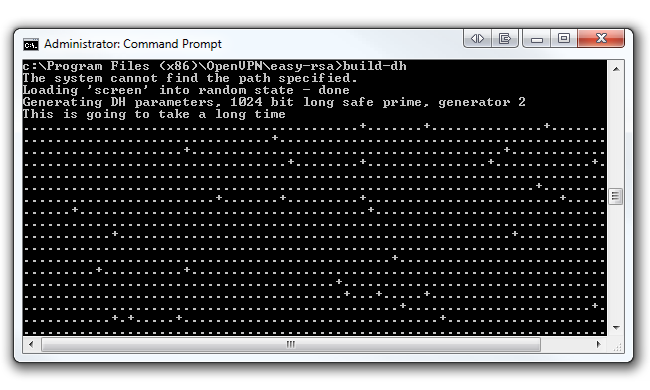
Now we have to generate the Diffie Hellman parameters. The Diffie Hellman protocol "allows two users to exchange a secret key over an insecure medium without any prior secrets". You can read more about Diffie Hellman on RSA's website.
In the same command prompt type build-dh. This command will output one file (dh1024.pem) in the easy-rsa/keys folder.
Creating the Configuration Files for the Client
Before we edit any configuration files, we should set up a dynamic DNS service. Use this service if your ISP issues you a dynamic external IP address every so often. If you have a static external IP address, skip down to the next step.
We suggest using DynDNS.com, a service that allows you to point a hostname (i.e. howtogeek.dyndns.org) to a dynamic IP address. It's important for OpenVPN to always know your network's public IP address, and by using DynDNS, OpenVPN will always know how to locate your network no matter what your public IP address is. Sign up for a free hostname and point it to your public IP address.
Now back to configuring OpenVPN. In Windows Explorer, navigate to C:\Program Files (x86)\OpenVPN\sample-config if you're running 64-bit Windows 7 or C:\Program Files\OpenVPN\sample-config if you're running 32-bit Windows 7. In this folder you will find three sample configuration files; we're only concerned with the client.ovpn file.
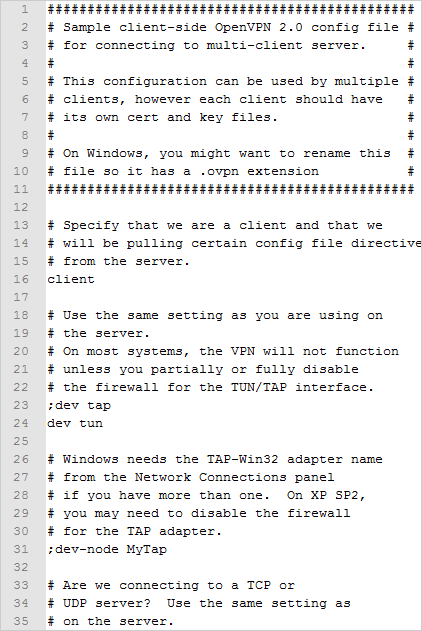
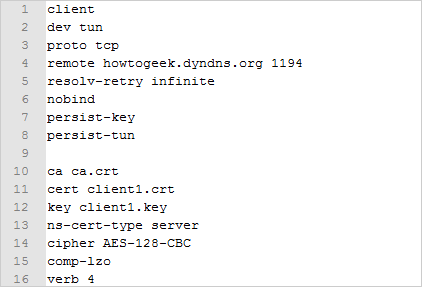
Right click on client.ovpn and open it with Notepad or Notepad++. You'll notice your file will look like the picture below:
However, we want our client.ovpn file to look similar to this picture below. Be sure to change the DynDNS hostname to your hostname in line 4 (or change it to your public IP address if you have a static one). Leave the port number to 1194 as it is the standard OpenVPN port. Also, be sure to change lines 11 and 12 to reflect the name of your client's certificate file and key file. Save this as new file .ovpn file in the OpenVPN/config folder.
