Some people's networked printers, cameras, routers, and other hardware devices are accessible from the Internet. There are even search engines designed to search such exposed devices. If your devices are secure, you won't have to worry about this.
Follow this guide to ensure your networked devices are properly isolated from the Internet. If you configure everything properly, people won't be able to find your devices by performing a search on Shodan.
Secure Your Router
On a typical home network -- assuming you don't have any other devices plugged directly into your modem -- your router should be the only device that's connected directly to the Internet. Assuming your router is correctly configured, it will be the only device that's accessible from the Internet. All other devices are connected to your router or its Wi-Fi network and are only accessible if the router allows them to be.
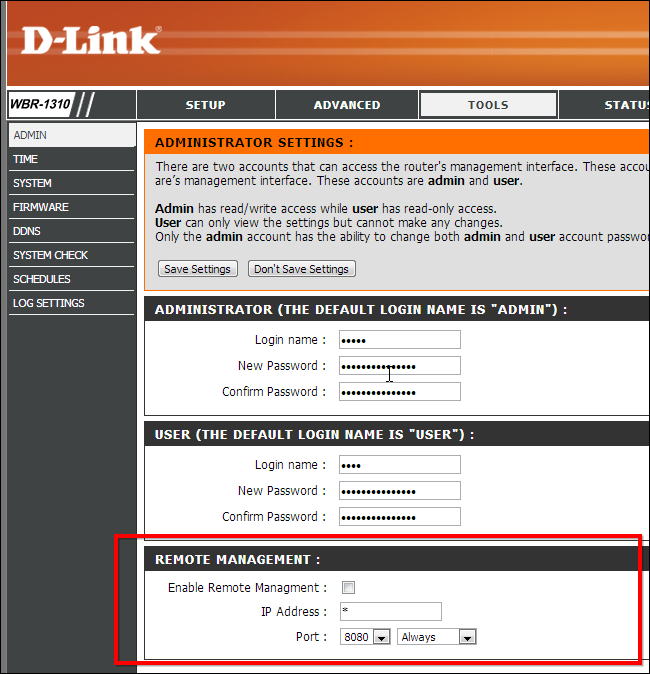
First things first: Ensure your router itself is secure. Many routers have "remote administration" or "remote management" features that allow you to log into your router from the Internet and configure its settings. The vast majority of people will never use such a feature, so you should ensure it's disabled -- if you have this feature enabled and have a weak password, an attacker may be able to log into your router remotely. You'll find this option in your router's web interface, if your router offers it. If you do need remote management, ensure you change the default password and, if possible, the username, too.
Many consumer routers have a serious security vulnerability. UPnP is an insecure protocol that allows devices on the local network to forward ports -- by creating firewall rules -- on the router. However, we previously covered a common security problem with UPnP -- some routers will accept UPnP requests from the Internet as well, allowing anyone on the Internet to create firewall rules on your router.
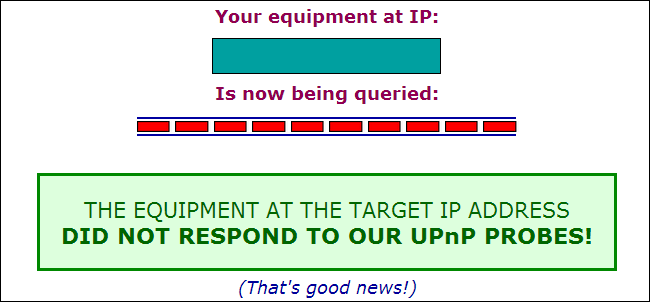
Check whether your router is vulnerable to this UPnP vulnerability by visiting the ShieldsUP! website and running the"Instant UPnP Exposure Test."
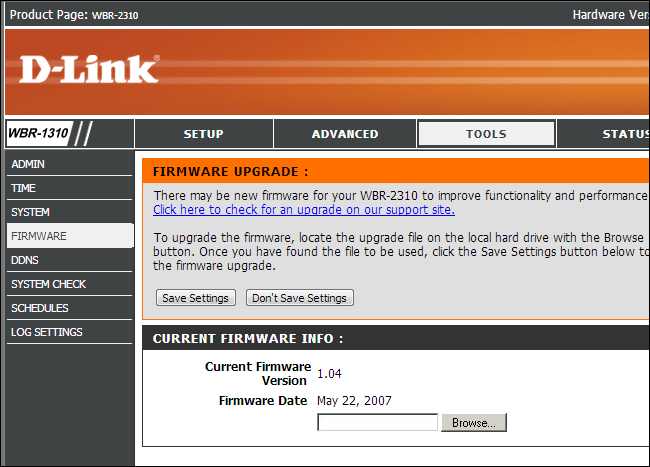
If your router is vulnerable, you may be able to fix this problem by updating it with the latest version of the firmware available from its manufacturer. If that doesn't work, you may want to try disabling UPnP in the router's interface or purchasing a new router that doesn't have this problem. Be sure to re-run the above test after updating the firmware or disabling UPnP to ensure your router is actually secure.
