Quick Links
If you’ve ever missed an alarm because your phone unexpectedly rebooted in the middle of the night and wouldn’t start up until the correct PIN, pattern, or password was entered, Andorid Nougat's new Direct Boot is the answer.
Nougat's Direct Boot and File Encryption, Explained
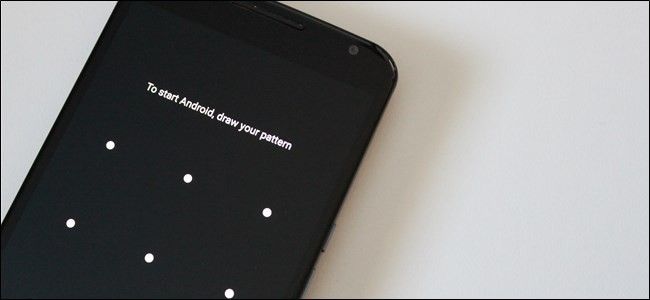
In previous versions of Android, Google used full-disk encryption to secure your device. That meant you had to enter the PIN or password every time your phone booted--or it wouldn't boot at all. So, if the phone reboots in the middle of the night, while in your bag, or some other scenario where you won’t see it for a while, you basically miss out on everything that happens—since the operating system isn’t technically loaded, it has no way to generate notifications. Instead, it just sits at full brightness (with no timeout!) waiting for your input…or to die. Whichever comes first. Man, that sounds grim.
It sounds great in theory, security-wise, but in practice, the above-mentioned scenario makes this method incredibly inconvenient. So, in Android Nougat, Google decided to add a new type of system encryption that it calls "File Encryption". This is comprised of two different types of data:
- Credential encrypted data: This data is protected and is only accessible once the device has been fully unlocked via PIN, pattern, or password. In practice, this acts similarly to full-disk encryption in terms of user experience.
- Device encrypted data: This is what’s new in Nougat. It makes certain non-personal data available to the operating system before the user inputs their unlock info. This includes generic system files needed to get the OS up and running in a usable state, allowing Nougat to boot up to the lock screen without any user interaction.
With this, developers can also push certain files into this encrypted space, allowing things like alarms, phone calls, and notifications to come through before the device has been fully unlocked. That means no accidentally sleeping in because your phone crashed and rebooted in the middle of the night.
When apps are allowed to run in this “device encrypted” state, they can push data to credential encrypted storage, but they can’t read it—it’s a one-way street. It’s in the developer’s hands as to what should be run at which level.
Android's file-based encryption is also known by a much simpler name: “Direct Boot”. This name, which doesn't really exist in Android's menus but was used at Google I/O with the announcement of Nougat, describes what the File Encryption feature means in practice: the phone is now allowed to boot directly into the operating system without the need for the user to input their security information.
How to Enable Nougat's New File Encryption
That all sounds great, right? You're probably itching to enable this right now, but there is a catch. If you've upgraded to Android 7.0, Direct Boot/File Encryption won’t be enabled default. If you buy a new phone with Android 7.0, then it will. Why? Because your current device is already using full-disk encryption, and this new method requires a full wipe in order to work. Bummer.
That said, there’s an easy way to quickly tell if you’re already using file-based encryption. Head to Settings > Security > Screen Lock and tap your current screen lock. If “require PIN to start device” is an option, you’re running full-disk encryption.
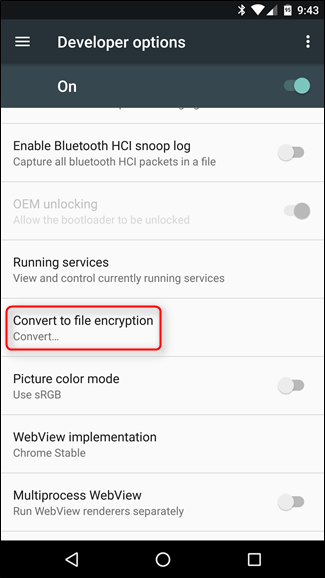
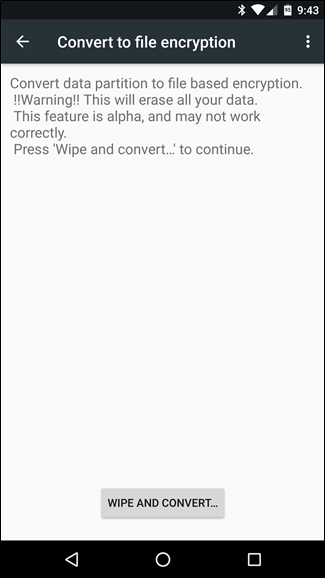
If you’d like to convert to file-based encryption, you can do so by enabling Developer Options, then heading into Developer Options and tapping the “Covert to file encryption” option. Keep in mind that this will erase all of your data, effectively factory resetting the device!
Lastly, it’s worth mentioning that if you’ve been running the beta version of Android N, then updated to the release version with an over-the-air update, the odds are you aren’t running file-based encryption, even if you performed a factory reset or did a clean install of the N beta. This, of course, depends on when you started running the beta—early adopters are probably still running the old full-disk encryption.
File-based encryption and Direct Boot are really nice solutions to an extremely irritating problem. The best part is that it requires very little interaction from the user—on new devices that will be running Nougat out of the box, this should all be the default. And the level of security provided hasn’t decreased in any way—all the important, personal data is still fully encrypted until unencrypted by the user.