Configuring DD-WRT's OpenVPN Daemon
The basic idea now is to copy the server certificates and keys we made earlier and paste them into the DD-WRT OpenVPN Daemon menus. Open up your browser again and navigate to your router. You should now have the DD-WRT VPN edition installed on your router. You will notice a new sub-tab under the Services tab called VPN. Click the Enable radio button under OpenVPN Daemon.
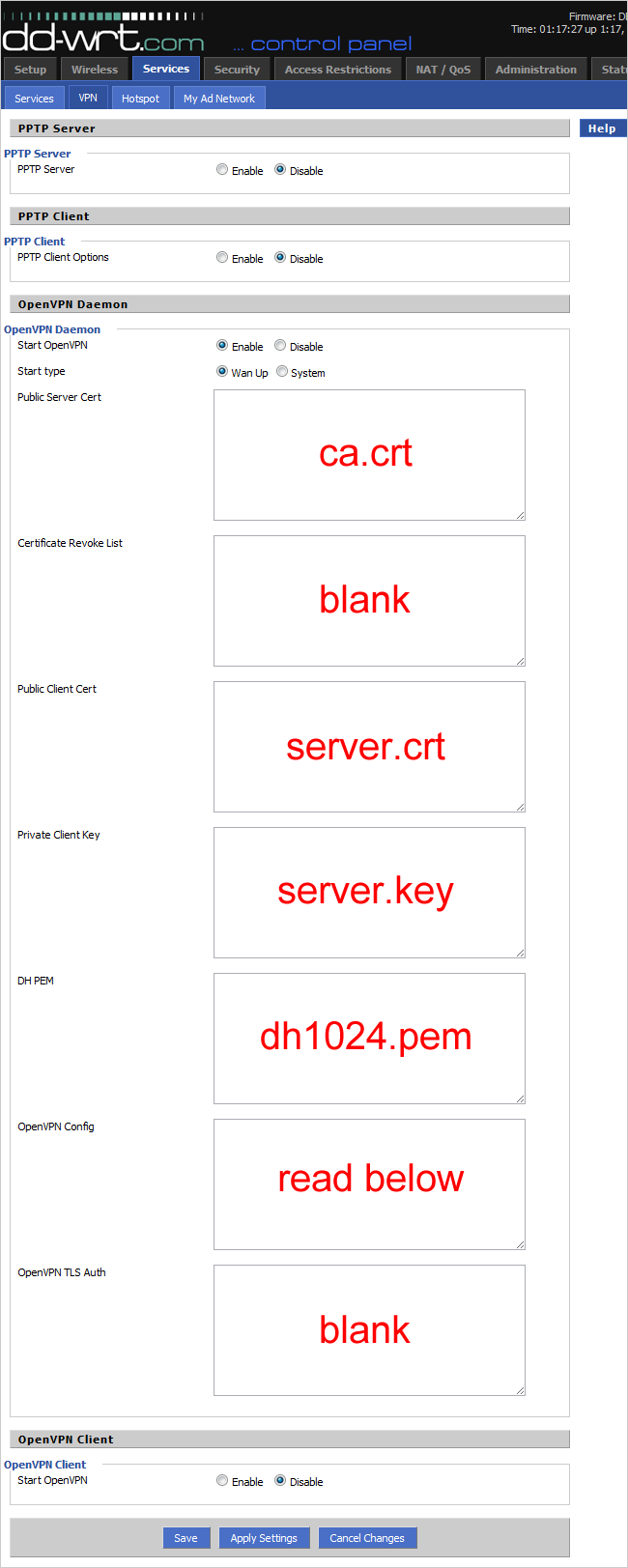
First, be sure to change Start type to "Wan Up" instead of the default "System". Now we're going to need our server keys and certificates we created earlier. In Windows Explorer, navigate to C:\Program Files (x86)\OpenVPN\easy-rsa\keys on 64-bit Windows 7 (or C:\Program Files\OpenVPN\easy-rsa\keys on 32-bit Windows 7). Open each corresponding file below (ca.crt, server.crt, server.key, and dh1024.pem) with Notepad or Notepad++ and copy the contents. Paste the contents in the corresponding boxes as seen below.
