Quick Links
In the last two articles, we looked at how to prepare your PC for network access. In this installment, we are going to look at wireless network configuration.
Be sure to check out the previous articles in this Geek School series on Windows 7:
- Introducing How-To Geek School
- Upgrades and Migrations
- Configuring Devices
- Managing Disks
- Managing Applications
- Managing Internet Explorer
- IP Addressing Fundamentals
- Networking
And stay tuned for the rest of the series all week.
Wireless networks allow computers to communicate without the use of cables. This is also commonly known as Wi-Fi. A connection is made from a device, which is usually a PC or a Laptop with a wireless card, to a Wireless Access Point (WAP), which acts as a bridge between the wireless network and the wired networks. Wireless network standards are specified by IEEE 802.11.
There are many flavors of 802.11, but we will only be concerned with four. Each increases the distance and speed of your wireless network.
|
Name |
Speed |
Distance |
Frequency |
|
802.11a |
54 Mbps |
30m |
5 GHz |
|
802.11b |
11 Mbps |
91m |
2.4 GHz |
|
802.11g |
54 Mbps |
91m |
2.4 GHz |
|
802.11n |
540 Mbps |
182m |
5 and 2.4 GHz |
Security Concerns
By default, wireless signals can be intercepted and read anyone within range. As such, it is always recommended that you use some form of encryption. Over time there has been many encryption standards:
- WEP - Wired Equivalent Privacy can be cracked and there are many tutorials on how to do it. For this reason, it has been superseded by stronger encryption techniques such as WPA2.
- TKIP - Temporal Key Integrity Protocol was designed by the IEEE and the Wi-Fi Alliance as a solution to replace WEP without requiring the replacement of legacy hardware. TKIP has also been cracked and you should choose a stronger algorithm where available.
- RADIUS - Remote Authentication Dial In User Service (RADIUS) is a network protocol often used by ISPs and larger enterprises to manage access to both the internet as well as internal networks. RADIUS is what you would use to secure your wireless networks in a corporate environment.
- WPA - The original WPA standard used TKIP, but was later replaced by WPA2 which uses a more secure AES-based algorithm. WPA is susceptible to brute force attacks when a weak passphrase is used. In most cases, WPA2 is the recommended option to use.
Connecting to a Wireless Network
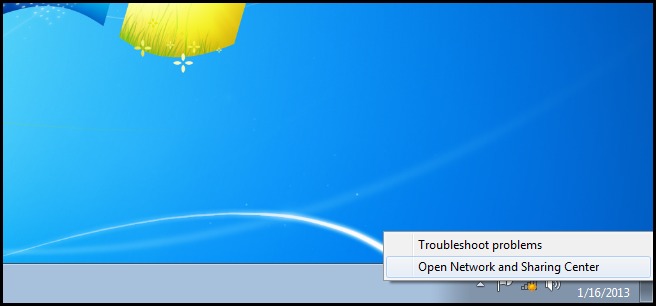
In the real world we just click on the wireless status icon and select the network we want to connect to, however the exam requires you to know how to connect to a wireless network through the Control Panel. To do that, you will need to open the Network and Sharing Center. This can be done by right clicking on the network connectivity status icon and selecting Open Network and Sharing Center from the context menu.
Then click on the Set up a new connection or network link.
Next you will want to select manually connect to a wireless network, then click next.
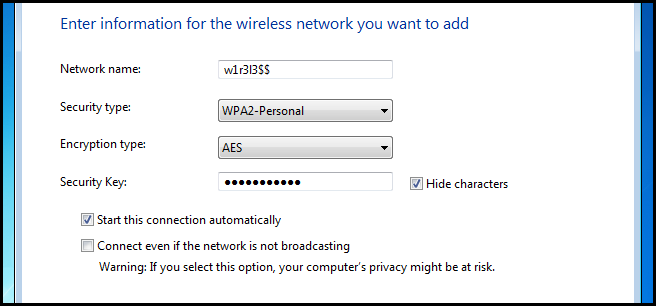
Next you will need to:
- Enter the SSID of your network
- Select the security type for your network
- Select the encryption scheme your network uses
- Then type in the password for the network
Once you have entered all that click next.
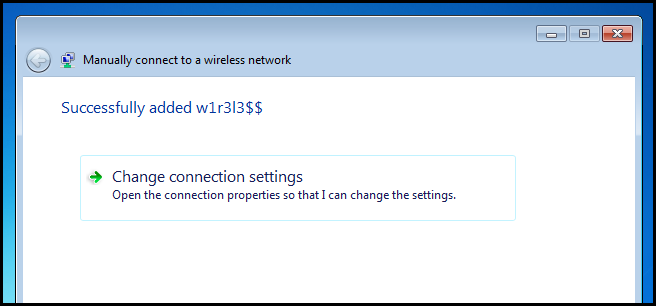
You should then get a message stating you have successfully added the network. At this point you can close the wizard.
