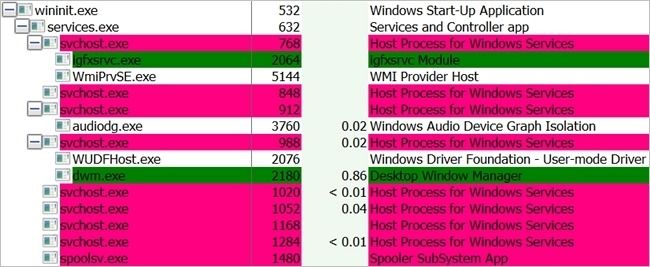
If you open up Task Manager or Process Explorer on your system, you will see many services running. But how much of an impact can a service have on your system, especially if it is 'corrupted' by malware? Today's SuperUser Q&A post has the answers to a curious reader's questions.
Today's Question & Answer session comes to us courtesy of SuperUser---a subdivision of Stack Exchange, a community-driven grouping of Q&A web sites.
The Question
SuperUser reader Forivin wants to know how much impact a service can have on a Windows system, especially if it is 'corrupted' by malware:
What kind malware/spyware could someone put into a service that does not have its own process on Windows? I mean services that use svchost.exe for example, like this:
Could a service spy on my keyboard input? Take screenshots? Send and/or receive data over the internet? Infect other processes or files? Delete files? Kill processes?
How much impact could a service have on a Windows installation? Are there any limits to what a malware 'corrupted' service could do?
The Answer
SuperUser contributor Keltari has the answer for us:
What is a service?
A service is an application, no more, no less. The advantage is that a service can run without a user session. This allows things like databases, backups, the ability to login, etc. to run when needed and without a user logged in.
What is svchost?
- According to Microsoft: "svchost.exe is a generic host process name for services that run from dynamic-link libraries". Could we have that in English please?
- Some time ago, Microsoft started moving all of the functionality from internal Windows services into .dll files instead of .exe files. From a programming perspective, this makes more sense for reusability...but the problem is that you can not launch a .dll file directly from Windows, it has to be loaded up from a running executable (exe). Thus the svchost.exe process was born.
So, essentially a service which uses svchost is just calling a .dll and can do pretty much anything with the right credentials and/or permissions.
If I remember correctly, there are viruses and other malware that do hide behind the svchost process, or name the executable svchost.exe to avoid detection.
Have something to add to the explanation? Sound off in the comments. Want to read more answers from other tech-savvy Stack Exchange users? Check out the full discussion thread here.