For the OpenVPN Config field, we will need to create a custom file. These settings will differ depending on how your LAN is set up. Open a separate browser window and type in your router's IP address. Click the Setup tab and take note of what IP address you have configured under Router IP > Local IP Address. The default, which is what we are using in this example, is 192.168.1.1. Paste this subnet right after "route" in the first line to reflect your LAN setup. Copy this into the OpenVPN Config box and click Save.
push "route 192.168.1.0 255.255.255.0"
server 10.8.0.0 255.255.255.0
dev tun0
proto tcp
keepalive 10 120
dh /tmp/openvpn/dh.pem
ca /tmp/openvpn/ca.crt
cert /tmp/openvpn/cert.pem
key /tmp/openvpn/key.pem
# Only use crl-verify if you are using the revoke list - otherwise leave it commented out
# crl-verify /tmp/openvpn/ca.crl
# management parameter allows DD-WRT's OpenVPN Status web page to access the server's management port
# port must be 5001 for scripts embedded in firmware to work
management localhost 5001
Now we must configure the firewall to allow clients to connect to our OpenVPN server via the 1194 port. Go to the Administration tab and click the Commands sub-tab. In the Commands text box paste the following:
iptables -I INPUT 1 -p udp --dport 1194 -j ACCEPT
iptables -I FORWARD 1 --source 192.168.1.0/24 -j ACCEPT
iptables -I FORWARD -i br0 -o tun0 -j ACCEPT
iptables -I FORWARD -i tun0 -o br0 -j ACCEPT
Be sure to change your LAN IP in the second line if it is different than the default. Then click the Save Firewall button below.
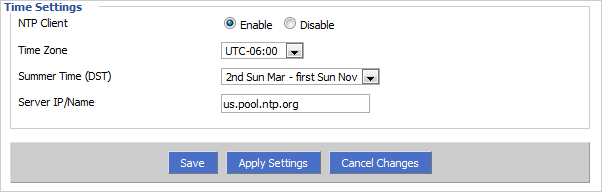
Finally, be sure to check your Time Settings under the Setup tab otherwise the OpenVPN daemon will deny all clients. We suggest going to TimeAndDate.com and searching for your city under Current Time. This website will give you all the information you need to fill in under Time Settings just like we did below. Also, check out the NTP Pool Project's website for public NTP servers to use.
Setting Up an OpenVPN Client
In this example we will be using a Windows 7 laptop as our client on a separate network. The first thing you'll want to do is install OpenVPN on your client like we did above in the first steps under Configuring OpenVPN. Then navigate to C:\Program Files\OpenVPN\config which is where we'll be pasting our files.
Now we have to go back on our original computer and collect a total of four files to copy over to our client laptop. Navigate to C:\Program Files (x86)\OpenVPN\easy-rsa\keys again and copy ca.crt, client1.crt, and client1.key. Paste these files in the client's config folder.
Finally, we need to copy one more file over. Navigate to C:\Program Files (x86)\OpenVPN\config and copy over the new client.ovpn file we created earlier. Paste this file in the client's config folder also.
Testing the OpenVPN Client
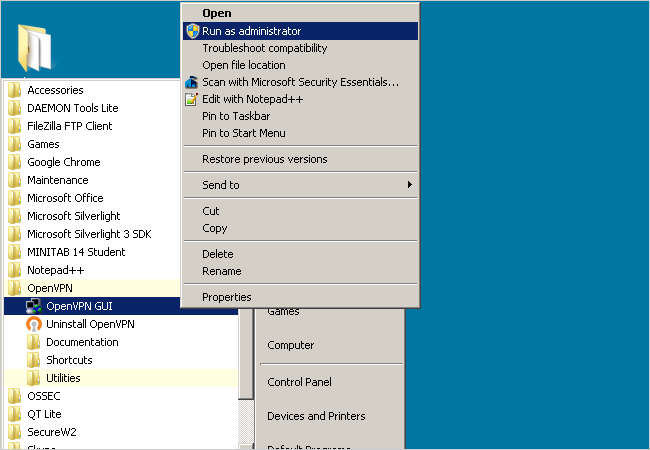
On the client laptop, click the Windows Start button and navigate to All Programs > OpenVPN. Right click on the OpenVPN GUI file and click Run as administrator. Note that you must always run OpenVPN as an administrator in order for it to work properly. To permanently set the file to always run as administrator, right click the file and click Properties. Under the Compatibility tab check Run this program as an administrator.