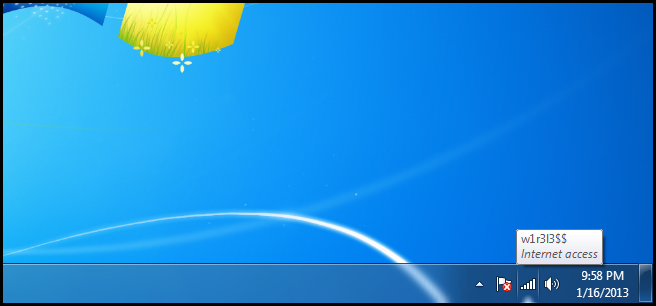
You should now see your wireless network status icon change to white and show you the signal strength.
Exporting Wireless Network Profiles
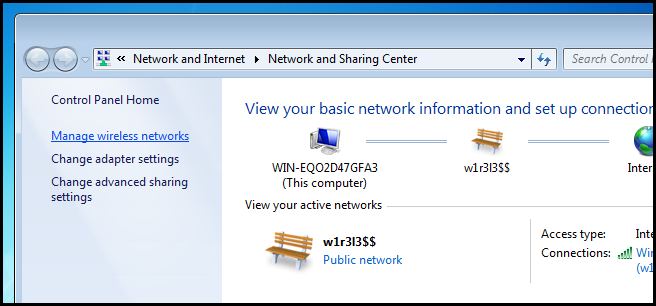
If you need to setup wireless network connectivity on multiple machines, you can export your wireless network profile to a file and import it on the other machines. To do that again open the Network and Sharing Center but this time click on the manage wireless networks link in the left hand pane.
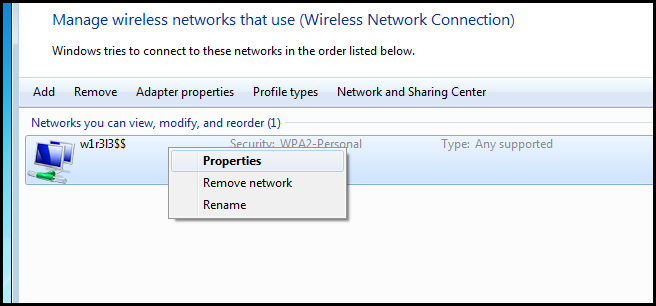
Then right click on the network you want to export and select Properties from the context menu.
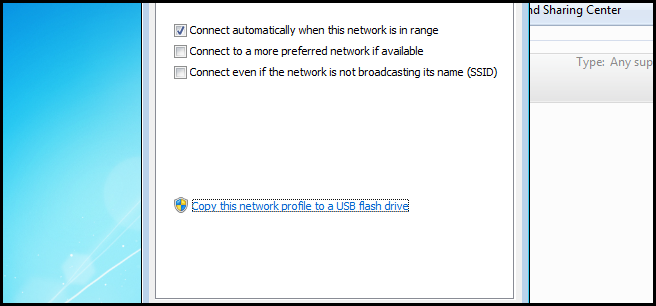
To export the network profile click on the link near the bottom of the dialog. If a USB is plugged in, a wizard will appear that will guide you through the remainder of the export process.
Importing a Wireless Network Profile
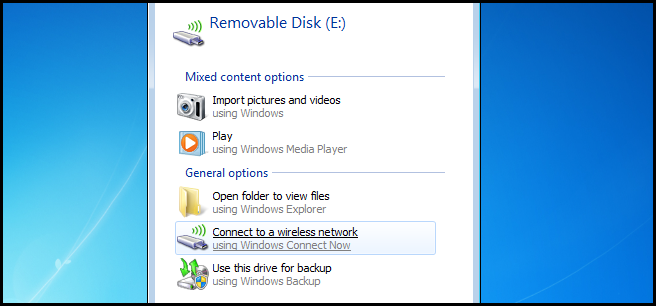
Once you have a network profile saved on a removable drive you will need to go to the other computer and insert the drive. When the auto play dialog opens, you will see a new option to connect to a wireless network. You will want to click on it.
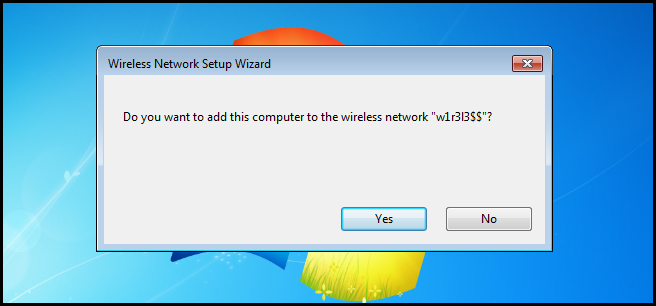
You will then be asked if you want to add the computer to the network. Clicking yes is all it takes to get connected.
