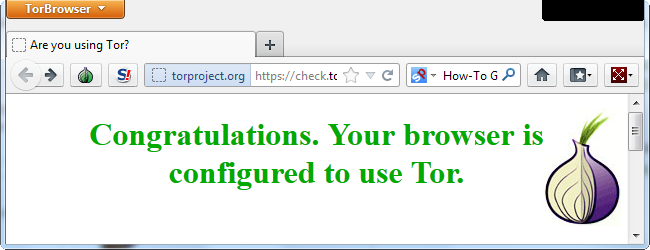
Everything you do online can be traced back to your IP address. Even if you're accessing encrypted websites, networks can see the websites you're accessing -- and the websites themselves know your IP address. Use the Tor network to browse with anonymity.
Tor is an encrypted network that can route your traffic through relays, making the traffic appear to come from exit nodes. Unlike with proxies, the exit node itself doesn't know your IP address or where you are.
How Tor Works
When you use a Tor client, your Internet traffic is routed through Tor's network. The traffic travels through several randomly selected relays (run by volunteers), before exiting the Tor network and arriving at your destination. This prevents your Internet service provider and people monitoring your local network from viewing the websites you access. It also prevents the websites themselves from knowing your physical location or IP address -- they'll see the IP address and location of the exit node instead. Even the relays don't know who requested the traffic they're passing along. All traffic within the Tor network is encrypted.
Image Credit: The Tor Project, Inc.
For example, let's say you access Google.com through Tor. Your Internet service provider and local network operator can't see that you're accessing Google.com -- they just see encrypted Tor traffic. The Tor relays pass your traffic along until it eventually reaches an exit node. The exit node talks to Google for you -- from Google's perspective, the exit node is accessing their website. (Of course, traffic can be monitored at the exit node if you're accessing an unencrypted website.) The exit node passes the traffic back along the relays, and the relays don't know where it ends up.
Tor offers anonymity and a path through Internet censorship and monitoring -- people living under repressive regimes with censored Internet connections can use Tor to access the wider Internet without fear of reprisal. Whistleblowers can use Tor to leak information without their traffic being monitored and logged.
It's not a great idea to use Tor for normal browsing, though. While the architecture does a good job of offering anonymity, browsing through Tor is significantly slower than browsing normally.
If you want more detailed information about how Tor works, check out the Tor Project's website.
Tor Browser Bundle
The Tor Project recommends the Tor Browser Bundle as the safest, easiest way to use Tor. The Tor Browser Bundle is a customized, portable version of Firefox that comes preconfigured with the ideal settings and extensions for TOr. You can use Tor with other browsers and browser configurations, but this is likely to be unsafe. For example, Flash and other browser plug-ins can reveal your IP address -- the Tor Browser Bundle disables plug-ins for you and provides a safe environment, so you don't have to worry about your browser settings. It also includes the EFF's HTTPS Everywhere extension, which enables HTTPS on websites with HTTPS support. HTTPS provides encryption between the exit node and destination website.
Tor recommends that you not download document files, such as DOC and PDF files, and open them in external applications. The external application can connect to the Internet to download additional resources, exposing your IP address.
Getting Started
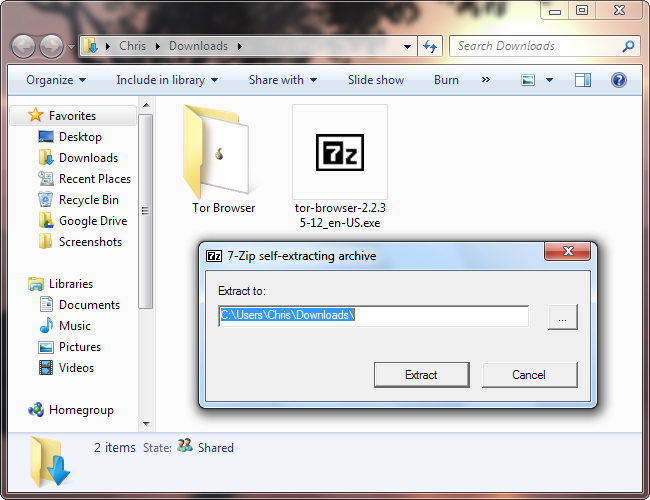
After downloading the Tor Browser Bundle, double-click the downloaded EXE file and extract it to your hard drive. The Tor Browser Bundle requires no installation, so you can extract it to a USB stick and run it from there.
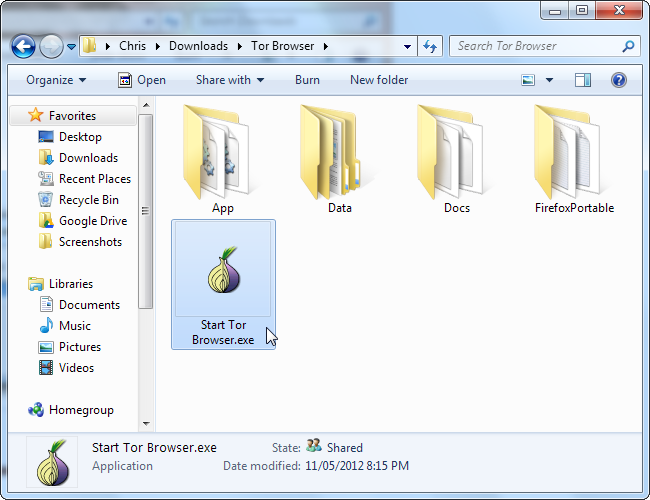
Launch the Start Tor Browser.exe file in the Tor Browser folder.
