On Linux, the Root user is equivalent to the Administrator user on Windows. However, while Windows has long had a culture of average users logging in as Administrator, you shouldn’t log in as root on Linux.
Microsoft tried to improve Windows security practices with UAC – you shouldn’t log in as root on Linux for the same reason you shouldn’t disable UAC on Windows.
Why Ubuntu Uses Sudo
Discouraging users from running as root is one of the reason why Ubuntu uses sudo instead of su. By default, the root password is locked on Ubuntu, so average users can’t log in as root without going out of their way to re-enable the root account.
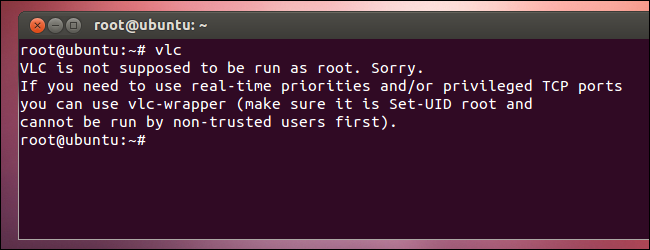
On other Linux distributions, it’s historically been possible to log in as root from the graphical login screen and get a root desktop, although many applications may complain (and even refuse to run as root, as VLC does). Users coming from Windows sometimes decided to log in as root, just as they used the Administrator account on Windows XP.
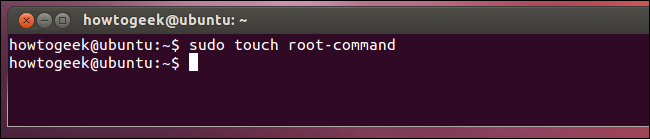
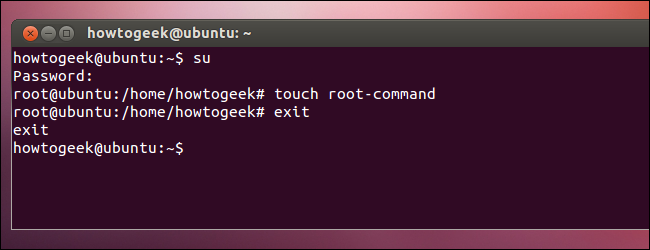
With sudo, you run a specific command (prefixed by sudo) that gains root privileges. With su, you’d use the su command to gain a root shell, where you’d run the command you want to use before (hopefully) exiting the root shell. Sudo helps enforce best practices, running only commands that need to be run as root (such as software installation commands) without leaving you at a root shell where you may stay logged in or run other applications as root.
Limiting The Damage
When you log in as your own user account, programs you run are restricted from writing to the rest of the system – they can only write to your home folder. You can’t modify system files without gaining root permissions. This helps keep your computer secure. For example, if the Firefox browser had a security hole and you were running it as root, a malicious web page would be able to write to all files on your system, read files in other user account’s home folders, and replace system commands with compromised ones. In contrast, if you’re logged in as a limited user account, the malicious web page wouldn’t be able to do any of those things – it would only be able to inflict damage in your home folder. While this could still cause problems, it’s much better than having your entire system compromised.
This also helps protect you against malicious or just plain buggy applications. For example, if you run an application that decides to delete all files it has access to (perhaps it contains a nasty bug), the application will wipe our your home folder. This is bad, but if you have backups (which you should!), it’s fairly easy to restore the files in your home folder. However, if the application had root access, it could delete every single file on your hard drive, necessitating a full reinstall.
Fine-Grained Permissions
While older Linux distributions ran entire system administration programs as root, modern Linux desktops use PolicyKit for even more fine-grained control of the permissions an application receives.
For example, a software-management application could be granted only permission to install software on your system through PolicyKit. The program’s interface would run with the limited user account’s permissions, only the part of the program that installed software would receive elevated permissions – and that part of the program would only be able to install software.
The program wouldn’t have full root access to your entire system, which could protect you if a security hole is found in the application. PolicyKit also allows limited user accounts to make some system administration changes without obtaining full root access, making it easier to run as a limited user account with less hassle.
Linux will let you log into a graphical desktop as root -- just as it will allow you to delete every single file on your hard drive while your system is running or write random noise directly to your hard drive, obliterating your file system – but it isn’t a good idea. Even if you know what you’re doing, the system isn’t designed to be run as root – you’re bypassing much of the security architecture that makes Linux so secure.