Quick Links
Like most things on Linux, the sudo command is very configurable. You can have sudo run specific commands without asking for a password, restrict specific users to only approved commands, log commands run with sudo, and more.
The sudo command’s behavior is controlled by the /etc/sudoers file on your system. This command must be edited with the visudo command, which performs syntax-checking to ensure you don’t accidentally break the file.
Specify Users With Sudo Permissions
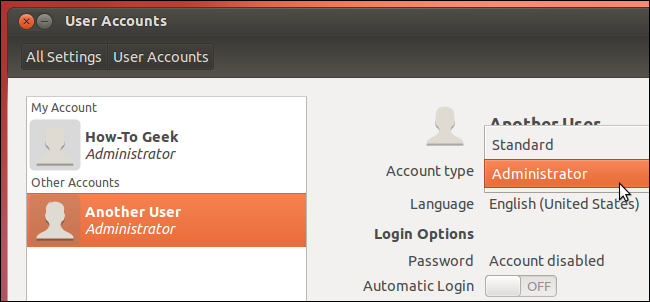
The user account you create while installing Ubuntu is marked as an Administrator account, which means it can use sudo. Any additional user accounts you create after installation can be either Administrator or Standard user accounts – Standard user accounts don’t have sudo permissions.
You can control user account types graphically from Ubuntu’s User Accounts tool. To open it, click your user name on the panel and select User Accounts or search for User Accounts in the dash.
Make Sudo Forget Your Password
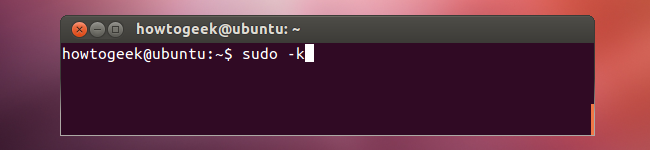
By default, sudo remembers your password for 15 minutes after you type it. This is why you only have to type your password once when executing multiple commands with sudo in quick succession. If you’re about to let someone else use your computer and you want sudo to ask for the password when it runs next, execute the following command and sudo will forget your password:
sudo –k
Always Ask For a Password
If you’d rather be prompted each time you use sudo – for example, if other people regularly have access to your computer -- you can disable the password-remembering behavior entirely.
This setting, like other sudo settings, is contained in the /etc/sudoers file. Run the visudo command in a terminal to open the file for editing:
sudo visudo
In spite of its name, this command defaults to the new-user-friendly nano editor instead of the traditional vi editor on Ubuntu.
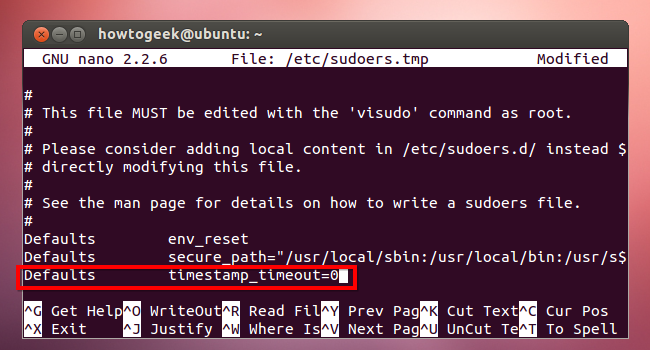
Add the following line below the other Defaults lines in the file:
Defaults timestamp_timeout=0
Press Ctrl+O to save the file, and then press Ctrl+X to close Nano. Sudo will now always prompt you for a password.
Change the Password Timeout
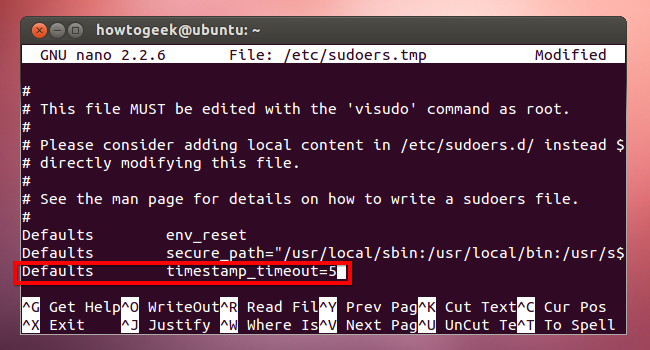
To set a different password timeout – either a longer one like 30 minutes or a shorter one like 5 minutes – follow the steps above but use a different value for timestamp_timeout. The number corresponds to the number of minutes sudo will remember your password for. To have sudo remember your password for 5 minutes, add the following line:
Defaults timestamp_timeout=5
Never Ask for a Password
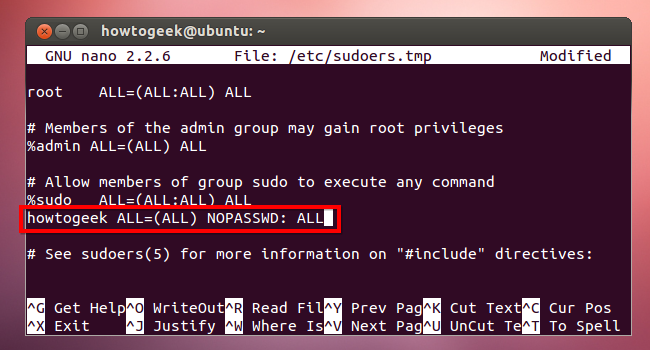
You can also have sudo never ask for a password – as long as you’re logged in, every command you prefix with sudo will run with root permissions. To do this, add the following line to your sudoers file, where username is your username:
username ALL=(ALL) NOPASSWD: ALL
You can also change the %sudo line – that is, the line that allows all users in the sudo group (also known as Administrator users) to use sudo – to have all Administrator users not require passwords:
%sudo ALL=(ALL:ALL) NOPASSWD:ALL
Run Specific Commands Without a Password
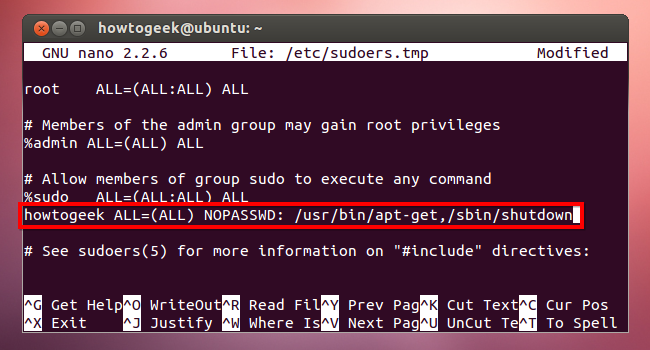
You can also specify specific commands that will never require a password when run with sudo. Instead of using “ALL” after NOPASSWD above, specify the location of the commands. For example, the following line will allow your user account to run the apt-get and shutdown commands without a password.