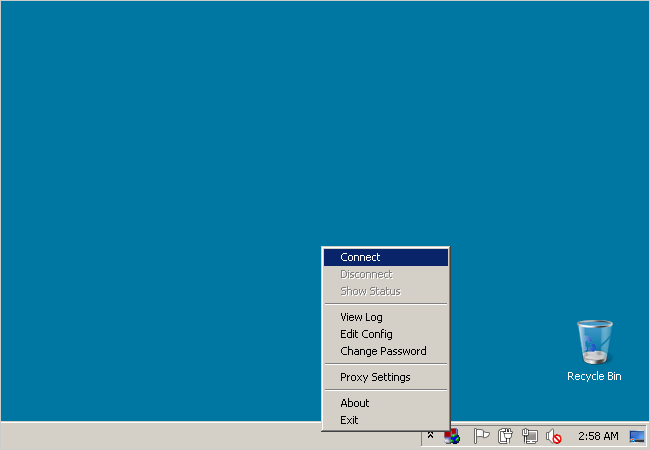
The OpenVPN GUI icon will appear next to the clock in the taskbar. Right click the icon and click Connect. Since we only have one .ovpn file in our config folder, OpenVPN will connect to that network by default.
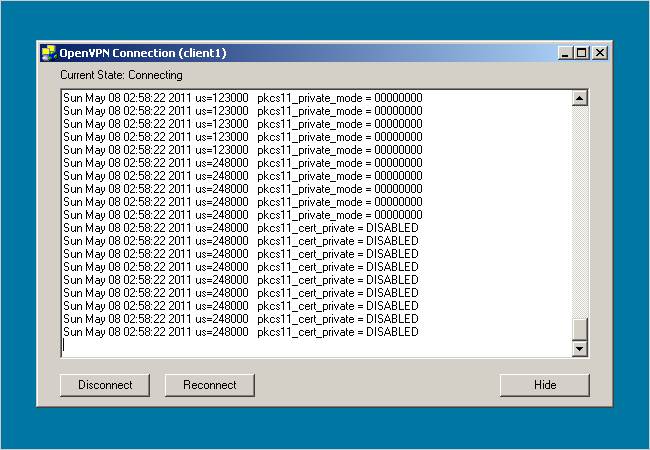
A dialog box will pop up displaying a connection log.
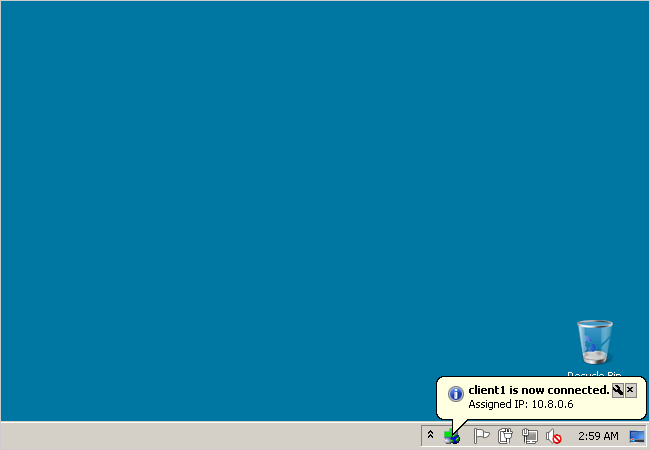
Once you're connected to the VPN, the OpenVPN icon in the taskbar will turn green and will display your virtual IP address.
And that's it! You now have a secured connection between your server and client's network using OpenVPN and DD-WRT. To further test the connection, try opening a browser on the client laptop and navigating to your DD-WRT router on the server's network.