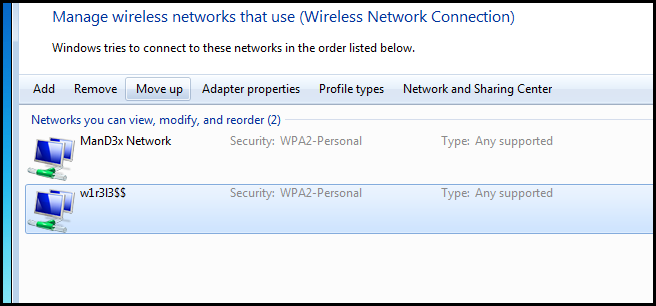
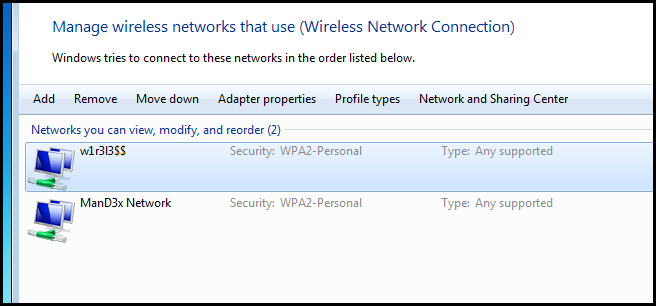
Setting a Preferred Wireless Network
If you are situated in an area that gets signal from more than one access point, you normally want to connect to the one that has a stronger signal. If you find yourself in a situation where Windows always connects to the weaker access point you can manually change the priority of the networks. To do this, open the Network and Sharing Center again.
Then click on the Manage wireless networks link in the left hand pane.
Now select the network with the strong signal and click the move up button.
That’s all there is to it.
Ad-Hoc Networks
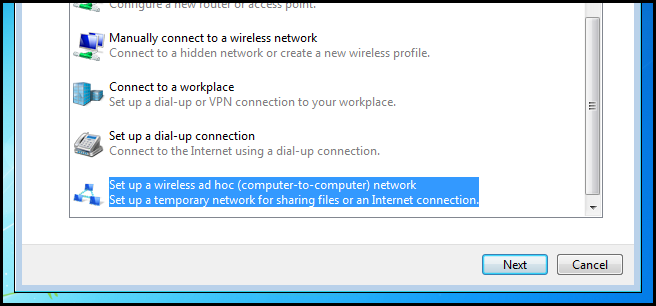
An 802.11 wireless network adapter can operate in two modes, Ad-Hoc and Infrastructure. Infrastructure mode is the way you have probably always used Wi-Fi, where you connect to an access point. In Ad-hoc mode your computers talk directly to each other and do not need an access point, however the computers have to be within 30m of each other. To create an ad-hoc network head into the network and sharing center and click on the set up a new connection or network link.
Then scroll all the way to the bottom and choose to setup an ad-hoc network, then click next.
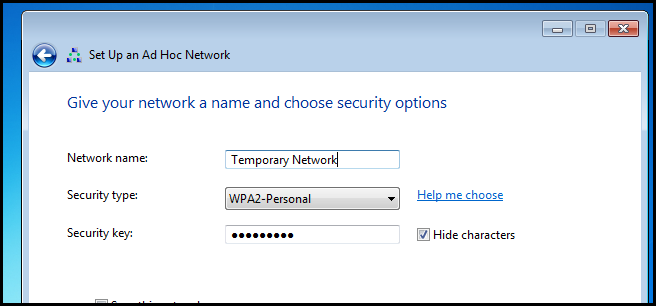
Next give your network a name and a password, then click next.
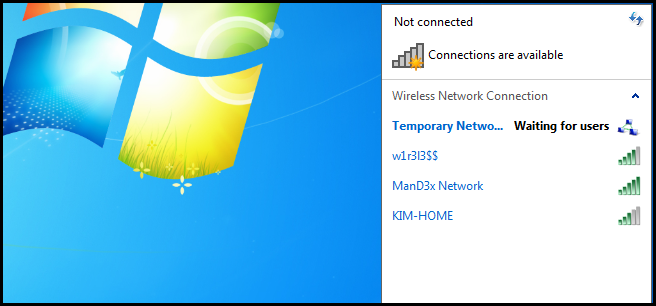
Once completed, users will be able to connect to the network just as they would an infrastructure based network.
Homework
- Find out how you could turn your PC into a wireless router, so that your other devices can share its internet connection. (Hint: The answer lies within the How-To Geek site.)
If you have any questions you can tweet me @taybgibb, or just leave a comment.