Quick Links
You've probably heard that you need to overwrite a drive multiple times to make the data unrecoverable. Many disk-wiping utilities offer multiple-pass wipes. This is an urban legend -- you only need to wipe a drive once.
Wiping refers to overwriting a drive with all 0's, all 1's, or random data. It's important to wipe a drive once before disposing of it to make your data unrecoverable, but additional wipes offer a false sense of security.
Image Credit: Norlando Pobre on Flickr
What Wiping Does
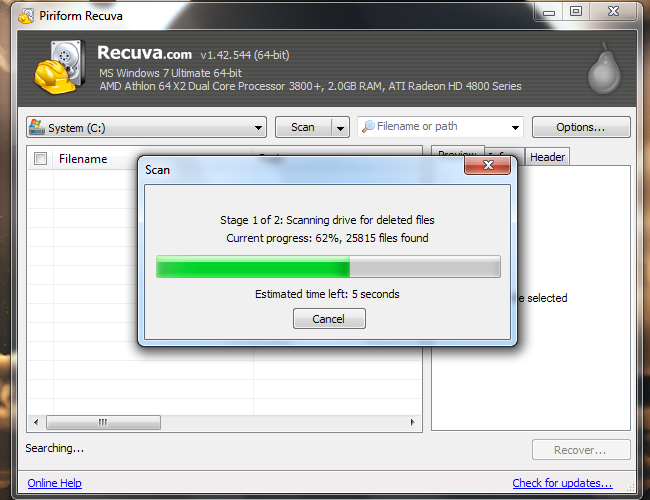
When you delete a file using Windows, Linux, or another operating system, the operating system doesn't actually remove all traces of the file from your hard drive. The operating system marks the sectors containing the data as "unused." The operating system will write over these unused sectors in the future. However, if you run a file-recovery utility, you can recover data from these sectors, assuming they haven't been overwritten yet.
Why doesn't the operating system delete the data completely? That would take additional system resources. A 10 GB file can be marked as unused very quickly, while it would take much longer to write over 10 GB of data on the drive. It doesn't take any longer to overwrite a used sector, so there's no point in wasting resources overwriting the data -- unless you want to make it unrecoverable.
When you "wipe" a drive, you overwrite all data on it with 0's, 1's, or a random mix of 0's and 1's.
Mechanical Hard Drives vs. Solid State Drives
The above is only true for traditional, mechanical hard drives. Newer solid state drives supporting the TRIM command behave differently. When an operating system deletes a file from an SSD, it sends a TRIM command to the drive, and the drive erases the data. On a solid state drive, it takes longer to overwrite a used sector rather than writing data to an unused sector, so erasing the sector ahead of time increases performance.
Image Credit: Simon Wüllhorst on Flickr
This means that file-recovery tools won't work on SSDs. You also shouldn't wipe SSDs -- just deleting the files will do. SSDs have a limited number of write cycles, and wiping them will use up write cycles with no benefit.
The Urban Legend
On a traditional mechanical hard disk drive, data is stored magnetically. This has led some people to theorize that, even after overwriting a sector, it may be possible to examine each sector's magnetic field with a magnetic force microscope and determine its previous state.
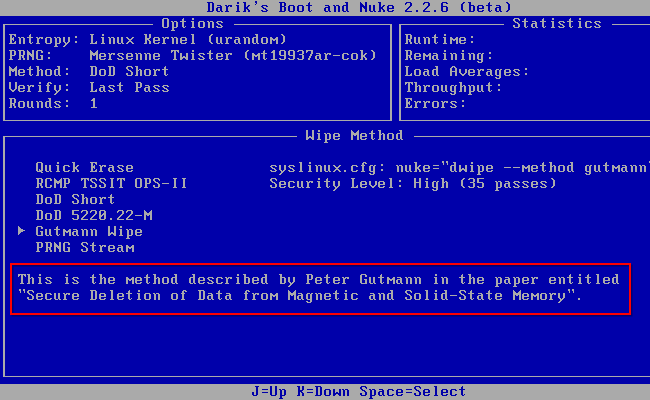
As a solution, many people advise writing data to the sectors multiple times. Many tools have built-in settings to perform up to 35 write passes -- this is known as the "Gutmann method," after Peter Gutmann, who wrote an important paper on the subject -- "Secure Deletion of Data from Magnetic and Solid-State Memory," published in 1996.
In fact, this paper was misinterpreted and become the source of the 35-pass urban legend. The original paper ends with the conclusion that:
"Data overwritten once or twice may be recovered by subtracting what is expected to be read from a storage location from what is actually read... However by using the relatively simple methods presented in this paper the task of an attacker can be made significantly more difficult, if not prohibitively expensive."
Given that conclusion, it's pretty obvious that we should use the Gutmann method to erase our drives, right? Not so fast.
The Reality
To understand why the Gutmann method isn't necessary for all drives, it's important to note that the paper and method were designed in 1996, when older hard drive technology was in use. The 35-pass Gutmann method was designed to wipe data from any type of drive, no matter what type of drive it was -- everything from current hard disk technology in 1996 to ancient hard disk technology.
As Gutmann himself explained in an epilogue written later, for a modern drive, one wipe (or maybe two, if you like -- but certainly not 35) will do just fine (the bolding here is mine):
"In the time since this paper was published, some people have treated the 35-pass overwrite technique described in it more as a kind of voodoo incantation to banish evil spirits than the result of a technical analysis of drive encoding techniques... In fact performing the full 35-pass overwrite is pointless for any drive since it targets a blend of scenarios involving all types of (normally-used) encoding technology, which covers everything back to 30+-year-old MFM methods (if you don't understand that statement, re-read the paper). If you're using a drive which uses encoding technology X, you only need to perform the passes specific to X, and you never need to perform all 35 passes. For any modern PRML/EPRML drive, a few passes of random scrubbing is the best you can do. As the paper says, "A good scrubbing with random data will do about as well as can be expected". This was true in 1996, and is still true now. "
Disk density is also a factor. As hard disks have gotten bigger, more data has become packed into smaller and smaller areas, making theoretical data recovery essentially impossible:
"...with modern high-density drives, even if you've got 10KB of sensitive data on a drive and can't erase it with 100% certainty, the chances of an adversary being able to find the erased traces of that 10KB in 200GB of other erased traces are close to zero."
In fact, there have been no reported case of anyone using a magnetic force microscope to recover overwritten data. The attack remains theoretical and confined to older hard disk technology.
Beyond Wiping
If you're still paranoid after reading the above explanations, there are a few ways you can go further. Performing 35 passes won't help, but you can use a degausser to eliminate the drive's magnetic field -- this may destroy some drives, though. You can also physically destroy your hard disk -- this is the real "military-grade" data destruction.
Image Credit: U.S. Army Environmental Command on Flickr