Ensure Other Devices Aren't Accessible
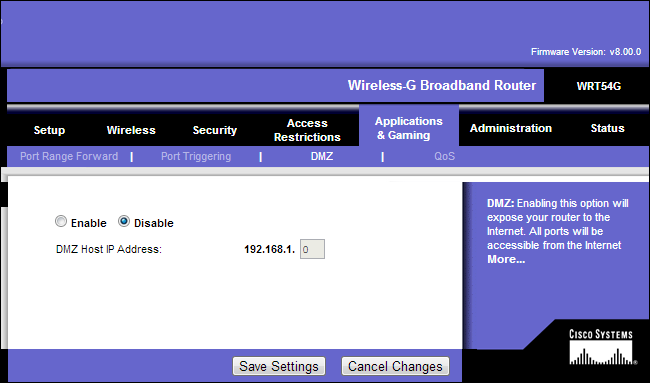
Ensuring your printers, cameras, and other devices aren't accessible over the Internet is fairly simple. Assuming these devices are behind a router and not directly connected to the Internet, you can control whether they're accessible from the router. If you're not forwarding ports to your networked devices or placing them in a DMZ, which exposes them entirely to the Internet, these devices will only be accessible from the local network.
You should also ensure that port-forwarding and DMZ features aren't exposing your computers or networked devices to the Internet. Only forward ports you actually need forwarded, and shy away from the DMZ feature -- a computer or device in the DMZ will receive all incoming traffic, as if it were connected directly to the Internet. This is a quick shortcut that avoids the need for port forwarding, but the DMZ'd device also loses the security benefits of being behind a router.
If you do want to make your devices accessible online -- maybe you want to log into a networked security camera's interface remotely and see what's going on in your house -- you should ensure they're set up securely. After forwarding ports from your router and making the devices accessible from the Internet, ensure they're set up with a strong password that isn't easily guessed. This may sound obvious, but the number of Internet-connected printers and cameras that have been exposed online shows that many people aren't password-protecting their devices.
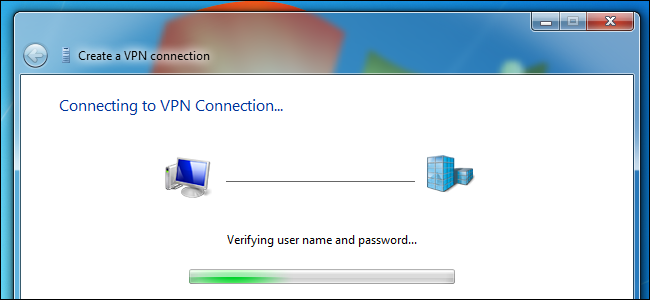
You may also want to consider not exposing such devices on the Internet and setting up a VPN instead. Rather than the devices being directly connected to the Internet, they're connected to the local network and you can remotely connect to the local network by logging into the VPN. You can secure a single VPN server more easily than you can secure several different devices with their own built-in web servers.
You can also try more creative solutions. If you only need to remotely connect to your devices from a single location, you could set up firewall rules on your router to ensure they can only be remotely accessed from a single IP address. If you want to share devices like printers online, you may want to try setting up something like Google Cloud Print rather than exposing them directly.
Be sure to keep your devices up-to-date with any firmware updates that include security fixes, too -- especially if they're exposed directly to the Internet.
Lock Down Your Wi-Fi
While you're at it, be sure to lock down your Wi-Fi networks. New network-connected devices -- from Google's Chromecast TV streaming device to Wi-Fi enabled light bulbs and everything in between -- generally treat your Wi-Fi network as a secure area. They allow any device on your Wi-Fi to access, use, and configure them. They do this for an obvious reason -- it's more user-friendly to treat all devices on the network as trusted than to prompt users for authentication in their own homes. However, this only works well if the local Wi-Fi network is actually secure. If your Wi-Fi isn't secure, anyone can connect and hijack your devices. They may also be able to browse any files you have shared on the network, too.
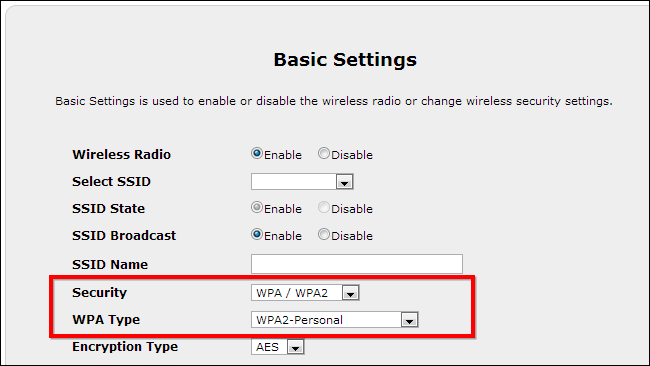
Be sure you have secure Wi-Fi encryption settings enabled on your home router. You should be using WPA2 encryption with a fairly strong passphrase -- ideally a reasonably long passphrase with numbers and symbols in addition to letters.
There are many other ways you could try to secure your home network -- from using WEP encryption to enabling MAC address filtering and hiding your wireless network -- but these don't offer much security. WPA2 encryption with a strong passphrase is the way to go.
When it all comes down to it, these are standard security precations. You just need to ensure your devices are up-to-date with the latest security patches, protected with strong passwords, and configured securely.
Pay particular attention to the networking -- the router shouldn't be set to expose devices on the Internet unless they're configured securely. Even then, you may want to connect to them remotely via a VPN for additional security or ensure they're only accessible from specific IP addresses.