username ALL=(ALL) NOPASSWD: /usr/bin/apt-get,/sbin/shutdown
This can be particularly useful when running specific commands with sudo in a script.
Allow a User to Run Only Specific Commands
While you can blacklist specific commands and prevent users from running them with sudo, this isn’t very effective. For example, you could specify that a user account not be able to run the shutdown command with sudo. But that user account could run the cp command with sudo, create a copy of the shutdown command, and shut down the system using the copy.
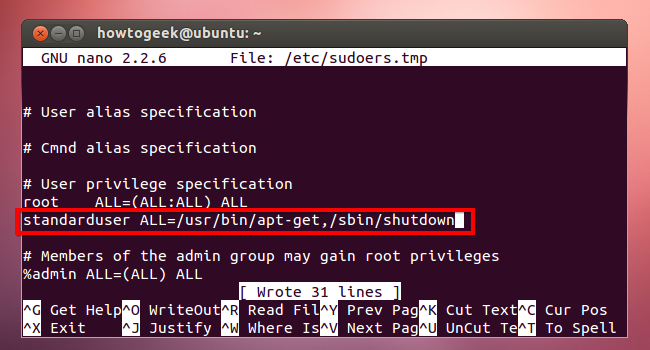
A more effective way is to whitelist specific commands. For example, you could give a Standard user account permission to use the apt-get and shutdown commands, but no more. To do so, add the following line, where standarduser is the user’s username:
standarduser ALL=/usr/bin/apt-get,/sbin/shutdown
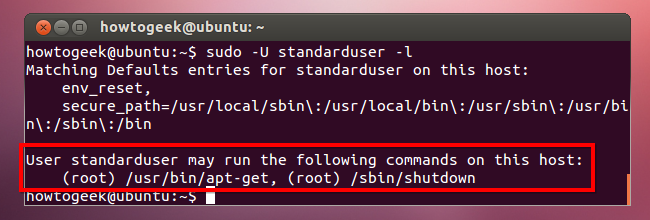
The following command will tell us what commands the user can run with sudo:
sudo -U standarduser –l
Logging Sudo Access
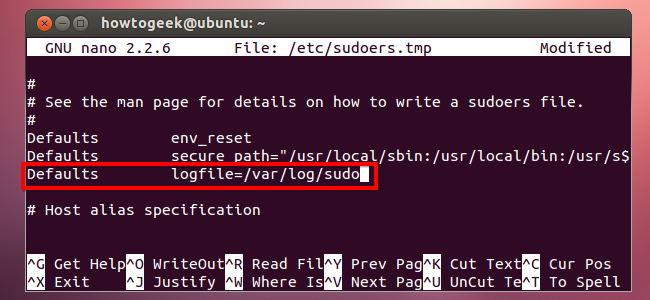
You can log all sudo access by adding the following line. /var/log/sudo is just an example; you can use any log file location you like.
Defaults logfile=/var/log/sudo
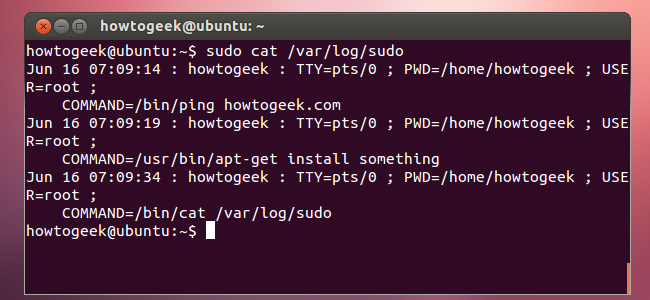
View the contents of the log file with a command like this one:
sudo cat /var/log/sudo
Bear in mind that, if a user has unrestricted sudo access, that user has the ability to delete or modify the contents of this file. A user could also access a root prompt with sudo and run commands that wouldn't be logged. The logging feature is most useful when coupled with user accounts that have restricted access to a subset of system commands.