Quick Links
When you a delete a file, it isn't really erased -- it continues existing on your hard drive, even after you empty it from the Recycle Bin. This allows you (and other people) to recover files you've deleted.
If you're not careful, this will also allow other people to recover your confidential files, even if you think you've deleted them. This is a particularly important concern when you're disposing of a computer or hard drive.
Image Credit: Norlando Pobre on Flickr
What Happens When You Delete a File
Windows (and other operating systems) keep track of where files are on a hard drive through "pointers." Each file and folder on your hard disk has a pointer that tells Windows where the file's data begins and ends.
When you delete a file, Windows removes the pointer and marks the sectors containing the file's data as available. From the file system's point of view, the file is no longer present on your hard drive and the sectors containing its data are considered free space.
However, until Windows actually writes new data over the sectors containing the contents of the file, the file is still recoverable. A file recovery program can scan a hard drive for these deleted files and restore them. If the file has been partially overwritten, the file recovery program can only recover part of the data.
Note that this doesn't apply to solid-state drives (SSDs) -- see below for why.
Image Credit: Matt Rudge on Flickr
Why Deleted Files Aren't Erased Immediately
If you're wondering why your computer doesn't just erase files when you delete them, it's actually pretty simple. Deleting a file's pointer and marking its space as available is an extremely fast operation. In contrast, actually erasing a file by overwriting its data takes significantly longer. For example, if you're deleting a 10 GB file, that would be near-instantaneous. To actually erase the file's contents, it may take several minutes -- just as long as if you were writing 10 gigabytes of data to your hard drive.
To increase performance and save time, Windows and other operating systems don't erase a file's contents when it's deleted. If you want to erase a file's contents when it's deleted, you can use a "file-shredding" tool -- see the last section for more information.
Solid-State Drives Work Differently: None of this applies to solid state drives (SSDs). When you use a TRIM-enabled SSD (all modern SSDs support TRIM), deleted files are removed immediately and can't be recovered. Essentially, data can't be overwritten onto flash cells -- to write new data, the contents of the flash memory must first be erased. Your operating system erases files immediately to speed up write performance in the future -- if it didn't erase the file data immediately, the flash memory would first have to be erased before being written to in the future. This would make writing to an SSD slower over time.
Image Credit: Simon Wüllhorst on Flickr
Recovering Deleted Files
If you've accidentally deleted a file and need to get it back, there are some things you should bear in mind:
- You should recover the file as soon as possible: As Windows continues to write files to your hard drive, the chances of it overwriting the deleted files increases. If you want to be sure you can recover the file, you should perform a recovery immediately.
- You should try to use the hard drive as little as possible: The best way to recover a deleted file from a hard drive is powering the computer down immediately after the file is deleted, inserting the hard drive into another computer, and using an operating system running on another hard drive to recover it. If you try to recover a file by installing a file-recovery program on the same hard drive, the installation process and normal use of the hard drive can overwrite the file.
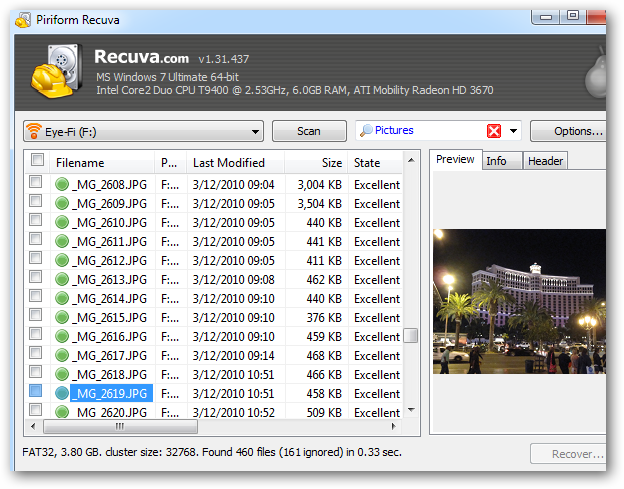
Windows doesn't include a built-in tool that scans your hard drive for deleted files, but there are a wide variety of third-party tools that do this. Recuva, made by the developers of CCleaner, is a good option. Recuva and other utilities can scan a hard drive for deleted files and allow you to recover them.