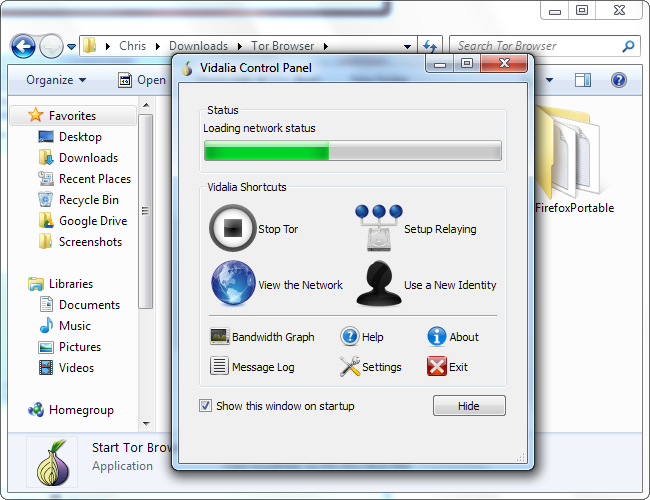
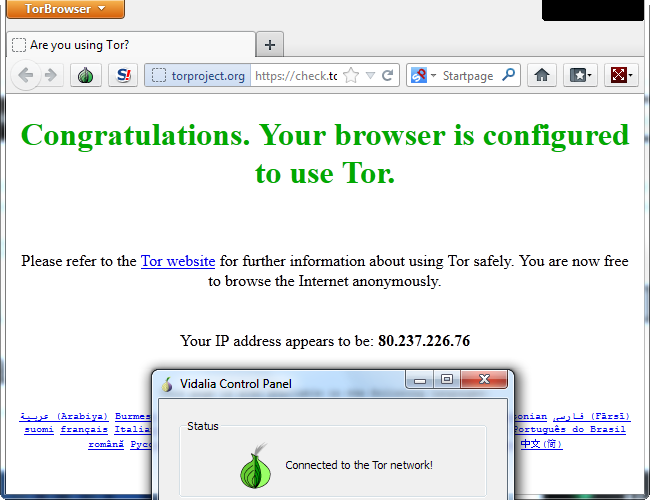
The EXE file will launch Vidalia, which connects to the Tor network. After connecting, Vidalia will automatically open Tor's customized Firefox browser.
Vidalia automatically launches the Tor Browser once it connects. When you close the browser, Vidalia automatically disconnects from Tor and closes.
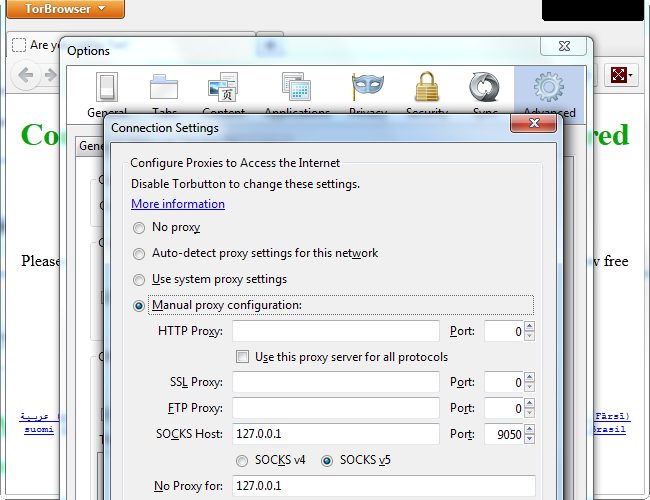
Vidalia creates a local proxy on your system. The Tor Browser Bundle is configured to route all your traffic through it by default, as we can see here in the Tor Browser's connection settings window. You can configure other programs to access Tor through the proxy, but they may reveal your IP address in other ways.
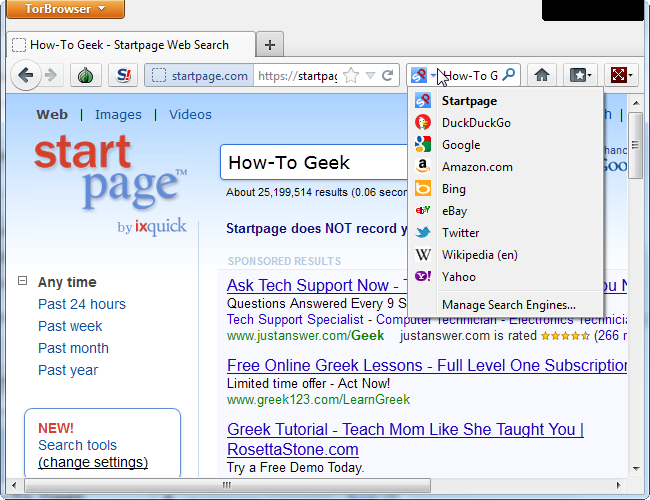
Use the Tor Browser to browse the web just as you would with a normal browser. It's pre-configured with Startpage and DuckDuckGo, search engines that respect your privacy.
Remember not to provide any personal information -- say, by logging into an account associated with you -- while using the Tor browser, or you'll lose the anonymity.