Quick Links
Have you ever wanted to have that special "dorm knock" with your router, as to have it only "open the door" when the secret knock has been recognized? How-To Geek explains how to install the Knock daemon on DD-WRT.
Image by Bfick and Aviad Raviv
If you haven't already, be sure and checkout previous articles in the series:
- Turn Your Home Router Into a Super-Powered Router with DD-WRT
- How To Install Additional Software On Your Home Router (DD-WRT)
- How to Remove Advertisements with Pixelserv on DD-WRT
Assuming you are familiar with those topics, keep reading. Keep in mind that this guide is a little more technical, and beginners should be careful when modding their router.
Overview
Traditionally, in order to be able to communicate with a device/service one would have to initiate a full network connection with it. However doing so exposes, what is called in the security age, an attack surface. The Knock daemon is a kind of a network sniffer that can react when a pre-configured sequence is observed. As a connection does not have to be established in order for the knock daemon to recognize a configured sequence, the attack surface is reduced while maintaining the desired functionality. In a sense, we will precondition the router with a desired "two bits" response (unlike poor Roger...).
In this article we will:
- Show how to use Knockd to have the router Wake-On-Lan a computer on your local network.
- Show how to trigger the Knock sequence from an Android application, as well as a computer.
Note: While the installation instructions are no longer relevant, you could watch the movie series I've created "way back when", to see the entire rundown of configuring to knocking. (Just excuse the crude presentation).
Security implications
The discussion about "how secure is Knockd?", is long and dates back many a millenia (in internet years) but the bottom line is this:
Knock is a layer of security by obscurity, that should only be used to enhance other means like encryption and should not be used on it's own as an end all be all security measure.
Prerequisites, Assumptions & Recommendations
- It is assumed that you have an Opkg enabled DD-WRT router.
- Some patience as this may take "a while" to setup.
- It is highly recommended that you obtain a DDNS account for your external (usually dynamic) IP.
Lets get cracking
Installation & Basic configuration
Install the Knock daemon by opening a terminal to the router and issuing:
opkg update ; opkg install knockd
Now that Knockd is installed we need to configure the triggering sequences and commands that will be executed once they are triggered. To do this, open the "knockd.conf" file in a text editor. On the router this would be:
vi /opt/etc/knockd.conf
Make its content look like:
[options]
logfile = /var/log/knockd.log
UseSyslog[wakelaptop]
sequence = 56,56,56,43,43,43,1443,1443,1443
seq_timeout = 30
command = /usr/sbin/wol aa:bb:cc:dd:ee:22 -i $( nvram get lan_ipaddr | cut -d . -f 1,2,3 ).255
tcpflags = sync
Lets explain the above:
- The "options" segment allows one to configure global parameters for the daemon. In this example we've instructed the daemon to keep a log both in the syslog and in a file. While it doesn't harm using both options in conjunction, you should consider keeping just one of them.
- The "wakelaptop" segment, is an example of a sequence that will trigger the WOL command to your LAN for a computer with the MAC address of aa:bb:cc:dd:ee:22.Note: The command above, assumes the default behavior of having a class C subnet.
To add more sequences, simply copy & paste the "wakelaptop" segment and adjust with new parameters and/or commands to be executed by the router.
Startup
To have the router invoke the daemon on startup, append the below to the "geek-init" script from the OPKG guide:
knockd -d -c /opt/etc/knockd.conf -i "$( nvram get wan_ifname )"
This will start the Knock daemon on the "WAN" interface of your router, so that it will listen to packets from the internet.
Knock from Android
In the age of portability its almost imperative to "have an app for that"... so StavFX created one for the task :)
This app performs the knocking sequences right from your Android device and it supports creating widgets on your home screens.
- Install the Knocker application from the Android market (also please be kind and give it a good rating).
