Quick Links
If you've ever used a "Sign In With Facebook" button, or given a third-party app access to your Twitter account, you've used OAuth. It's also used by Google, Microsoft, and LinkedIn, as well as many other account providers. Essentially, OAuth allows you to grant a website access to some information about your account without giving it your actual account password.
OAuth for Signing In
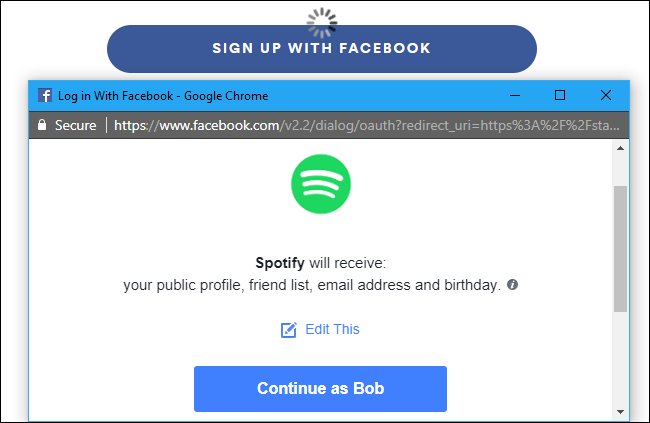
OAuth has two main purposes on the web at the moment. Often, it's used for creating an account and signing into an online service more conveniently. For example, rather than create a new username and password for Spotify, you can click or tap "Sign In With Facebook". The service checks to see who you are on Facebook and creates a new account for you. When you sign into that service in the future, it sees that you're sign in with the same Facebook account and gives you access to your account. You don't need to set up a new account or anything---Facebook authenticates you instead.
This is very different from simply giving the service your Facebook account password, however. The service never gets your Facebook account password or full access to your account. It can only view a few limited personal details, like your name and email address. It can't view your private messages or post on your Timeline.
Those "Sign In With Twitter", "Sign In With Google", "Sign In With Microsoft", "Sign In With LinkedIn", and other similar buttons for other websites work the same way, to
OAuth for Third-Party Applications
OAuth is also used when giving third-party apps access to accounts like your Twitter, Facebook, Google, or Microsoft accounts. It allows these third-party apps access to parts of your account. However, they never get your account password. Each application gets a unique access token that limits the access it has for your account. For example, a third-party application for Twitter may only have the ability to view your tweets, but not post new tweets. That unique access token can be revoked in the future, and only that specific app will lose access to your account.
As another example, you might give a third-party application access to only your Gmail emails, but restrict it from doing anything else with your Google account.
This is very different from simply giving a third-party application your account password and letting it sign in. The apps are limited in what they can do, and that unique access token means the account access can be revoked at any time without changing your main password and without revoking access from other apps.
How OAuth Works
You probably won't see the word "OAuth" appear whenever you're using it. Websites and apps will just ask you to sign in with your Facebook, Twitter, Google, Microsoft, LinkedIn, or other type of account.
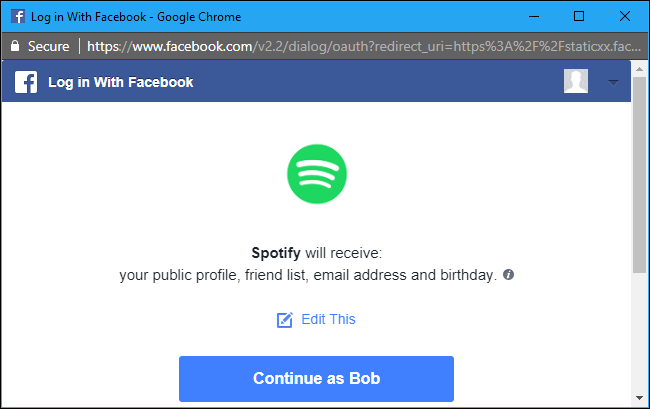
When you choose an account, you'll be directed to the account provider's website, where you'll have to sign in with that account if you aren't currently signed in. If you are signed in---great! You don't even have to enter a password.
Ensure you're actually directed to the real Facebook, Twitter, Google, Microsoft, LinkedIn, or whatever other service's website with a secure HTTPS connection before typing your password! This part of the process seems ripe for phishing, as malicious websites could pretend to be the real service's website in an attempt to capture your password.
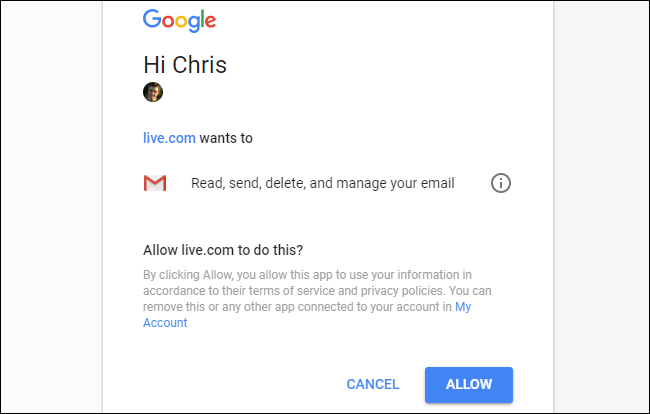
Depending on how the service works, you may just automatically be signed in with a bit of personal information, or you may see a prompt to give the application access to some of your account. You may even be able to choose which information you want to give the application access to.
Once you've given the app access, it's done. Your service of choice gives the website or application a unique access token. It stores that token and uses it to gain access to these details about your account in the future. Depending on the application, this may be used only to authenticate you when you sign in, or to automatically access your account and do things in the background. For example, a third-party application that scans your Gmail account may regularly access your emails so it can send you a notification if it finds something.
How to View and Revoke Access From Third-Party Applications
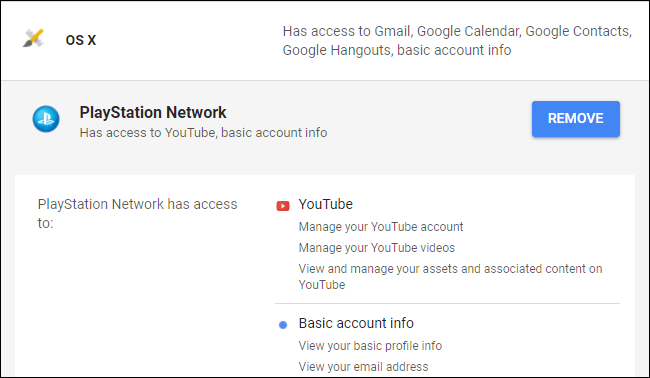
You can view and manage the list of third-party websites and applications that have access to your account on each account's website. It's a good idea to check these from time to time, as you may have once given access to your personal information to a service, stopped using it, and forgotten that service still has access. Limiting the services that have access to your account can help secure it and your private data.
For more detailed technical information about implementing OAuth, visit the OAuth website.