Preventing Deleted Files From Being Recovered
If you have confidential, private data on your computer, such as financial documents and other sensitive pieces of information, you may be worried that someone could recover your deleted files. If you're selling or otherwise disposing of a computer or hard drive, you should exercise caution.
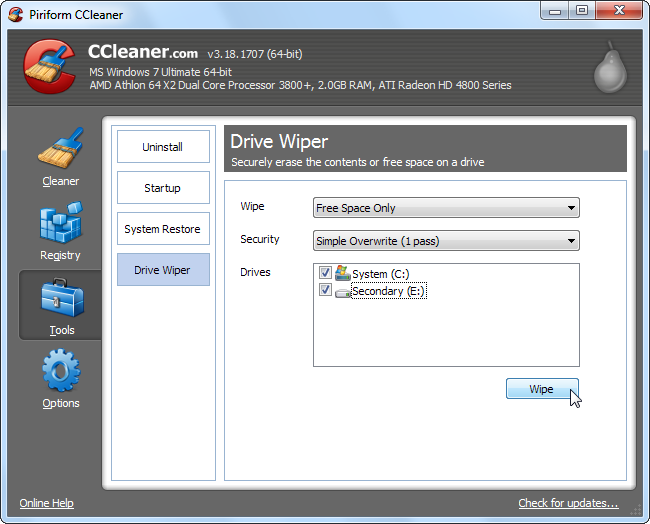
You can use a utility that automatically wipes your hard drive's free space -- by writing other data over the free space on your hard drive, all deleted files will be erased. For example, CCleaner's integrated Drive Wiper tool can do this.
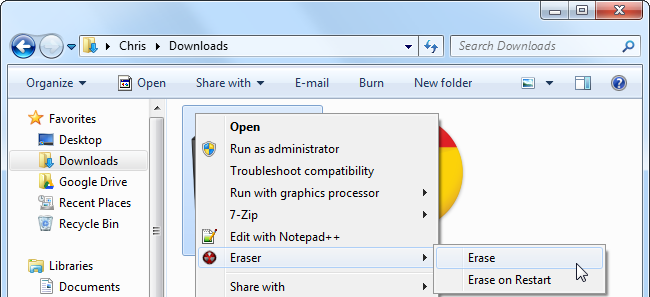
To make sure that a single file can't be recovered, you can use a "file-shredding" application such as Eraser to delete it. When a file is shredded or erased, not only is it deleted, but its data is overwritten entirely, preventing other people from recovering it. However, this may not always protect you -- if you made a copy of the file and deleted the original at some point, another deleted copy of the file may still be lurking around your hard disk.
Note that this process takes longer than deleting a file normally, so it's a bad idea to delete every file this way -- it's only necessary for confidential ones.
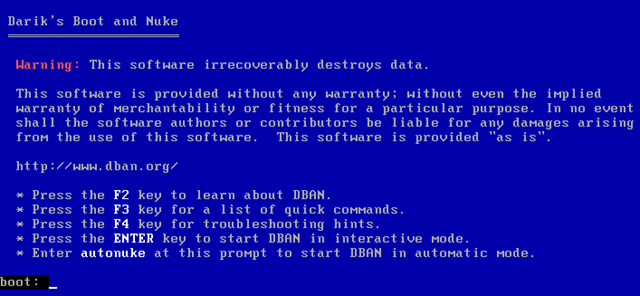
To really prevent someone from recovering any of your data, you can use a disk-wiping program, such as DBAN (Darik's Boot and Nuke.) Burn DBAN to a CD, boot from it, and it will erase everything from your hard drive, including your operating system and all your personal files, overwriting them with useless data. This is very useful when getting rid of a computer -- it helps you ensure all your personal data is erased.
While some people think that files can still be recovered after they're overwritten, the evidence shows us that one wipe should be good enough.
You should now understand why deleted files can be recovered and when they can't. Remember this when getting rid of a computer or hard drive -- your confidential files may still be present on your hard drive if you haven't properly erased them.