-
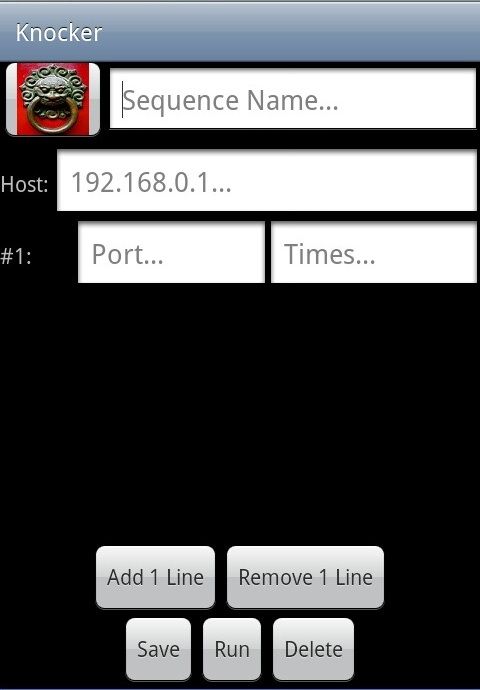
Once installed on your device, launch it. You should be greeted by something like:
-
You may long press the example icon to edit it, or click "menu" to add a new entry. A new entry would look like:
-
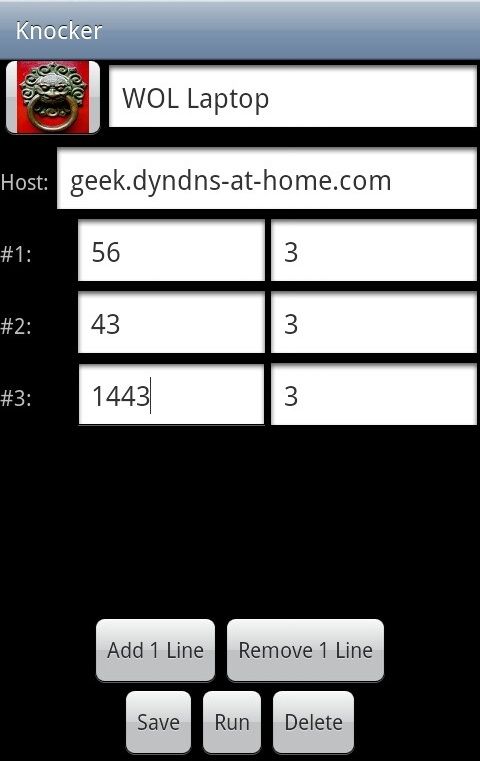
Add lines and fill the information required for your Knocking. For the example WOL configuration from above this would be:
- Optionally change the icon by long pressing the icon next to the Knock name.
- Save the Knock.
- Single tap the new Knock in the main screen to activate it.
- Optionally create a widget for it on a home screen.
Keep in mind that while we've configured the example configuration file with groups of 3 for each port (because of the Telnet section below), with this application there is no restriction on the amount of repeats (if at all) for a port.
Have fun using the app that StavFX has donated :-)
Knock from Windows/Linux
While it is possible to perform the Knocking with the simplest of network utility a.k.a "Telnet", Microsoft has decided that Telnet is a "security risk" and subsequently no longer install it by default on modern windows. If you ask me "They that can give up essential liberty to obtain a little temporary safety, deserve neither liberty nor safety. ~Benjamin Franklin" but i digress.
The reason we set the example sequence to groups of 3 for each port, is that when telnet is unable to connect to the desired port, it will automatically try again 2 more times. This means that telnet will actually knock 3 times before giving up. So all we have to do is execute the telnet command once for each port in the port group. It is also the reason a 30 seconds timeout interval has been selected, as we have to wait for telnet's timeout for each port until we execute the next port-group. It is recommended that when you've finished with the testing phase, that you automate this procedure with a simple Batch/Bash script.
Using our example sequence this would look like:
- If your on windows, follow the MS instruction to install Telnet.
- Drop to a command line and issue:telnet geek.dyndns-at-home.com 56telnet geek.dyndns-at-home.com 43telnet geek.dyndns-at-home.com 1443
If all went well, that should be it.
Troubleshooting
If your router doesn't react to sequences, here are a couple of troubleshooting steps you may take:
-
View the log - Knockd will keep a log you can view in real time to see if the knocking sequences have arrived to the daemon and if the command has been executed correctly.Assuming you are at least using the log-file as in the example above, to see it in real-time, issue in a terminal:
tail -f /var/log/knockd.log - Be mindful of firewalls - Sometimes your ISP, workplace or internet cafe, take the liberty of blocking communication for you. In such a case, while your router may be listening, the knocks on ports that are blocked by any part of the chain, will not reach the router and it will have a hard time reacting to them. That is why it is recommended to try combinations that use the well known ports such as 80, 443, 3389 and so on before trying more random ones. Again, you may view the log to see what ports do reach the router's WAN interface.
-
Try the sequences internally - Before involving the above complexity that other parts of the chain may introduce, it is recommended that you try to execute the sequences internally to see that they A. hit the router like you think they should B. execute the command/s as expected. To accomplish this, you may start Knockd while bound to your LAN interface with:
knockd -d -i "$( nvram get lan_ifnameq )" -c /opt/etc/knockd.conf - Remember which side your on - It is not possible to Knock the WAN interface from the LAN interface in the above configuration. If you would like to be able to knock no matter "what side your on" you can simply run the demon twice, Once bound to the WAN as in the article and once bound to the LAN as in the debugging step from above. There is no problem running both in conjunction by simply appending the command from above to the same geek-init script.
Remarks
While the above example could be accomplished by various other methods, we hope that you can use it to learn how to accomplish more advance things.
A part two to this article that hides the VPN service behind a knock is coming, so stay tuned.